Likejacking: Kidnap of "Like", new propagation method in Facebook
On April 12th, the security company Sophos published on its blog a report about a new scam campaign (fraud) that has been propagating through Facebook with the message:
“Dad walks in on daughter... EMBARRASING!!!"
We decided to investigate if this threat was still active and, to our surprise, after several days of being public, it was still available and referenced a site unrelated to Facebook.
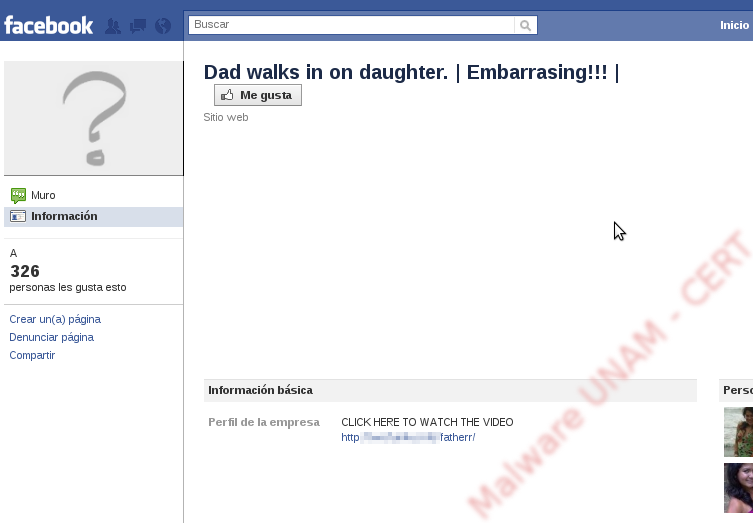
When we followed the link, it loaded a site on a different window and with the same title as the Facebook page (“Dad walks in on daughter… EMBARRASIN!!”), with an image that represents a YouTube video before being played.
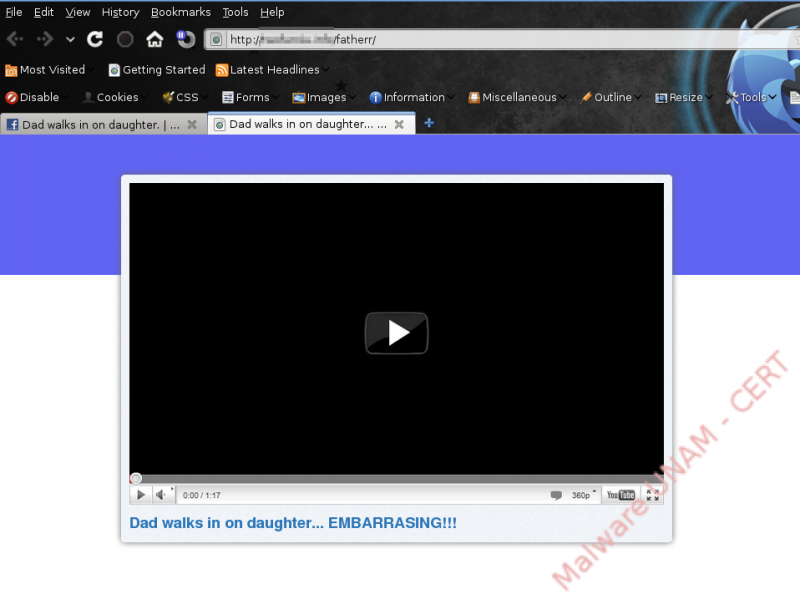
The interesting thing, and precisely the goal of this kind of attack, is that when the user tries to play the video either by clicking on the “button” in the middle or on the one situated at the bottom left corner, what the user is actually doing is clicking a “Like” button embedded on the site and hidden behind the image.
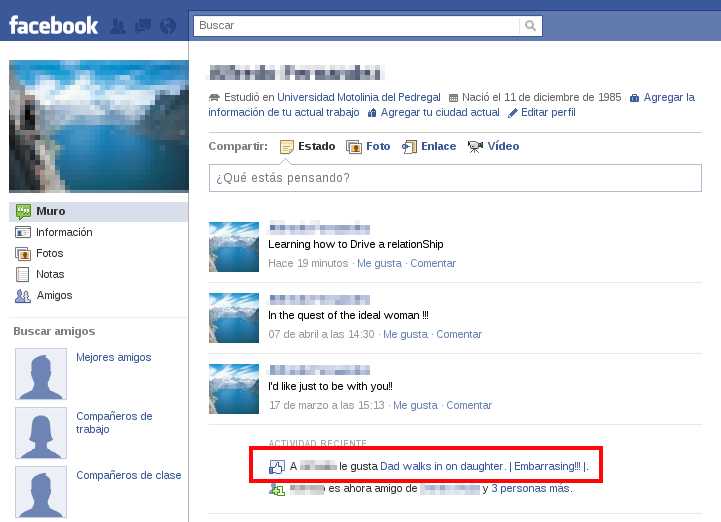
As a result, the user’s profile shows the action taken, that is “Liking” the malicious site. This is the way this attack spreads, given that any of our “friends” can see the message, and if they’re curious enough, they can be tricked by the same scam. The best course of action is to eliminate the post as soon as possible.
Afterwards, on the malicious site, a window pops up asking the user to complete a survey to verify his/her age before being allowed to watch the video.
