Linux machines infected by bots
UNAM-CERT received a report about an allegedly malicious file for Linux operating systems. According to the complainant, the system presented low performance and strange behavior; so we proceeded to analyze the sample.
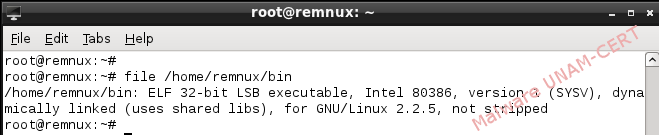
With the file command we observed that the file was of type ELF (Executable and Linking Format), which is the file format for executables in Linux. The LSB string references the memory storage mode, in this case it is “Little-Endian”. Another characteristic observed was that the file was compiled for the Intel 80386 architecture.
First, we proceeded to make the analysis of the strings to obtain useful information about the behavior of the sample. The strings shown on the image below, served as a guideline to determine that the sample was a bot that tried to establish a communication with an IRC channel. IRC channels are commonly used by malware so that, once a machine has been infected, it can report to a C&C (Command & Control) and wait for the orders that must be performed.
We also found the strings shown below, which seem to be the instructions that the infected computer executed to join and communicate with the IRC channel.
References to some files (randsignoff.e, randaway.e, randkicks.e, randversions.e) were also found, as seen on the image below. Apparently, these files were stored in the same path as the executable file. However, the Incident Response Team could not recover these files due to the fact that they had been deleted remotely.
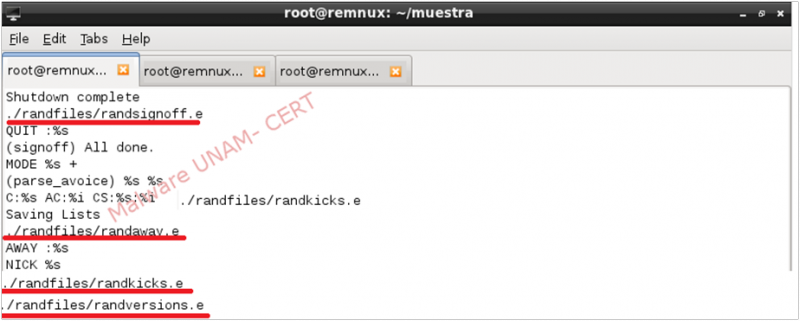
The string “EnergyMech” and the domain of the server to which the sample seemed to establish communication, were also found.
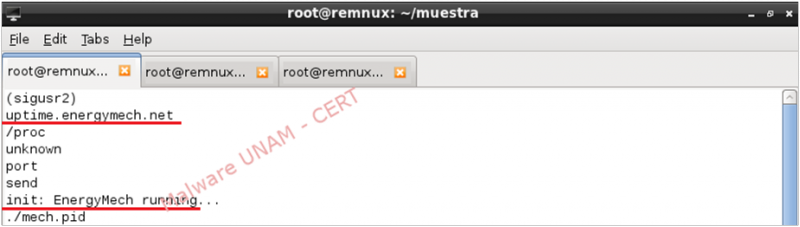
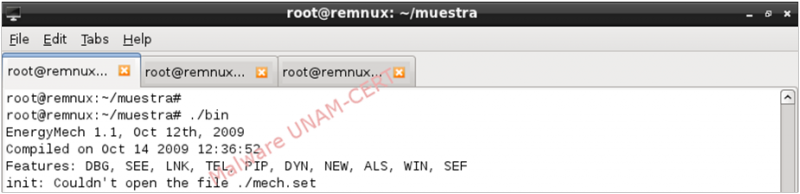
Subsequently, we proceeded to execute the sample. The dynamic analysis showed that the analyzed sample corresponded to the EnergyMech IRC Bot version 1.1, compiled on 2009.
It attempted to open the mech.set file, which seems to be the configuration file of the malicious sample and, as shown on the image below, it prints a message indicating the file could not be opened.
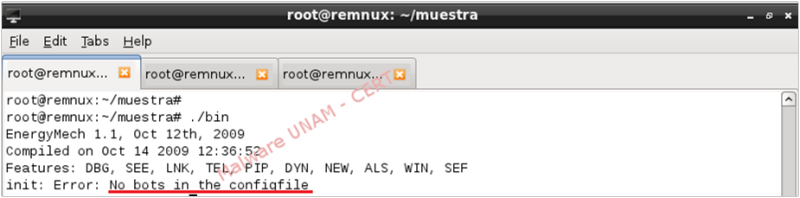
We created the file mech.set to observe the behavior of the executable when the file was available. Because the file was empty, when we executed the sample, we received a message indicating there wasn't a configuration in the created file.
