Malicious software used to steal credentials of information exchange services
In recent days we captured a malicious sample that, once executed on the computers, generated a large amount of network traffic; thus, we proceeded to analyze it.
The file captured was renamed 01082013.exe and has the following signatures:
MD5: b06966d77e3949e1e5edf64c82e54b1e
SHA256: 5c1a43ba2a4af38629421b12c6d1f43560c997565d5aa122b2bdb4fd99c60bba
The string analysis of the file showed us a couple of functions used by the malicious file. On the next image, the functions marked in red are the ones that allowed it to obtain the configuration values from the initialization files (GetPrivateProfile), as well as the attributes from the directories and the files in the system (GetFileAttribute). The function CreateDirectory is also present, so the sample probably creates a directory on execution.
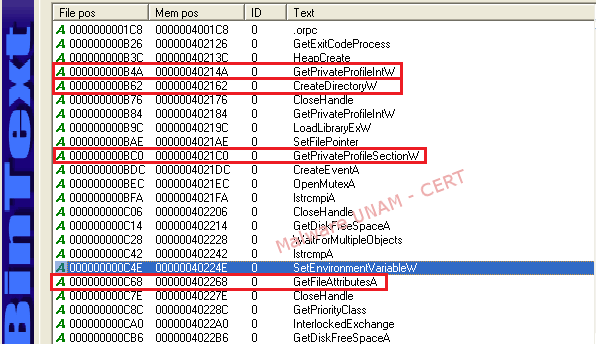
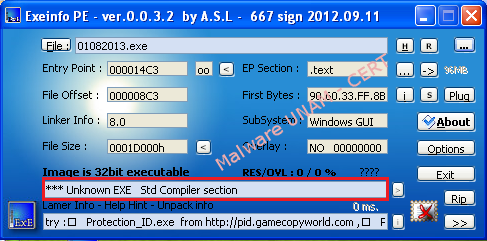
However, the amount of strings obtained was very low, which is usually an indication of the use of a packer on the executable. Unfortunately, the ExeInfoPE tool was not able to determine the type of packer used.
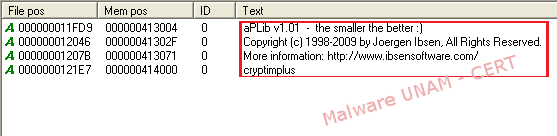
When the process that corresponded to the malicious file was active, it was possible to carry out a memory dump with the LordPE tool; after which it was possible to make a second string analysis.
This is how we could determine that the malicious software made use of a library to compress the executable file and thus difficulting the analysis of the code.
We could also obtain the set of domains to which the malicious software made requests, where two types of files could be observed on the URL addresses: PHP files and executable files.
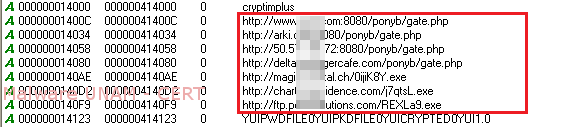
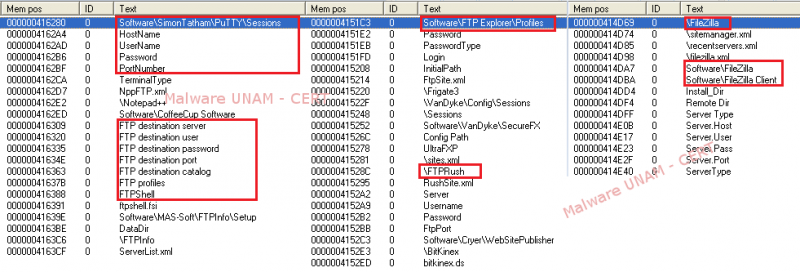
Additionally, during the analysis we found a great amount of strings that referenced different FTP services, next to these there were strings that indicated the fields of user and password; with this it was possible to conclude that one of the objectives of this malware is to collect the access credentials to different FTP servers.
It was likely for the malware to attempt to steal the accounts of the mail services found on the system and then send spam to different receivers. On the next image the strings that correspond to the Outlook and Thunderbird mail services and the protocols used to exchange mails are marked in red.