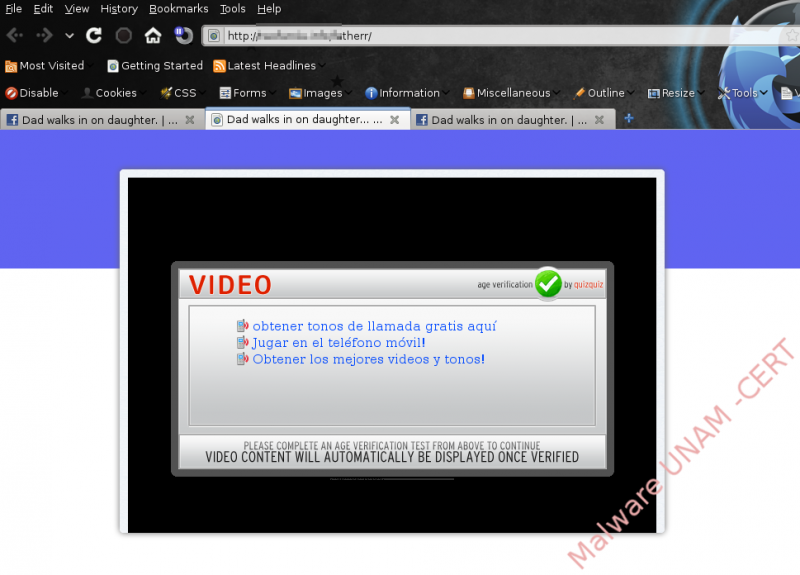
When clicking any of the links, the user is redirected to a site that asks for a cell phone number in order to get a password that will allow the user to obtain what was advertised on the link. In this case, we clicked on the link that advertised ring tones.

This technique, which is not new, is based on what is known as “click kidnapping”, clickjacking [2] or UI redressing (user interface correction) in which the attacker, somehow, generates a fake visual layer above an existing website, so that the only change made to the website is how the user sees the content and its behavior or functionality remains the same.
In our example the visual layer, that is the one the user interacts with (or believes to be interacting with) appears to be an non played YouTube video; while the real website (lower layer or the hidden layer) is the one containing the “Like” buttons and it’s actually the one with which the user is, unknowingly, interacting.
One the next image the “lower layer”, that contains all the “like” buttons, is shown.
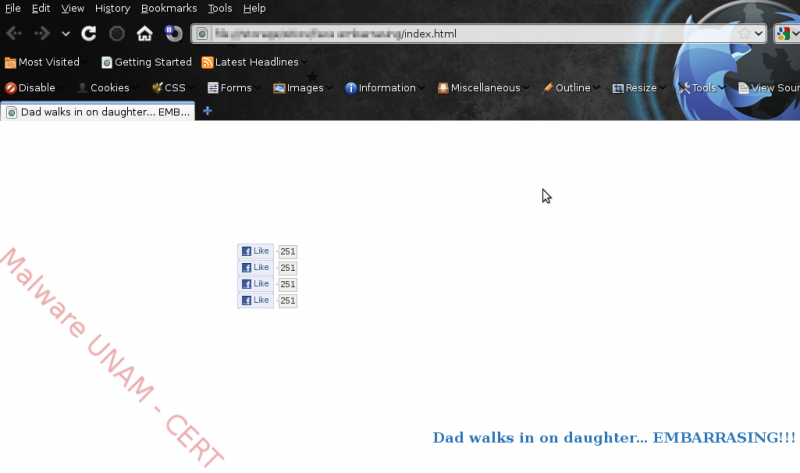
Next to the buttons, we can clearly see the number of people that have “liked” the content, which at that time was 251. Whereas on the first image of this entry, that shows the latest count at the time of writing this report, the number of people had increased to 326.
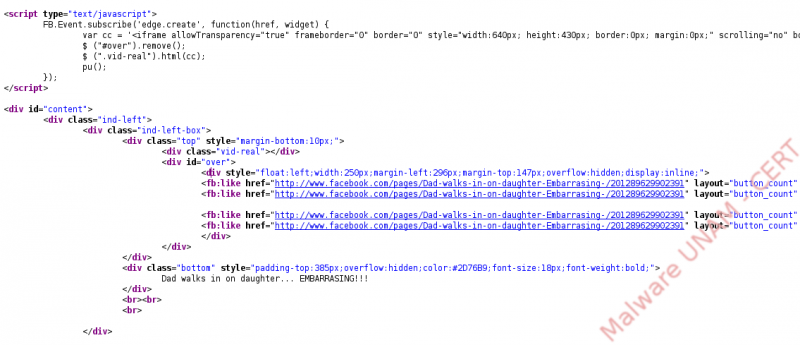
Finally, when reviewing the source code of the website, we found out that the author was using the API developed by Facebook, to create his/her interface. On February 18th we published a report explaining this fact.
In regards with the website of the allegedly video, the creator was using a method called FB.Event.subscribeto handle events through edge.create, a global event that activates when the user “Likes” something and that is used through the label fb:like. When the user makes the previous request (unconsciously), is when the propagating message is posted on the user’s wall.
Even though these attacks could be considered as not so dangerous, the impact that they could have is quite big because it affects a great number of users and the economic profit for the creators may ascend to thousands of dollars.
It is important to consider that if you encounter this kind of scams: you must not click on the “survey” links, you must delete the post immediately and denounce the page or the application.