SPAM email with message "POST Express Report " propagates malware
Recently, UNAM-CERT have received notifications about SPAM emails with the message POST Express Report, whose text is in English and informs to the user that a package was not sent to the address, for that reason the attached file contains instructions to recover the package mentioned above.
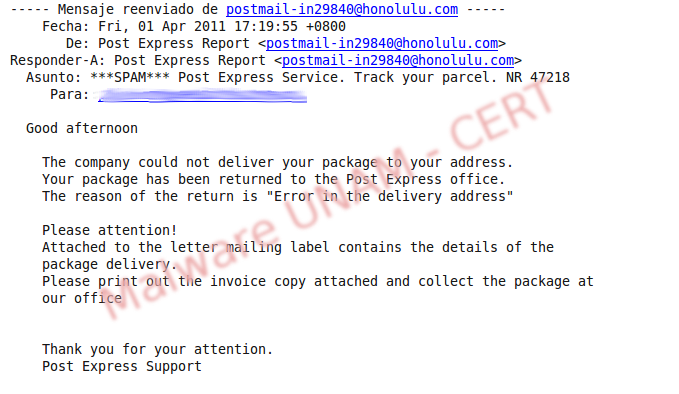
The attached file is in zip format, once decompressed, it creates the directory Invoice_Copy and then the Invoice_Copy.exe file, which is displayed with a Microsoft Word icon.
Analyzing the sample with antivirus engines, 30 antivirus detect it as a malicious file, most of them classified it as a trojan.
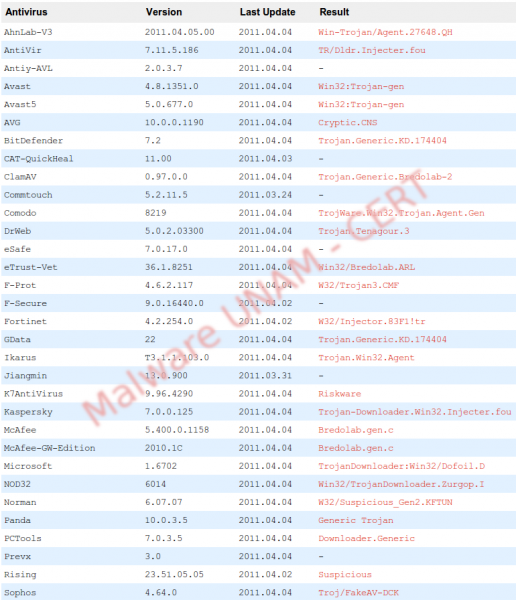
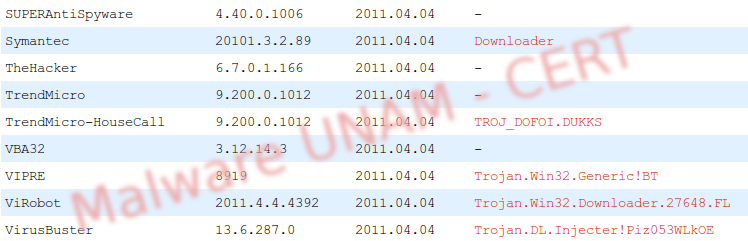
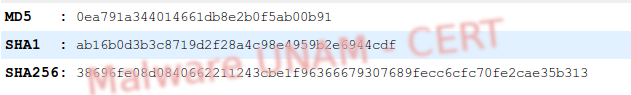
The sample has the following hashes:
Due to a string analysis we realized that the sample was packed, so we used the PeiD tool trying to find the packing algorithm the author's malware had used. PeiD showed us that the algorithm used to pack was UPX.
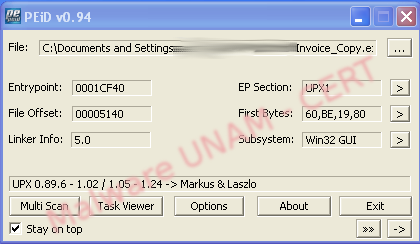
This kind of algorithm is reversible using the same tool, so that using UPX in a terminal we unpacked and repeated the string analysis.
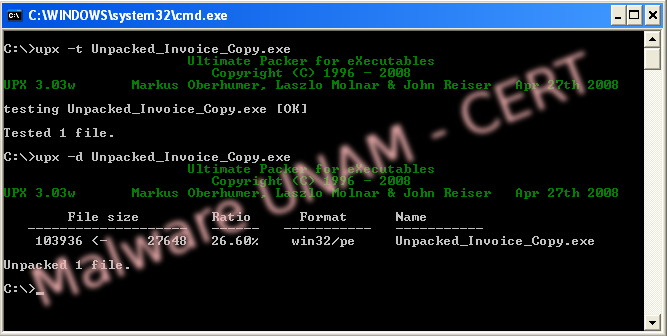
The analysis did not show us any useful information to understand the real behavior of the sample, so we started the dynamic analysis sending the sample to the laboratory.
