More alleged ecards from Gusanito - Botnet in progress!
Yesterday we received the notification of an email that was supposedly sent from the website gusanito.com. In the body of the email there were various links that lead to malware downloads and a “warning” that tries to prevent the user about fake emails pretending to be from Gusanito… Quite ironic, isn’t it?

As mentioned above, any of the links would make the user download an executable called “postales” (the word in Spanish for ecard), hosted in a site that was apparently compromised by the malware creators.
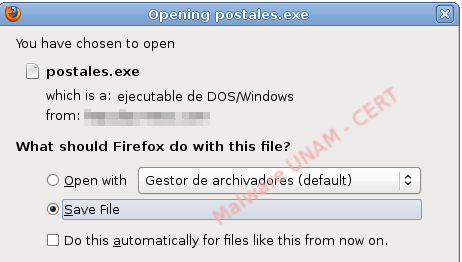
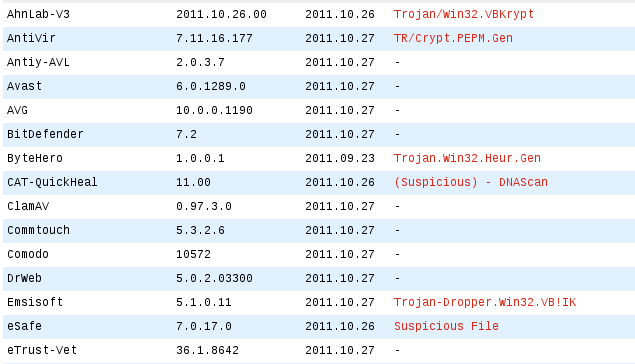
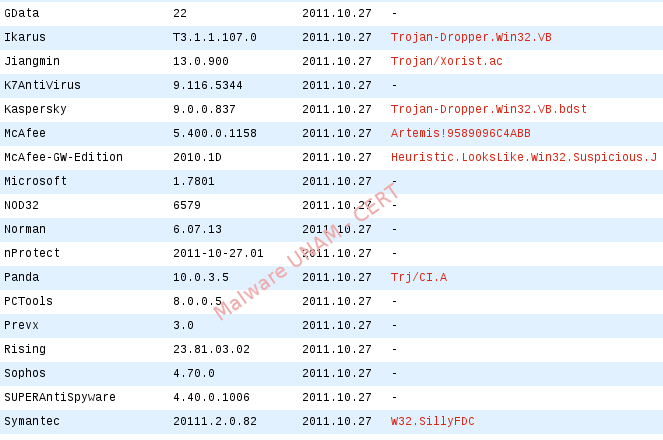
When this file was analyzed, only 13 antivirus engines detected it as a treat in VirusTotal:
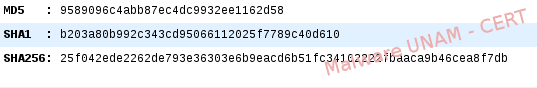
The MD5, SHA1 and SHA256 hashes of the sample are shown below:
Apparently, the malicious code is still in developing phase, because during its execution in our lab, it only started a process with the same name and establish a connection to the web server 93.174.91.3, that ended after a few seconds. It did not modify the Windows registry keys to guarantee its execution every time the system restarts.
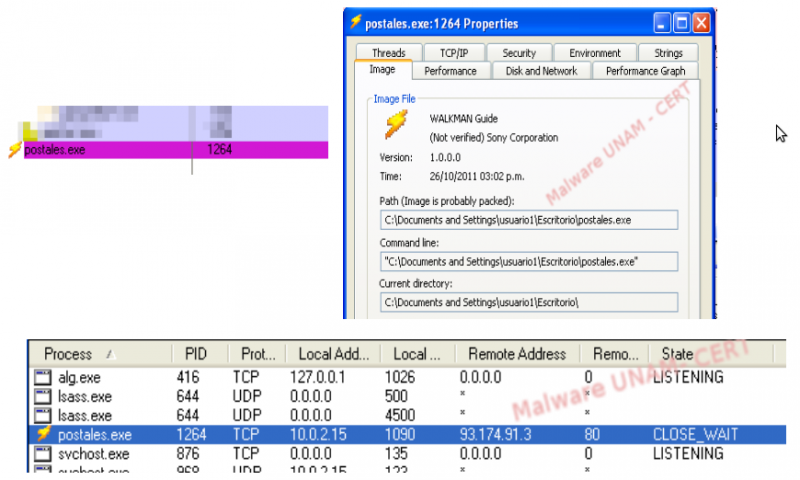
On the traffic analysis, we detected DNS requests to the mentioned web server.
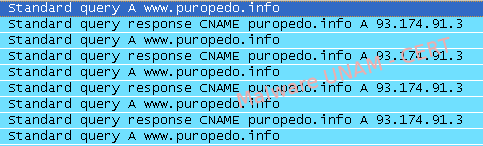
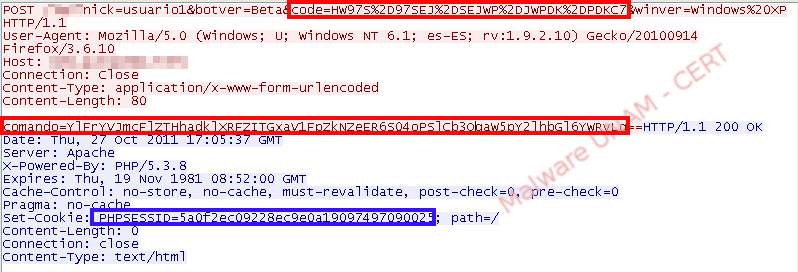
Furthermore, a POST request to the same server that sent information related to the infected computer was found. And also the variable botver=BETA, that made us think the malicious code was not finished.
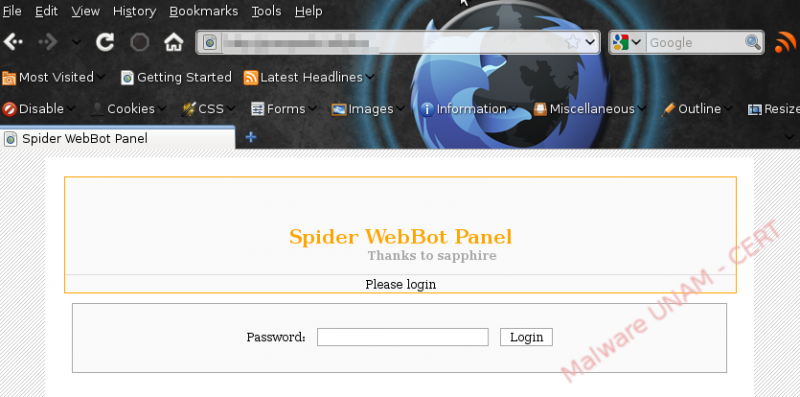
Finally, we could determine the main webpage of what seems to be the administrative console of the botnet in a section of the request made by the bot.
So far, there are no elements that allow us to determine the objective of the variable “code”, about the command sent in the POST request or about the php cookie that the server sends as response.