Twitter worm strikes goo.gl and redirects to a fake antivirus
Yesterday, in the website seguridad.unam.mx was published a note (http://www.seguridad.unam.mx/noticias/?noti=4285) that refers to a worm spreading in Twitter, which uses the Google service goo.gl, to shorten links, it redirected the user to several sites, where through the website (m28sx.html), it can be downloaded a fake antivirus.
Researching some time in the social network, the page mentioned above, we find the kind of messages used to spread the worm..png)
When we wanted to visit the website to where the link redirected us, we found out that it was already disabled and the redirection did not work. Fortunately, in a user tweet was published a link, which shows some active URLs, with the malicious code working. We randomly select one link, we copied and pasted in our Firefox web browser and we were redirected to the Google page. We decided to change the default User-Agent to one related with Microsoft Internet Explorer, using the User Agent Switcher plug-in and then, the selected URL opened a site showing the following message:
.png)
Due to Firefox security characteristics, the site was blocked, when appeared a message which warns that the PC was infected and the web browser crashed
.png)
We opened the site again, with a less updated Web Browser and it showed again a message that indicated that our PC was infected and it must be analyzed.
.png)
When clicking on the OK button, it started an alleged system scanning, when finished it showed us another message warning that “Windows Defender” had detected spyware and it was ready to remove it.
.png)
To remove the alleged threats, it appears a windows to download an executable called “pack.exe”. This executable is the fake antivirus “Security Shield”.
.png)
Analyzing the previous executable with different antivirus engines, just a few of them identify the executable as a threat.
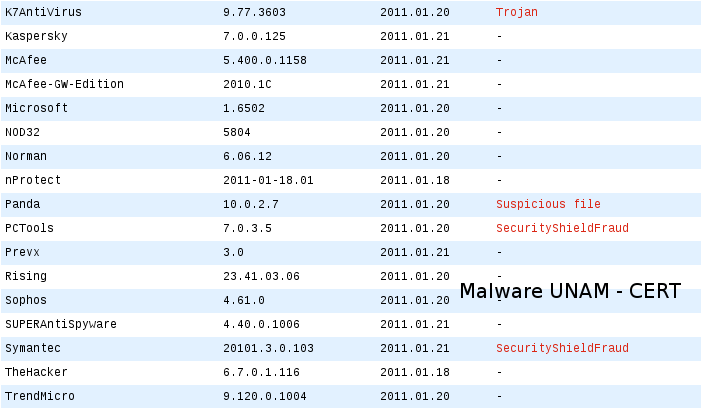
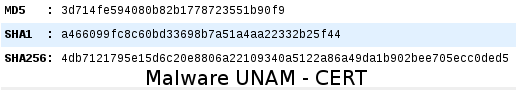
Its hashes are the following:
When the sample is executed, it started the installation of the alleged antivirus, then, it performed an “system scanning”, when finished it showed a window, which warns that to remove the detected threats, it was needed to buy a version able to remove it.
.jpg)
The executable was copied to the path C:/Documents and Settings/<usuario>/Configuración local/Datos de programa/, with the name zadotjbpr.exe. From here it ran a process with the same name, as well as a backdoor in the local port 1767 and it was added to the Windows registry key HKLM\Software\Microsoft\DirectDraw\MostRecentApplication, the following registry values: Created values: "Name"="zadotjbpr.exe" "ID"=dword:42aaa94c; Deleted values: "Name"="iexplore.exe" "ID"=dword:41107b81.
When the user wants to remove the alleged threats from its PC, the sample downloads the site used to steal the financial information and carry out the fraud. This page is accessed from a web browser contained in the executable. Analyzing the traffic, we were able to look that site and were able to obtain the “fictitious” data provided in the application..png)
.png)
Unfortunately, malicious code spreading through social networks, will be more frequent as the time goes by and attack vectors will also change, the best approach to keep us secure is updating our web browsers, our antivirus engines and most important not to pay attention to everything on the web.