A glimpse to the phishing and malware situation in Mexico (August – September)
Abstract
We have all received at least one fake message in our email accounts looking to obtain personal information (such as users, passwords, credit card data, etc.) or that redirects us to websites that download malicious programs. These emails, which appear to come from a reliable source, are known as phishing and make use of social engineering techniques to trick users. The following report shows a general analysis of several malware samples related to phishing websites that were reported to UNAM-CERT, this with the objective of showing some of the most common cases and reducing the number of affected users.
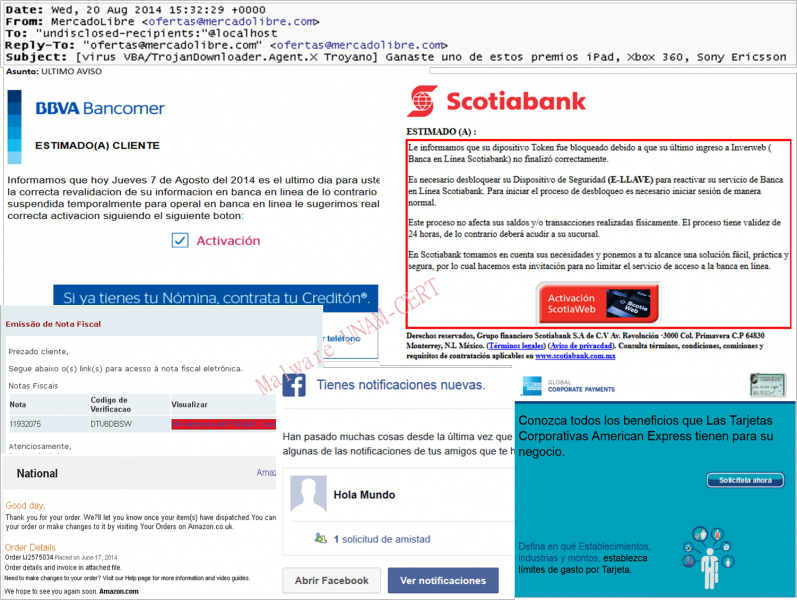
Some of the most used topics in phishing are related to:
· Banking Entities
· Online billing
· Access to a user's account without permission
· Data updates in an online service
· Celebrity rumors
· Social Networks
· Prices won
· Products bought or promotions
· Supposedly personal affairs (e-cards, photos, etc.)
-----Mensaje original-----
De:
Enviado el: martes, 02 de septiembre de 2014 02:40 a.m.
Asunto: tu pareja te engaña, te envio pruebas...
lamento que te enteres por este medio pero tu pareja te engaña.
hace tiempo estoy saliendo con alguien y me engaño diciendo que no tenia compromiso con nadie y hace poco me entero que es tu pareja te adjunto unas fotos para que sepas como te engañan y se rien de ti
Pronto te enviare mas.
How do they work?
As mentioned in previous malware reports (such as this, this or this, amongst others), the objective of phishing consists of stealing personal of financial information through the impersonation of an entity or service provider with good reputation. The email received tends to have links that redirect to fake websites with URLs and interfaces that look very similar to the originals. It is possible that other redirections take place before the browser displays the phishing site.
For example: one of the fake BBVA Bancomer emails we received asked us to habilitate the service of “cellphone alerts” that had supposedly become mandatory for the bank’s clients. To do this there was a link that, when clicked, redirected to the URL hxxp://clientes-js.com/CLIENtes-js.com/lLlLLl1Ll1lLl1lL1lLlLLl1Ll1lLl1lL1L.PHPlLlLLl1Ll1lLl1lL1L.PHPlLlLLl1Ll1lLl1lL1L.PHPlLlLLl1Ll1lLl1lL1L...L.PHP, as observed on the source code. This site redirected to bbva-bancomer.ctas-client.com/js/alertas/index.html.
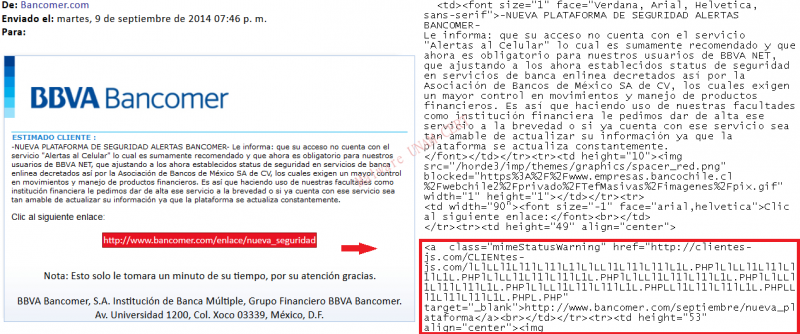
To know where the information of the forms will be sent, the source code of the site can be analyzed, since it usually contains the URL or the IP of the server where the collected data gets stored, as shown below.