We looked for the configuration files on the Internet and we found what seems to be the website of the toolkit used to create the bot. It was developed in C language for Linux operating systems and was distributed under GPL license.
The website in question is completely dedicated to the development of this IRC Bot. It includes tutorials on how to compile and configure the software, along with the files needed for the proper operation of the malware. Thus, we proceeded to download the appropiate configuration file, rename it to mech.set and execute the sample. It is worth mentioning that the actions that could be carried out by the malware with this configuration file might not be the same as the ones established by the attacker who infected legit hosts, it's just a proof of concept to measure the reach of this threat.
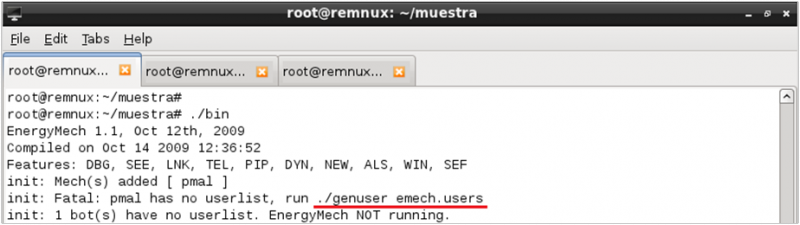
After the execution it displayed a message indicating that the lists of users needed was not found. The sample also provided the instruction to generate the list. When the configuration file, called emech.users, was generated, the sample was executed again. Since the configuration was now correct, the next message was displayed:
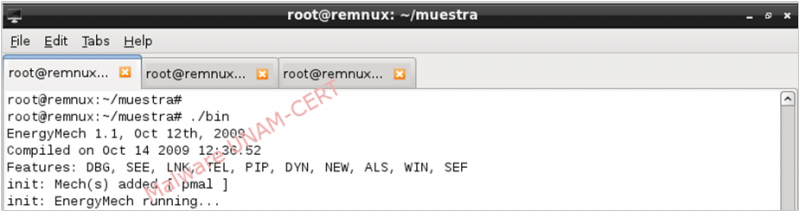
However, no network activity was detected; even when the port used to establish the connection was specified on the configuration file.
The signature of the malicious sample is shown below.
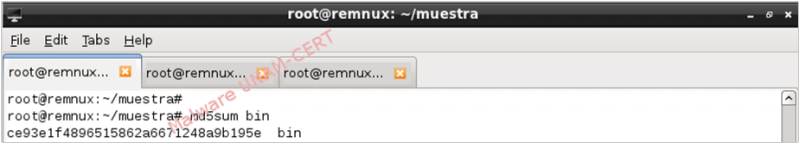
We used the signature to find information about the sample on VirusTotal. The results obtained show that only one out of 46 antivirus engines detects the sample as malicious.


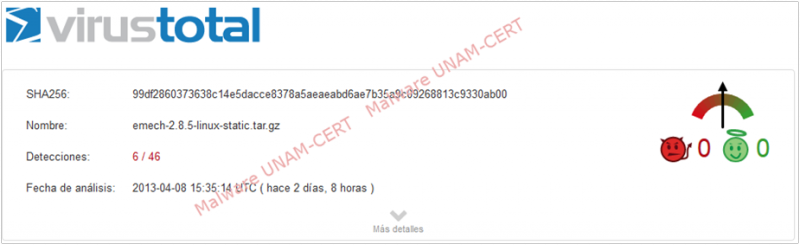
Meanwhile, when analyzing with VirusTotal the compressed file that was downloaded from the website that distributes this program, we obtained that the sample was only detected by 6 out of 46 antivirus engines. The results can be seen on the image below.