The first step taken by the sample is turning itself into a trojanized process of svchost.exe, this file is a common executable in Windows, so that is common to see a process with this name.
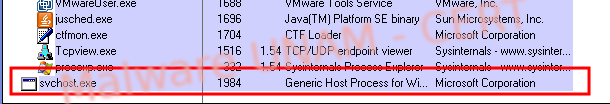
Then, the trojanized svchost.exe process starts opening connections to remote sites.
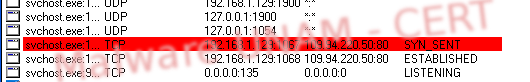

The malware requests DNS queries to several sites, as shown in the picture:
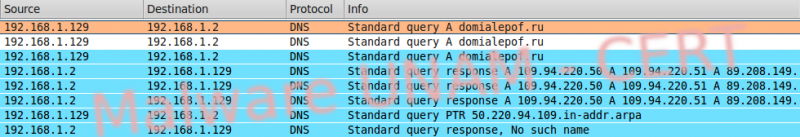
Once replied the requested DNS queries, it downloads a Microsoft Office file.
Analyzing the traffic of the particular frame was possible to read the text of the downloaded file.
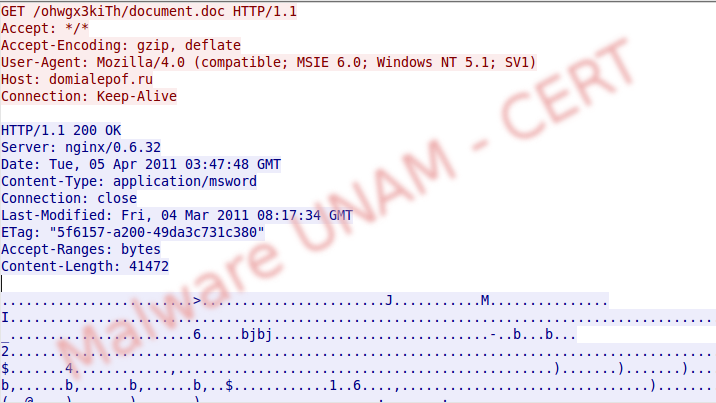
Immediately, it requests another site and downloads a binary file called 41.dat.

Both files are saved in temporal internet files in the computer. Sending the binary file to the antivirus engines , no one of them recognized it as a threat.
Once the connections have finished, it executes the default text editor in the computer and shows the following message, in order not to arouse suspicions about its malicious activity.
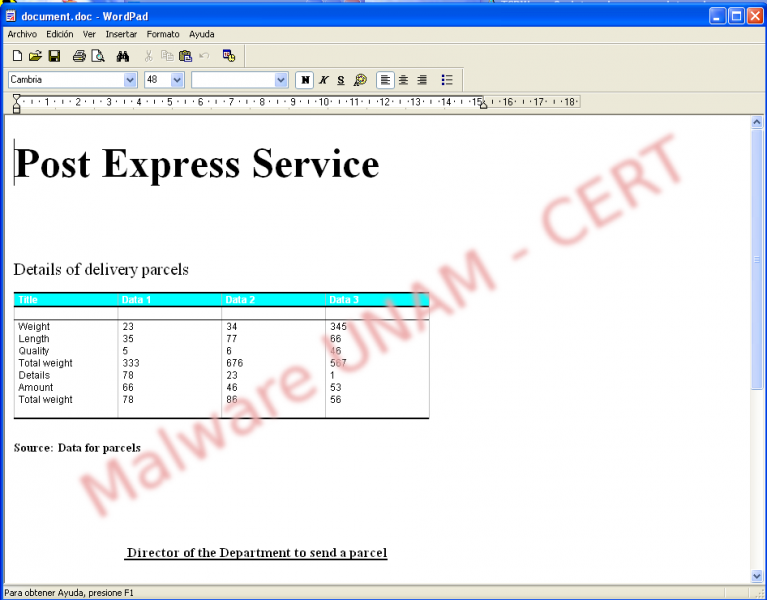
Once shown the message above, it does not perform any activity, but the svchost.exe process remains trojanized.