UNAM-CERT received a report about an executable file that appears to be malicious. Binary was hosted in a MX domain with the following name “BC-62016.exe”
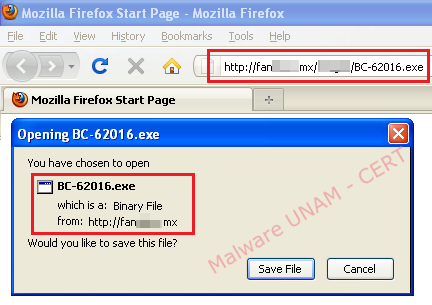
The first analysis was conducted in a controlled environment without Internet connection. When the sample is executed at first, a process with the same name of the file was created, then a new process called “vadoo.exe” was created too.

After that, the malware affects the “explorer.exe” process, a really common behavior when a computer gets infected with a sample of ZeuS bot. But, at this point, it’s not enough information to determinate that the infected computer becomes a part of the ZeuS botnet.
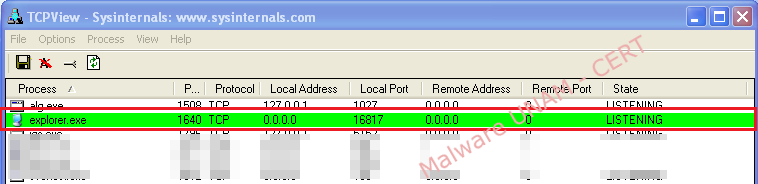
In the file system a folder named “Ixnyit” was created and inside of it, the “vadoo.exe” program is hosted, which was able to be perceived in execution when the system got infected.
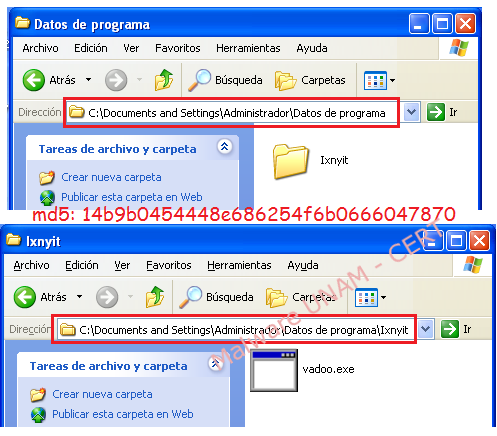
The above registered changes can be corroborated with the report generated by the “Regshot” analysis tool.
Another important change in the file system is that the malware erases itself from the path where it was executed at first time. This behavior can also be bound to the bots generated by the ZeuS toolkit.
Talking about network activity, it tries to resolve a different domain where it was downloaded, but it is also a MX domain.
During a second execution, the malware was provided with Internet connection with the goal of compiling more information about its behavior. By this time, the name of the executable file that was generated in the path “C:\Documents and Settings\Administrador\Datos de programa”, was different, the new file was named “cuibf.exe”.
Having Internet connection, the sample establishes a network connection to communicate with its “Command and Control” waiting for instructions of malicious activity in the infected computer.
In the image below there is shown the folder and the file generated by the malware “BC-62016.exe”:
Once the network connection is established with the “Command and Control”, a download of two files is launched, storing the files “te.exe” and “tmp305da5a5.exe” in a temporal folder.
In the image below, is shown the location of the two executable files downloaded in “Temp” folder. The files have the same MD5 firm, what indicates that it’s the same file, so once it has been downloaded, renames itself for ensuring its execution.
Into the network traffic captured during the process of infection, it can be observed the complete path where the download was executed. The “te.bin” file it’s a configuration file of the “Command and Control”.
In the network packages related to "GET" petitions made by the "bot" can be appreciated a download made by Windows operating system.
During strings analysis of binary file “BC-62016.exe” it appears many times “Stephani” word, that could be an allusion of a woman name.
Starting with the information extracted from the network traffic, we proceeded to visit the website that was hosting the malware downloaded on infected computers.
It was a legitimate site hosted in México and that surely was violated by a malicious attacker to mount the ZeuS “Command and Control”.
The website committed not affect the main page, but they mounted malicious configurations in a subdirectory that shows information in Japanese language.
The malware firms are listed below:
By the time when the analysis was made, VirusTotal service shown that the treat was detected by 19 up to 45 antimalware detection motors. Right below the report:













