Virus blocks antivirus websites
In recent days, a malicious file was captured and it was identified as a variant of "Sality" virus, which began to spread itself in early 2003, and nowadays it continues infecting a large number of computers because it authors have been improved methods of antivirus evasion
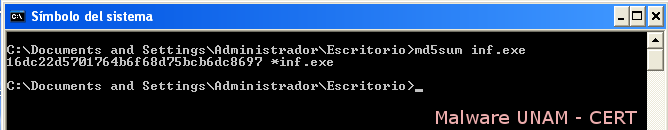
The captured file was downloaded with the name “inf.exe”. Its md5 signature is shown below.
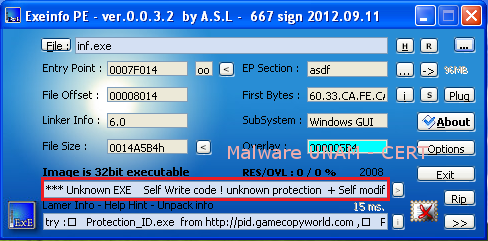
Before running the sample, “Exeinfo PE” tool was used in order to determine if the file was packaged. “Exeinfo PE” wasn’t able to determine the type of packer used, as shown in the following image.
An analysis of strings was performed, but there was no further information on the behavior of the sample, and this is because uses a single encryption algorithm to obfuscate text strings.
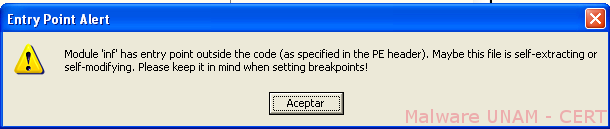
While attempting to use “Olly Debugger” tool, a message is displayed indicating that it is possibly a file that modifies itself. Viruses that exhibit this type of behavior are known as "polymorphic viruses", because they have the ability to modify themselves at runtime, thereby seeking to avoid the analysis of antivirus solutions.
Subsequently the sample was run in a controlled environment. However once the sample was executed the following message appeared.
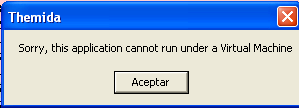

In the new window, there was a message indicating to the user that the application could not run under a virtual machine. However, this window does not belong to the malicious file, but the packer used to avoid the possibility of performing the reverse engineering process.
The only process that began while the window was active, was the malicious file itself.

It is noteworthy that despite the message displayed, the malicious file kept running. The process of infection observed indicates that the malicious file is injected into processes or executable files that are active, and which do not belong to the operating system-critical applications. In this particular case, the virus was injected into the process of the analysis tool "ProcessExplorer".
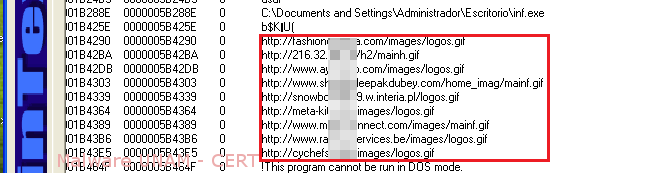
It is seen in the following image the intent that makes this process by communicating with various domains.
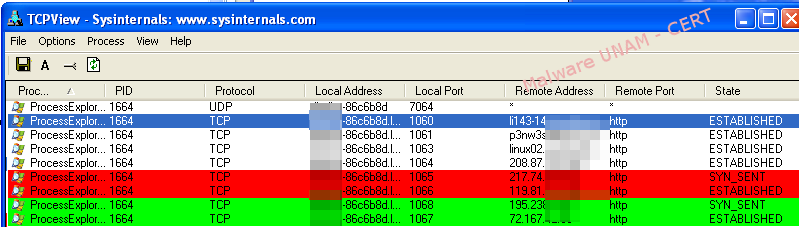
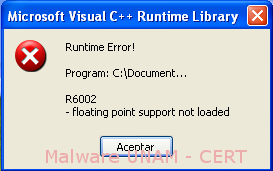
Because the virus overwrites the entry point of the application, the executable file of "ProcessExplorer" was corrupt, showing the following message when trying to use it.
