Pharming through Multimedia Messaging
Today we received the notification of a malicious code called 04_00_53_mensaje.exe that propagated by email using the following message:

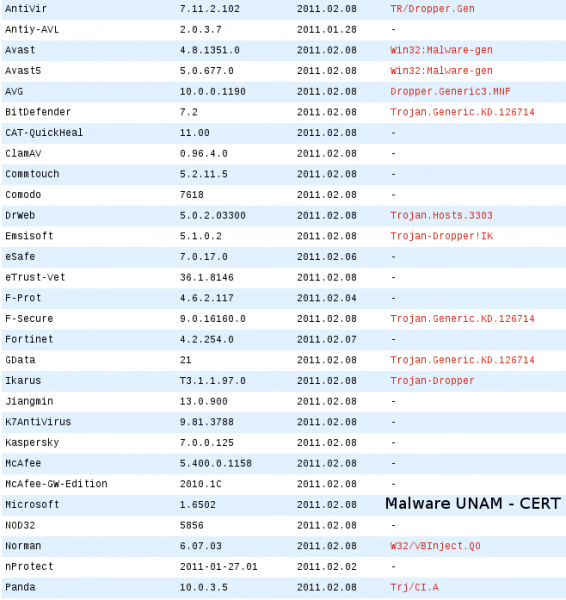
By the time of analysis it was recognized as a threat only by these antivirus engines:

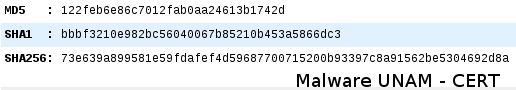
Its digital signatures are shown below:
When executed, it copied itself to C:\Windows\ with the name scssrr.exe, from where it started a process that made DNS queries to resolve the domain nuevo.chickenkiller.com.

The result of this query was the IP used for the pharming, after modifying the file C:/WINDOWS/System32/drivers/etc/hosts.
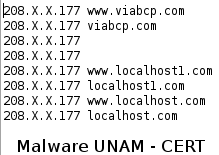
On our analysis lab, we modified the host file manually with the information shown above and consulted the site www.viabcp.com, after which we were redirected to a phishing site of a Peruvian bank.

On previous occasions, we have found that the author of a malicious code started up an HTTP server on the infected computer and modified the hosts file, redirecting the victim to localhost. For this sample, a phishing site of a bank was maintained and when the user opened the browser, a redirection to the user’s own computer took place. The information theft was carried out from a specific web page via JavaScript.
Unfortunately, on this occasion we could not determine whether another redirection to steal the user’s data took place, due to the link in section "Access to your accounts" wasn’t activated or the site wasn’t finished.