In many occasions these sites redirect to malware downloads, therefore it is important to have antivirus software installed and updated to block the website before it downloads the malicious program.
Statistics
The statistics shown below are based on the emails sent to the malware analysis team at UNAM-CERT through[phishing at seguridad dot unam dot mx], [malware at seguridad dot unam dot mx] e [incidentes at seguridad dot unam dot mx] between august 1st and September 25th of 2014. It does not represent the whole malware situation in Mexico; it is, as the title suggests, a “glimpse” of the phishing attacks observed in our country during September and October. Spam related emails were discarded.
According to our analysis, the most common targets for phishing attacks were banking institutions (specifically Bancomer, Banamex, Scotiabank and American Express) that together represent the 33%.
Secondly, we have fake Facebook emails with friend suggestions and friendship requests. On the third place we have the emails of different entities that report the websites where the identity of an organization has been impersonated.
Most of these emails included a link to redirect the user to other malicious websites, whether to steal the data or to download malware. And 19% contained attachments that the user had to download to, for example, “verify his Amazon order” or “check his bank account status”.
Most of the attachment files in this 19% were Word documents (.doc). In second place, compressed filesthat contained malicious executables. Andin lesser extent we hadPDF files.
Summary of the dynamic analysis performed to the downloaded samples
A large amount of the emails with attachments received had Word documents that used macros for their malicious purposes, as described on this report.
A binary file (.bin) was also found. It established a connection to a Brazilian domain to download Windows online help files (with “hlp” extension).
· Network Activity
The network activity of the samples tends to be similar. First, they check if the infected computer has Internet access by making petitions to known domains or IP addresses, the most common ones amongst the analyzed samples during the period August-September are listed below.
wxw.msn.com
wxw.adobe.com
time.windows.com
8.8.8.8
go.microsoft.com
wxw.microsoft.com
wxw.adobe.es
Once the samples verify the computer has Internet access, they start making requests to malicious sites, either to send information about the compromised PC or to download other executables from remote servers. Some of the malicious domains found are the following:
| Domains | IP |
| laxxx.org.br/2013/images/link/srv02.hlp | 187.45.193.205 |
| intertecno.cl/armeria/SpryAssets/xxxxx/ss.exe | 200.63.96.13 |
| catoex.com.mx/xxxxx/ws/ss.exe | 201.175.12.143 |
| intertecno.cl/soporte/Connections/xxxxxx/ss.exe | 200.63.96.13 |
| intertecno.cl/xxxxxxxx/gusanito/PostalAmor.exe | 200.63.96.13 |
Interestingly, the domain intertecno.cl was used several times, by different samples, to download an executable called ss.exe. It is also interesting the fact that attackers recurred to emails of fake ecards from gusanito, which is a propagation method that used to be popular a few years ago. On the other hand, one of the URLs downloaded a .hlp file; unfortunately it was not possible to analyze it due to it being removed.
· Word documents
All Word documents, sent as attachments on phishing emails, downloaded a malicious program called ss.exe and stored it on the temporary internet files directory (C:\Documents and Settings\<usuario>\Local Settings\Temporary Internet Files\Content.IE5\<directorio>\ss[1].exe). They also created a copy of the downloaded executable on C:\Documents and Settings\<usuario>\Local Settings\Temp.
This executable goes through the subkeys in the registry in HKLM\Software\Microsoft\Windows\CurrentVersion\Uninstall. And obtains the name of the computer from the registry key HKLM\System\CurrentControlSet\Control\ComputerName.
For the documents to look legitimate, they use images with the logo of a specific company or product, such as: Mercado Libre, Microsoft Office, Banamex o Bancomer.
These images are downloaded from websites and the URLs can be observed on a strings analysis to the Word documents. Some examples are shown below:
hxxp://img.mlstatic.com/org-img/HOMENHP/logo_ml.gif
hxxp://i.imgur.com/47rWvh5.png
hxxp://www.pcsei.com.mx/IMAGES/banamex_logo.jpg
http://www.bancomer.com/minisitios/Home/Seguridad/abr10_2/imagenes/logo_...