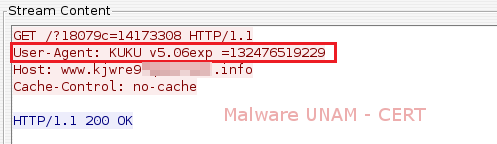
In network activity were observed requests with the string "KUKU", which is particularly when it comes to this virus, and it appears in the "User-Agent" in order to limit access to malicious files through a web browser.
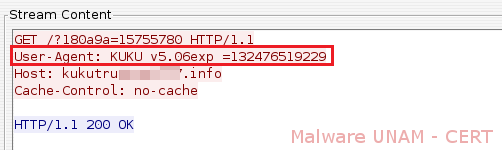
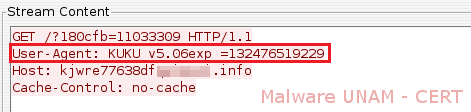
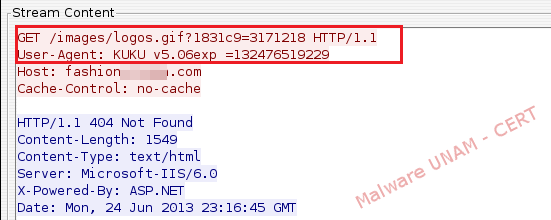
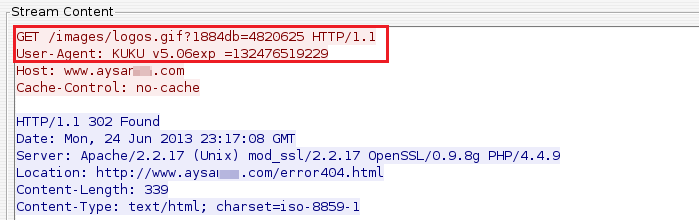
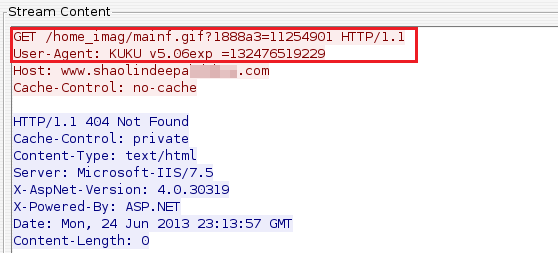
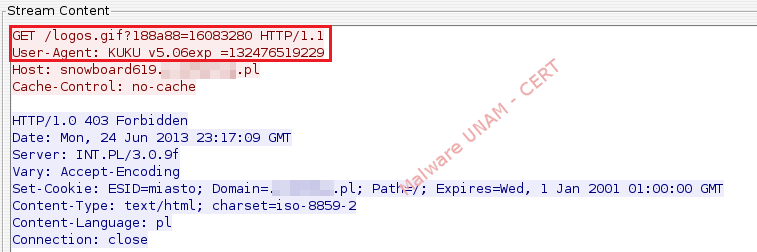
Requests to other domains follow the same pattern as those already shown. The number of registered domains are:
fashionenXXXX.com
snowboard619.w.intXXXX.pl
meta-XXXX.com
cychXXXX.com
kukutrustneXXXX.info
kjwre77638dfqwiXXXX.info
A method to get more information about the behavior of the sample, is to perform a memory dump of the process, "LordPE" tool was used to achieve it. After completing the process dump, turned to an analysis of strings where the name of the places that carried the malicious file requests finally showed.
The following image shows in red the strings "Oreans" referring to what appear to be system files, in addition to the possible reference to the site name "oreans.com".
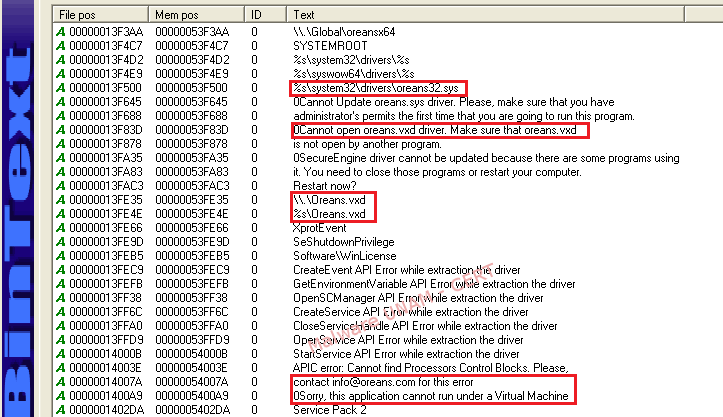
After an internet search, it was determined that the site oreans.com formally distributes packaging tool "Themida".
