Fake DHL email lead to malware download
Computer Emergency Response Team UNAM-CERT, received a notification about an email that reached to Hotmail users inbox, apparently, comes from DHL parcel service. The email is shown below:
In the email body, it is displayed shipping notification, which encourages the user to obtain further information by selecting either of two options:
1.- Click on the URL
2.- Enter the shipment number in the tracking page (this number is provided in the same email).
Both links leads to the download of "Shipping-Detail.zip", a file compressed in ZIP format. When unzipping the “Shipping Detail.exe”, a binary file is extracted, enough reason to start the analysis of the executable file.
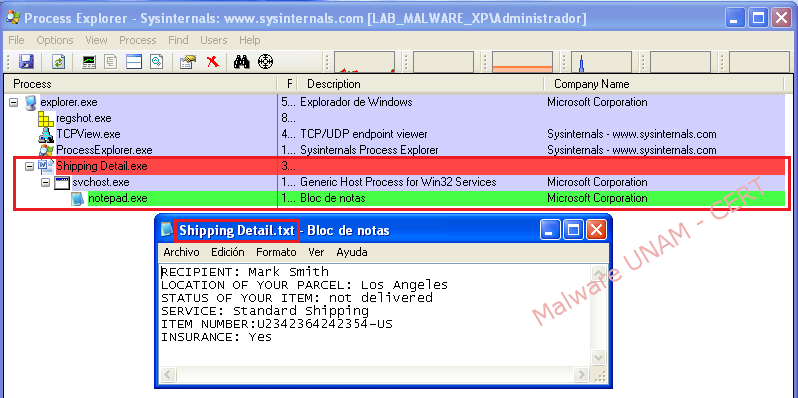
After running the sample in a controlled environment, the “svchost.exe” process was started up, which starts up at same time “Notepad.exe” process, the notepad shows the next text:
The network activity shows multiple synchronization requests by the “svchost.exe” trojanized process, from the infected computer to web servers by 8080 port.


With the Wireshark tool, it is possible to apply a filter for TCP traffic, which shows three attempts of synchronization for each IP address of the remote servers. The connections can't be established because the web services consulted by the malware are already down.
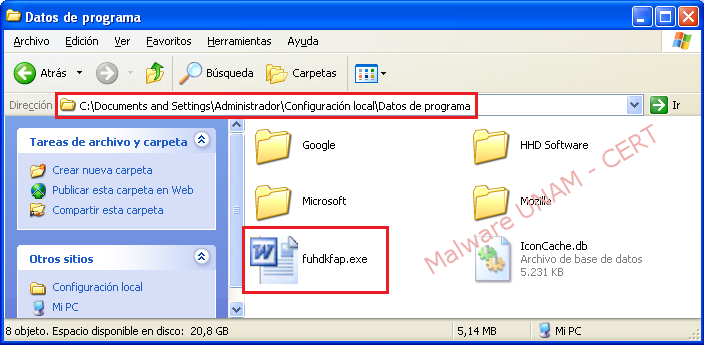
Regarding the changes in the file system, the malicious sample makes a self copy in the path C:\Documents and Settings\Administrador\Configuración local\Datos de programa\ and creates a file with the name “Shipping Detail.txt”, that is displayed to the user after the execution and, finally, it is autoerased.
Below it is showed the file created by the malware:
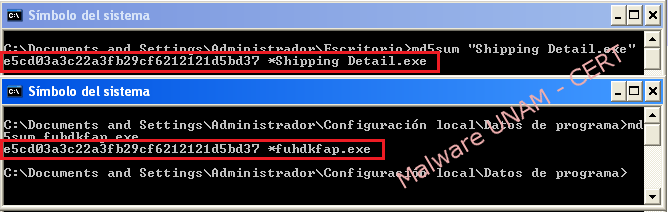
By getting the created file signature with a random name and the signature of the original malware, it is easy to see that those both are the same file.
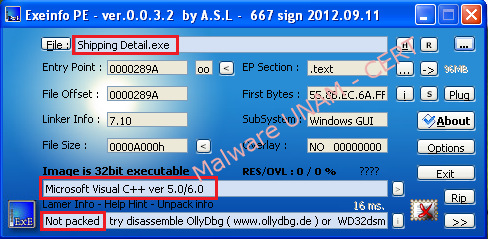
ExeinfoPE tool yielded two important data. First, it is showed that the sample is not packaged, which means that a string analysis can be performed. Secondly, the malware was written in C++ language.
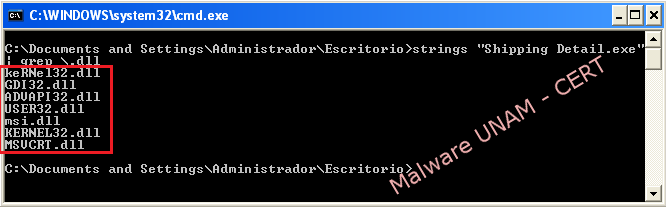
Making a strings analysis to the executable file, there were showed some names of the dynamic link libraries used by the malware piece.
The "Shipping-Detail.zip" file was hosted on a server in Germany, which surely was exploited in order to host the malware sample.
The report generated by VirusTotal service shows up that only 10 of 46 antivirus detect this threat:
In the report of file “Shipping Detail.exe”, it is also shown that 10 of 46 antivirus detect it as malicious. The difference between reports is that Emsisoft solution detects it as a malicious file and McAfee-GW-Edition does not.
In the analysis for this particular sample, no more malicious actions than those presented in this report, the web services that the malware piece tried to query, they were not available.