· Malicious Executables
Most of the downloaded samples presented a typical behavior: test the internet connection, download files from remote servers, send data to remote servers, create registry keys to guarantee persistence on the computer and trojanize legitimate system processes. However, an interesting sample was the one downloaded from an email sent by ofertas@mercadolibre.com, that told the user about a won iPad, Xbox 360 or Sony Ericsson, because when executed in a virtual machine raised a alert of infection for Zeus on the IPS (Intrusion Prevention System). The sample was called Order_report.exe and presented the following behavior:
- Creation of a svhost.exe process trojanized.
- Removal of the file after its execution
- Reading of the file C:\WINDOWS\System32\drivers\etc\hosts.
- Creation of a directory with a random name on the path C:\Documents and Settings\Jane\Application Data\ and inside an executable.
- Requests to the domains gnuwin32.sourceforge.net, projects.sourceforge.net, activestate.com, offnamerty.ru, web.tuxfamily.net, nowrap.de and sourceforge.net/forum/forum.php?forum_id=74807, which triggered the alert of the IPS.
- Binary File
This file made the following actions:
- Copy itself to C:\Users\Joe\AppData\Local\Temp\
- Tries to download metadata of two Windows online help files (.hlp), stored in a remote server, using the HEAD method.
- Modifies the registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\SideBySide.
- ss.exe
Creates a data file called “cur” at the same path where ss.exe gets executed and deletes it almost immediately. It didn’t show network activity nor made use of any of the common methods to guarantee its persistence on the computer. On the file properties it was indicated that the name of the company was “Tesco” and that the original file name was “PRI.DLL”.
Summary of the static analysis performed on the downloaded samples
The files found were analyzed and no packers were detected. For this report, the static analysis was carried out based on the system calls and the findings are grouped by programming language, since the characteristics of the samples of each group were very similar. The most relevant system calls are mentioned below:
· Executables in Borland Delphi
The binary file found made use of functions that manipulate de registry to: open and close keys (RegOpenKeyExA y RegCloseKey), obtain the data typeandthe data of an open registry key (RegQueryValueExA), write the attributes of an open key to the registry, amongst others.
The functions related to the file system included common actions such as: search for a file in a directory (FindFirstFileA), write on a file (WriteFile), establish their physical size (SetEndOfFile), read from a file (ReadFile), move a file or a complete directory (MoveFileA), create or open a file or device E/S (CreateFileA).
Additionally, it also made use of the following functions:
GetTimeZoneInformation: Obtains the configuration of the time zone.
GetTickCount: Obtains the number of milliseconds that have passed since the system started.
TrackMouseEvent: Notifies when the mouse pointer changes to another window or moves above one during a certain amount of time.
GetKeyboardState: Stores de state of the 256 keys on the buffer specified by the user.
GetKeyState: Obtains the state of the virtual key specified.
Both GetKeyboardState and GetKeyState are commonly used by keyloggers written in Delphi.
· Microsoft Visual Basic
After disassembling the executables developed in Visual Basic we observed that the entry point was the function ThunRTMain.
Only functions imported from the MSVBVM60.dll dynamic link library were observed.
The function DllFunctionCall is usually found in this kind of executables because it obtains the address of a function that belongs to a DLL. This call can be observed on the sections of the executable that present a pattern of instructions as the one showed on the following image.
Finally, functions related to file management were also found: vbaFileClose, rtcKillFiles, vbaFileOpen. And the function IsDebuggerPresent, used by the sample to detect whether it was opened with a debugger.
· Microsoft Visual C++
Some of the most relevant functions found on this executables were the following:
RegNotifyChangeKeyValue: Notifies about changes to the attributes of the specified registry key.
GetComputerName: Obtains the name of the local host.
FindNextFile: Continues the search of a file.
GetVolumeInformation: Returns information about the file system and the volume.
LZOpenFile: Creates, opens, reopens or deletes the specified file.
FtpDeleteFile: Deletes a file stored in a FTP server.
timeGetTime: Obtains the time in milliseconds since Windows started.
EndDocPrinter: Terminates a job on the specified printer.
Recvfrom: Receives messages from a socket.
closesocket: Closes an existent socket.
GetTempPath: Obtains the path to the temporary files directory.
PathRemoveExtension: Removes the extension from the name of a file on a path.