Now, if you choose to fix the alert displayed by the packager, you can edit the configuration file of the virtual machine (VmWare) by adding at the end of the ".vmx" file the following lines:
isolation.tools.getPtrLocation.disable = "TRUE"
isolation.tools.setPtrLocation.disable = "TRUE"
isolation.tools.setVersion.disable = "TRUE"
isolation.tools.getVersion.disable = "TRUE"
monitor_control.disable_directexec = "TRUE"
monitor_control.disable_chksimd = "TRUE"
monitor_control.disable_ntreloc = "TRUE"
monitor_control.disable_selfmod = "TRUE"
monitor_control.disable_reloc = "TRUE"
monitor_control.disable_btinout = "TRUE"
monitor_control.disable_btmemspace = "TRUE"
monitor_control.disable_btpriv = "TRUE"
monitor_control.disable_btseg = "TRUE"
monitor_control.restrict_backdoor = "TRUE"
If done this, when running the sample, the warning message by the packager, will not be shown. After running the sample with the corresponding settings, the malicious file will start a new process with the name "VMwareService.exe", which is not the legitimate process of the virtual machine.

Once running, this process made a number of requests to IP private network segment 192.168.0.0/24 on port 445 which is associated with the service known as "Microsoft-ds", possibly to find computers that have this service and thus exploit some vulnerability.
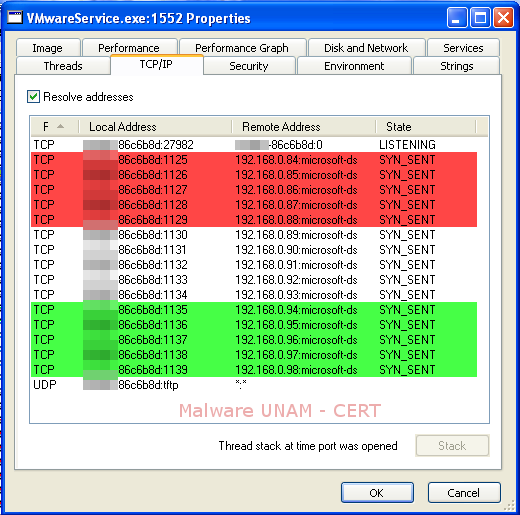
For more information about the vulnerabilities in this service, please visit the following link:
https://www.grc.com/port_445.htm
In addition, the sample made a series of requests to the registry keys to check if there are some applications installed on the system. Among the requests, it was observed that the sample checked if the emulator Wine was installed.

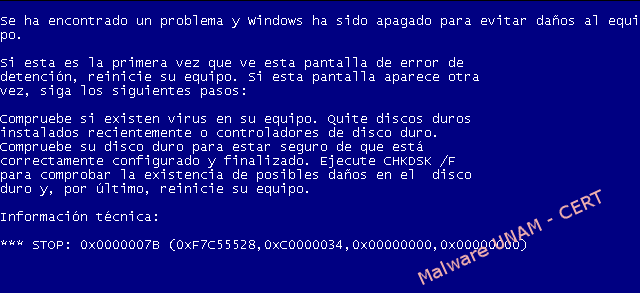
In the file system activity was observed that the registry keys that allow the system to boot in safe mode were eliminated. Therefore, to start the system in this way, will fail displaying a blue screen (BSOD).
Elimination was also observed ALG service which is associated to the firewall system. This ensures that requests made to external domains can not be blocked.
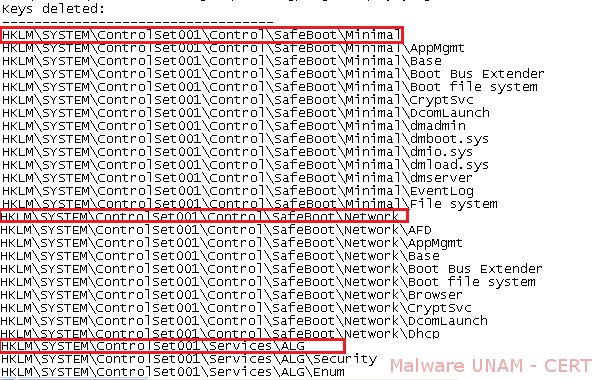
In addition, it was recorded the activity of multiple services, the first of which refers to "IpFilterDriver" which is used by the malicious file to block requests made to sites like Symantec Antivirus or ESET, among others.
