Virus that infects executable files through an allegedly update of the Adobe Flash plugin
Recently, the UNAM-CERT received a report about a malicious file that was propagating through the network and that pretended to be an update of the Adobe Flash Player plugin.
Once the website was accessed, it displayed a window to accept the download of the file.
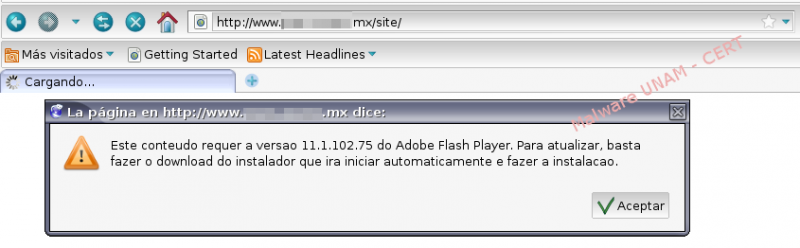
After downloading the file, it saved itself with the name dia11_puxa_cliente2.exe and displayed the following page, that pretended to be a legitimate Adobe Flash website.

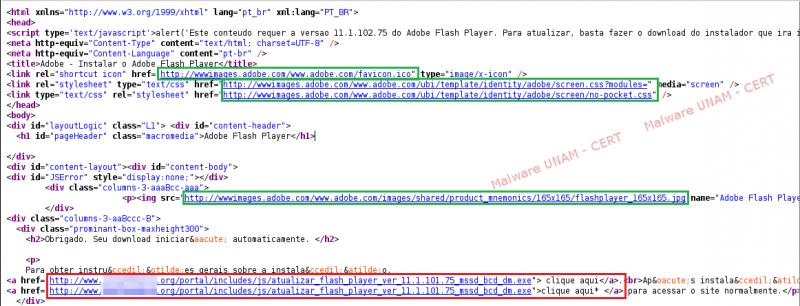
On the website we could observed the “clique aqui” links, which triggered the download of the malicious file; however, this download was not started from the infringed website, but from a different server. The source code of the page allowed us to determine the domain name of the site in which the malicious file was hosted. On the next image, the domain that hosted copies of the malicious file is shown in red; whereas the links to the legitimate Adobe Flash website, from where the images were loaded, are shown in green.
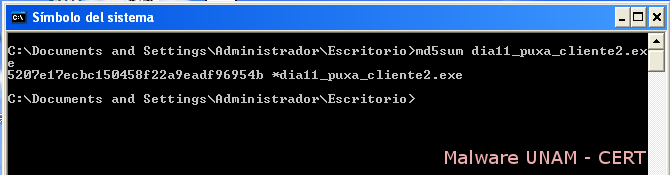
The md5 signature of the file is shown below.
Using the tool ExeInfoPE, it was determined that the file was not packed.

On the string analysis, we observed that the downloaded file contained the pattern “Ijeefo!Esbhpo!wj”, which allowed us to identify that file was infected with the virus known as “Jeefo”; that got its name after obfuscating the string “Hidden”. In fact, the pattern followed to obfuscate is a shift of one character to the right and to the left.

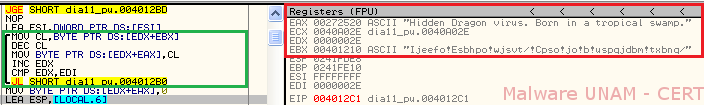
On following image, the routine that makes the shift of characters, which is part of the function stored at the memory address 00401280, is displayed.


