Zombies through Facebook
Yesterday, we received a notification from a user about certain links which are distributing malware through Facebook chat. These links are referring to a photo and have the objective of cheating users when clicking on them.

When a user tries to open the image, it is redirected to the site http://www.-sitio-.eu/images/, which pretends to be the genuine Facebook site and it shows a message reporting: “The photo has been removed”, after that, it appears a window to download the malicious file facebook-pic000934519.exe.
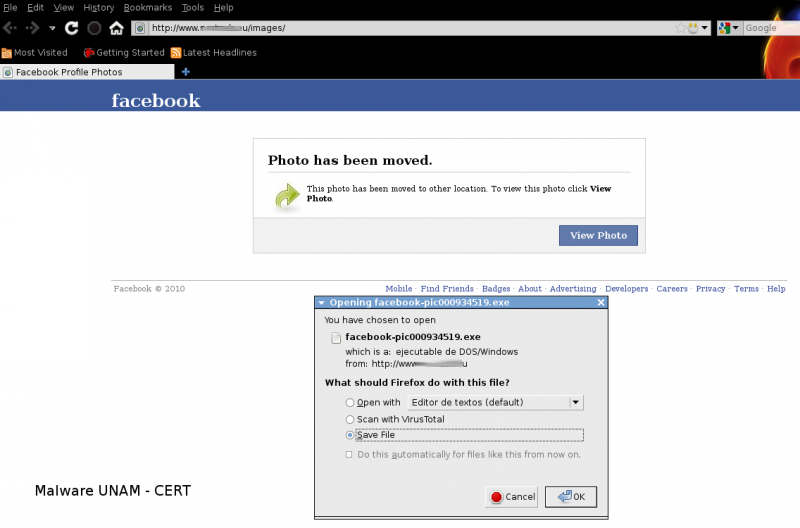
To the moment, this file is not recognized by many antivirus engines:


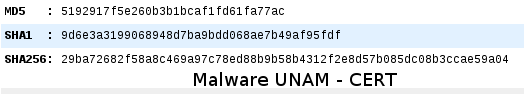
The sample's hashes are:
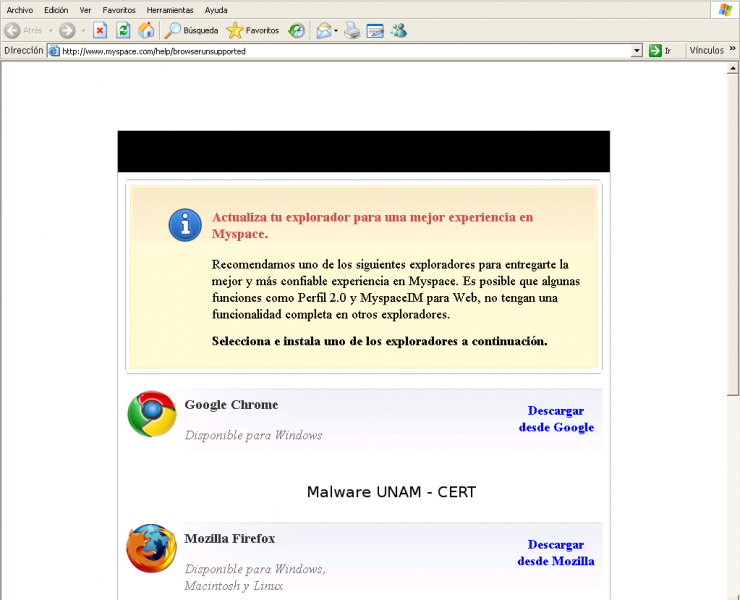
When is executed and due to that the web browser in our analysis lab was not updated, it started Internet Explorer with the site http://www.myspace.com/help/browserunsupported.
The executable was copied to the folder C:/WINDOWS/, with the name nvsvc32.exe and then, it started a process with that name and in order to guarantee its execution in each system startup, it added the registry key HKLM\Software\Microsoft\Windows\CurrentVersion\Run, with the registry value "NVIDIA driver monitor"="c:\windows\nvsvc32.exe", to cheat the user pretending to be a driver of NVIDIA Video Card.
Besides, it added a registry key HKLM\System\ControlSet002\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List, with the registry value "C:\
In this process (nvsvc32.exe) opened the port 1039/TCP and established a connection with the IRC server 77.X.X.106:6663.

In the IRC communication, it can be appreciated the links spread by the malicious code. At this moment they are still active.

After a second sample execution, the domain from which is spread the malware, pretends belong to facebook: hxxp://YYYY.facebook.com/photooftheyear/photo.php

We also identified, actually, the dialog that refers to “This photo has been removed” is an image inserted through an iframe and redirects to the site http://
In this site is also stored a malicious executable: hxxp://-XXXX-.com-/images/facebook-pic000934519.exe
We ran the sample a third time and we proved that the site, from where is downloaded the malware, as well as the image location have changed, now is hxxp://-ZZZZ-.be/images/facebook-pic000934519.exe