After the execution of the malicious sample different processes were started after being downloaded from the internet. The execution order and the way in which the processes were executed are shown on the image below.
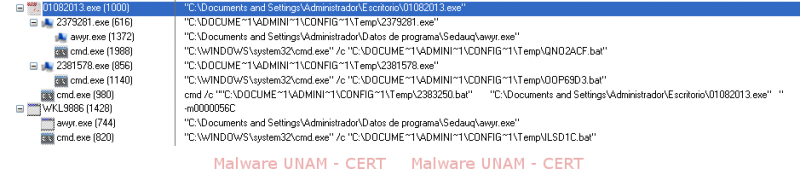
The files 2379281.exe, 2381578.exe and WKL9886 were downloaded from the Internet.
During the analysis, it was observed that the file 01082013.exe had as its primary function the download of additional malicious files. If the files were downloaded successfully, there was a higher network activity due to requests being made to the domains listed below:
wl18.YYYbland.ch
YYYrtomresidence.xxx
YYYturethisdallas.xxx
YYYdayaviation.xxx
YYYi.xxx
YYYic-crystal.xx
ftp.YYYrasolutions.xx
There were also connection attempts to the following IP addresses.
|
XX.57.185.72 |
|
XX.43.216.118 |
|
XX.125.162.221 |
|
XX.165.148.5 |
|
XX.77.13.23 |
|
XX.22.158.150 |
|
XX.95.46.22 |
|
XX.217.8.137 |
|
XX.90.134.19 |
|
XX8.227.104.254 |
|
XX0.255.230.41 |
|
XX3.81.192.36 |
|
XX5.1.200.201 |
|
XX.117.10.58 |
|
XX.8.206.100 |
|
XX8.210.219.218 |
|
XX8.197.50.249 |
|
XX.0.126.100 |
|
XX8.60.184.54 |
|
XX9.253.90.151 |
|
XX6.21.197.54 |
|
XX.63.204.26 |
|
XX8.202.187.155 |
|
XX.156.118.144 |
|
XX3.191.159.195 |
|
XX.221.93.26 |
|
XX.39.32.218 |
|
XX.134.85.68 |
|
XX.104.16.83 |
|
XX3.194.113.178 |
|
XX3.194.113.184 |
|
XX0.178.220.220 |
|
XX4.7.54.179 |
|
XX.139.149.134 |
|
XX3.12.34.148 |
|
XX.228.0.230 |
|
XX8.217.199.205 |
During the analysis of the network traffic, it was identified that the exchange of information between the malicious sites and the infected computer was carried out using an obfuscation process, so the information was not exchanged in clear text. The traffic captured when the infected computer uploaded data to a malicious site using the POST method, can be seen on the image below.

Given that the malicious software collected the access credentials to FTP and mail services, it is likely that the information had been sent on the previous request.
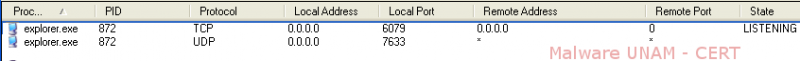
It is important to emphasize that the malicious file injects itself into the process explorer.exe to be able to go unnoticed for the user. This process works as a backdoor on the infected system because it habilitates two ports: one on tcp and one on udp.
To assure its execution on every system startup, the malware creates the registry key “HKCU\Software\Microsoft\Windows\CurrentVersion\Run”, which starts one of the downloaded files.
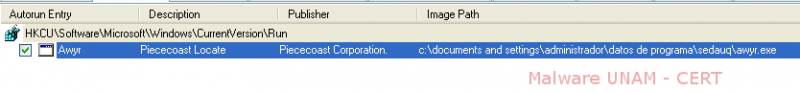
As for the file system, it was observed the modification of the firewall policies to allow communication on the local ports 6079 and 7633, which corresponded to the process explorer.exe. It was also observed the creation of a registry key to start the file awyr.exe on every user login.