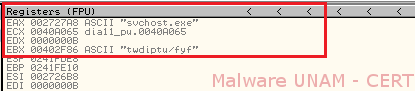
Using OllyDbg, we proceeded to locate the routine shown previously. The first time this routine was called, we observed the process used to de-obfuscate the strings included inside the file. When the process was finished, the string “Hidden Dragon virus. Born in a tropical swamp” was displayed, as shown in red on the image below.
Due to all the strings used by the malware being obfuscated, this routine is called before executing requests to different system files or to create a file with a specific name such as svchost.exe.
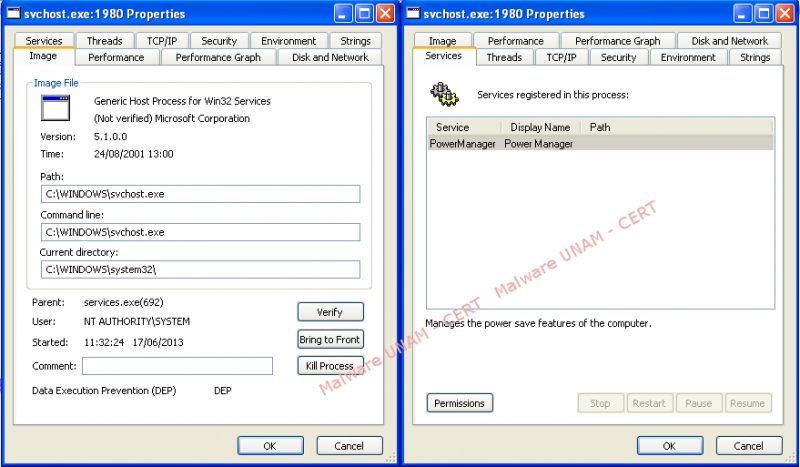
On the next images, the strings “svchost.exe” and “PowerManagerMutant” can be observed. The first references the file created on the directory “C:\Windows”, whereas the second one references the service that registers on the system.

After executing the sample, it displayed a window as the one shown below.

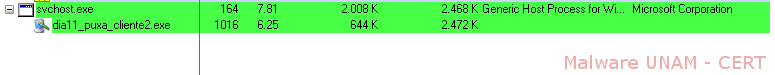
The started processes were only the ones corresponding to the executable file.

As for the file system, we observed that a new service called “PowerManager” with the description “Manages the power save features of the computer” was registered. It was also observed that it referenced the program svchost.exe located on the path “C:\Windows\svchost.exe”. It is important to remember that the legitimate file svchost.exe is located on the path “C:\Windows\System32”.
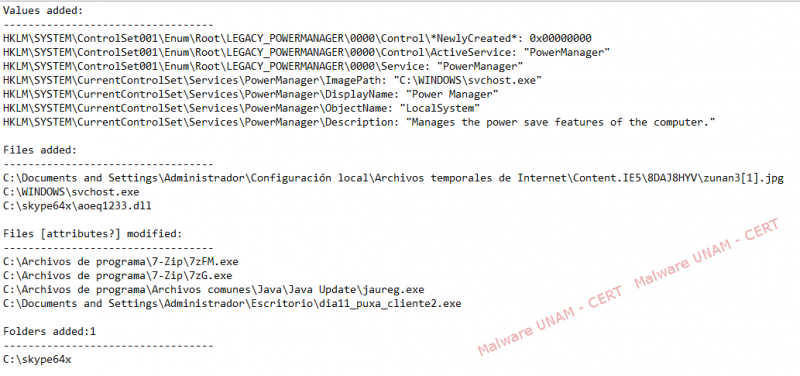
The image zunan3[1].jpg, the file svhost.exe and the DLL aoeq1233.dll were also added. The executable files 7zFM.exe, 7zG.exe and the malicious sample dia11_puxa_cliente2.exe were modified.
After the “PowerManager” service had been registered in the system, it started itself through the malicious file svchost.exe.

On the Windows registry editor, the “PowerManager” service looked like this:

Using the file command it was determined that the downloaded file zunan3.jpg did not have the correct format, being of type “data”. In addition, using a hexadecimal editor it was observed that it did not have the magic number “FF D8” expected for the jpg file type.

After analyzing the log created with the ProcessMonitor tool, we determined that the file dia11_puxa_cliente2.exe carried out a search on the internet temporal files to obtain access to the file zunan3.jpg, with which it created the DLL aoeq1233.dll.

As for the observed network activity, conversations to two domains on the 187.73.33.X segment were registered.

Both of them located on Brazilian servers.

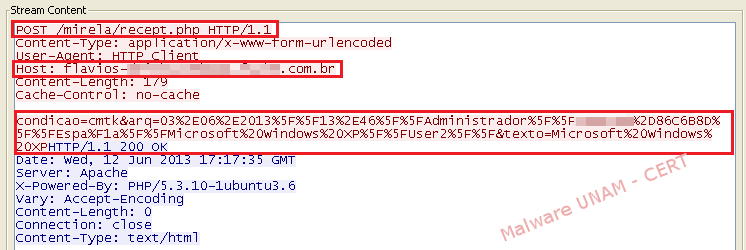
The analysis of the network traffic showed the moment in which the request to the file zunan3.jpg was made. On the next image the request, the domain and the content of the downloaded file are shown in red. The content was observed with the hexadecimal editor.