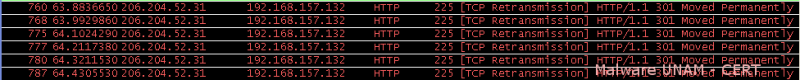
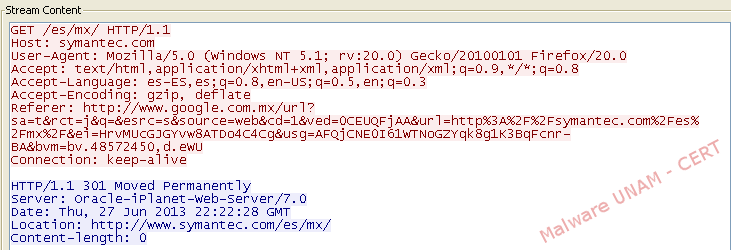
When we tried to access to the Symantec web site, we could observe in network traffic that multiple packets were being retransmitted because supposedly the site had been moved.
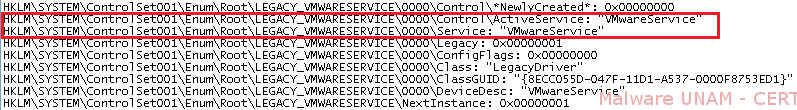
Additionally, malware added registry keys to register the service and start the malicious process "VMwareService.exe" in every startup of the system.
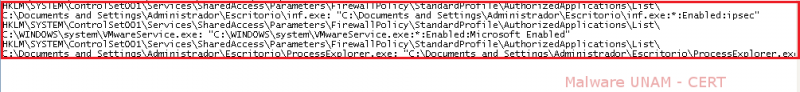
Infected processes were enabled in the list of allowed applications by the firewall, this way the requests made by the relevant processes would not be blocked.
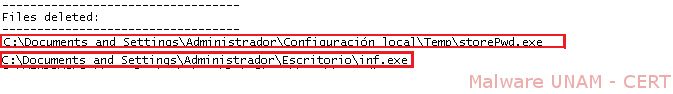
Finally, the virus conducted the modification of executable files, as shown below.
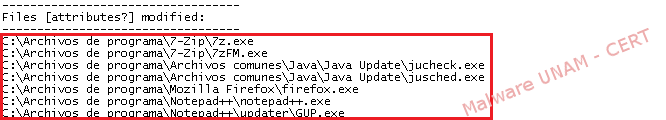
These files are modified in size because the virus is added to the end thereof, thereby ensuring that the execution of the virus files propagate again in case another infected file is eliminated.

The detection rate for this malware is 41 of 46 antivirus, so it is important to keep update the antivirus solution.
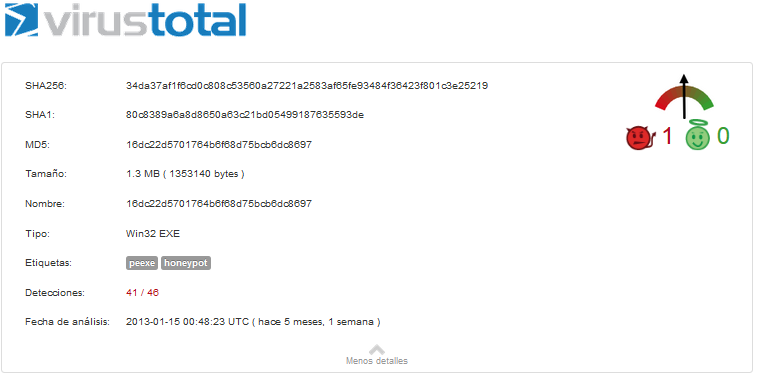
The full report can be found at the following link:
If you want to retrieve the start in safe mode and thus run the antivirus solution, you can follow the procedure previously posted on this blog at the following link:
http://www.malware.unam.mx/en/content/ransomware-impersonates-federal-police-identity