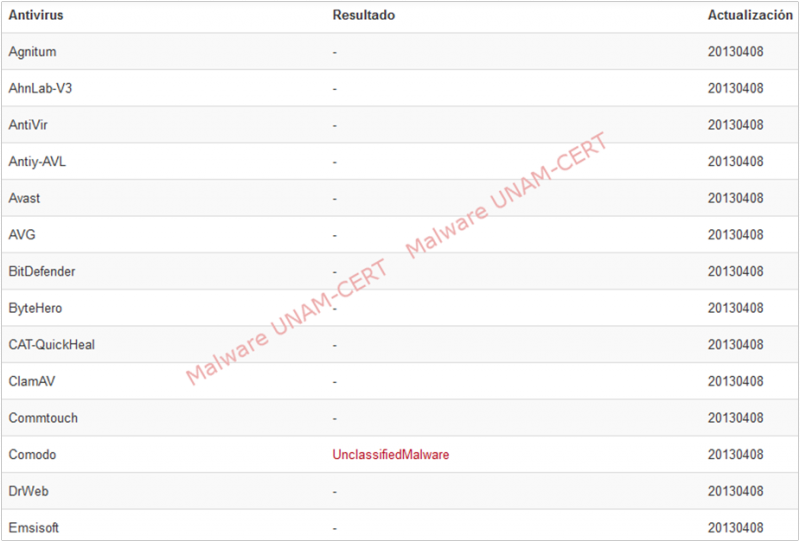
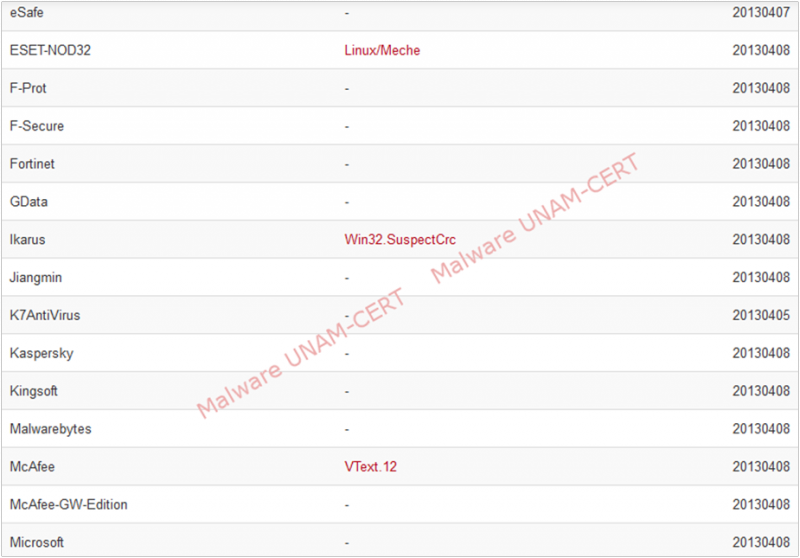
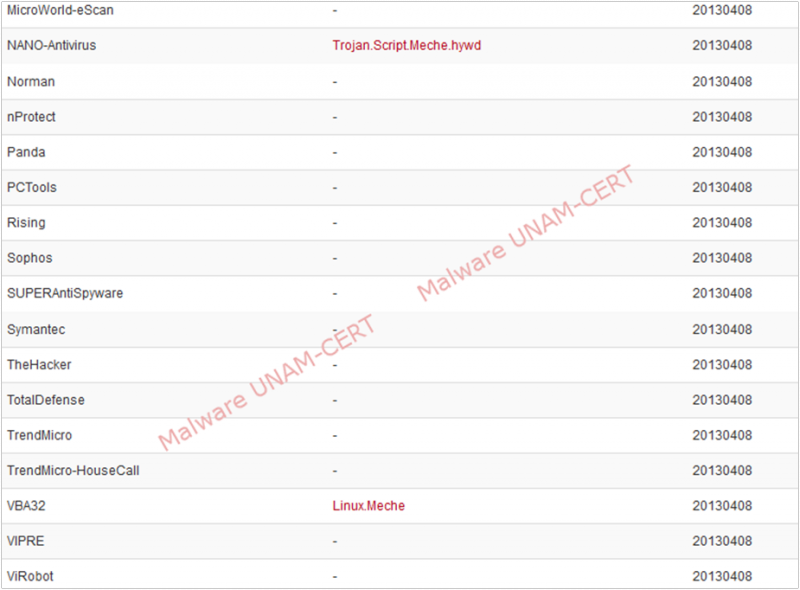
Given that we could only obtain the binary file and not the configuration files of the infected host, we could not determine the malware's original objective. It could have been used as a backdoor in order to access the infected system, this with the intent of extracting sensitive information from the hosts.
According to some reports, provided by the Antivirus that were able to detect the sample, the malware is generally located in the /etc/rc.d and /etc/init.d directories, which contain files that are excecuted at boot. It is, therefore, important to examine these directories periodically, in order to detect any inconsistency. It should be noted that these files are preceded by a period (.filename) as a way of avoding detection.