As for the network traffic of the second conversation, a POST request to a PHP file was made. The information sent included the username, the computer name, language and operating system used. With this data, the malware author is able to keep a record of the number of computers infected.
The infection process used by the virus is done through the files that were executed, these files were modified through the svchost.exe process, which copies itself completely on the executable files, adding 36 KB to them. Once a file had been infected, the virus remains in it until it is executed again; during the execution of the infected file, the virus tries to copy itself to another file. In many cases, the file could end up being unusable.
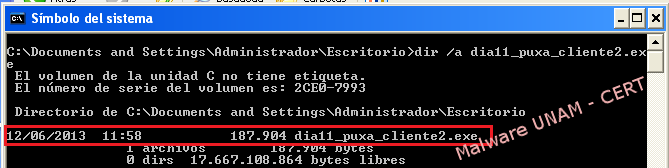
On the next images it is shown that the malicious file dia11_puxa_cliente2.exe changed its size after the execution.
Before execution
After execution
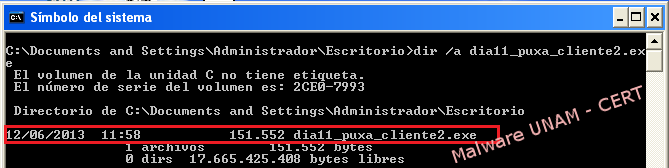
When the right operations are carried out, a difference of 36.352 Bytes could be observed. Additionally, it could be seen that the size of the svchost.exe file had the same size as the amount of bytes calculated beforehand.
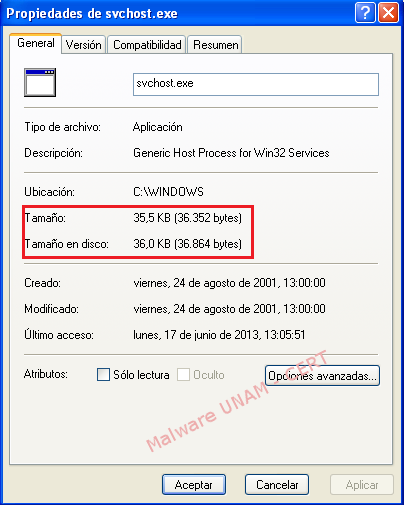
The file 7zFM.exe also presented modifications; therefore, we proceeded to carry out an analogous process to the one done by the malicious file. On the next images it is shown the size of the file before and after the execution of the malicious sample.
Before the execution

After the execution
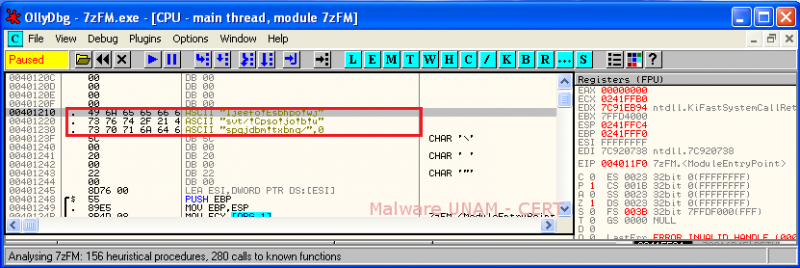
Once again, it could be observed that the size of the executable file 7zFM.exe has increased 36 KB. Using OllyDbg we could observe the strings of the “Jeefo” virus inside the executable file, as shown in red on the image below. This was a clear proof that the executable file was infected.
The md5 signatures of the files are shown below.
62727fa0d1e6b2ba0336d5ca9472c3a7 aoeq1233.dll
9e3c13b6556d5636b745d3e466d47467 svchost.exe
5207e17ecbc150458f22a9eadf96954b dia11_puxa_cliente2.exe
The analysis of the files carried out with the Virus Total website gave the following report:



It is necessary to maintain the antivirus updated to avoid damages on the computer and the programs; this is because, as mentioned above, in many cases these end up corrupted when the virus attempts to copy itself.