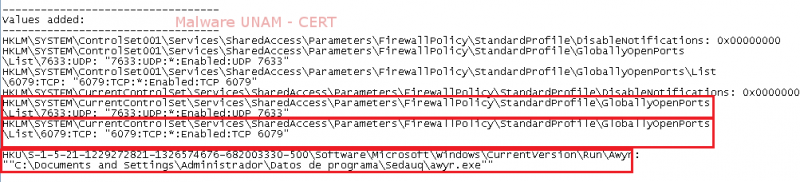
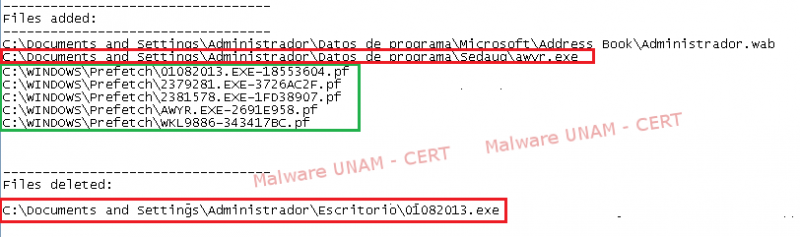
Multiple files with extension “pf” were added, these referenced files of type “Prefetch” and correspond to the malicious files downloaded and started. As it was expected, the malicious file awyr.exe, for which a registry key was added, was also created.
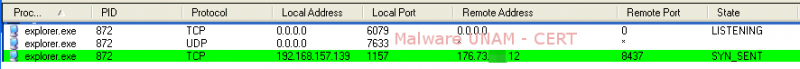
After restarting the system, it was observed that the process explorer.exe initiated itself again, habilitated the TCP port 6079 and the UDP port 7633 and established communication with a malicious site, as shown below.
The captured network traffic displays that the communication follows the same pattern to obfuscate the information exchanged; hence, it was not possible to determine the type of information transmitted.
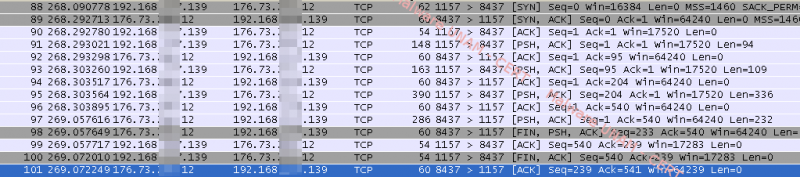
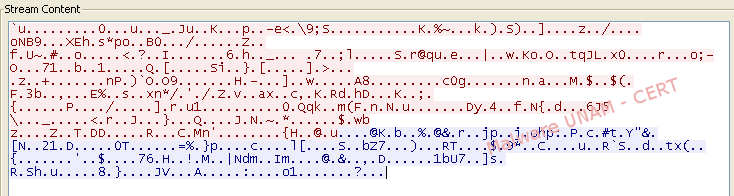
This same process was observed for each of the sites on which a successful connection was established.
The detection rates obtained from the VirusTotal website is shown below:
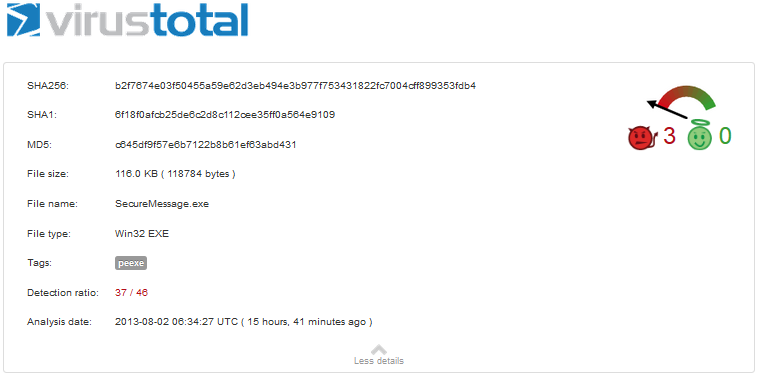
The full report can be found on the following link:
It is important to mention that if you want to use a FTP service, you have to uncheck the option that saves the access credentials, due to the fact that these are usually stored in plain text, which makes it easier for malicious programs to steal these data and subsequently use it to access the corresponding servers.