UNAM-CERT received a notification about a suspicious web site that leads to the installation of new Java software.
In the past few days, actualizations of the well-known Oracle software has been a trending topic, for both IT professionals and users all around the world, due to recent security flaws that have come to light, exposing users safety.
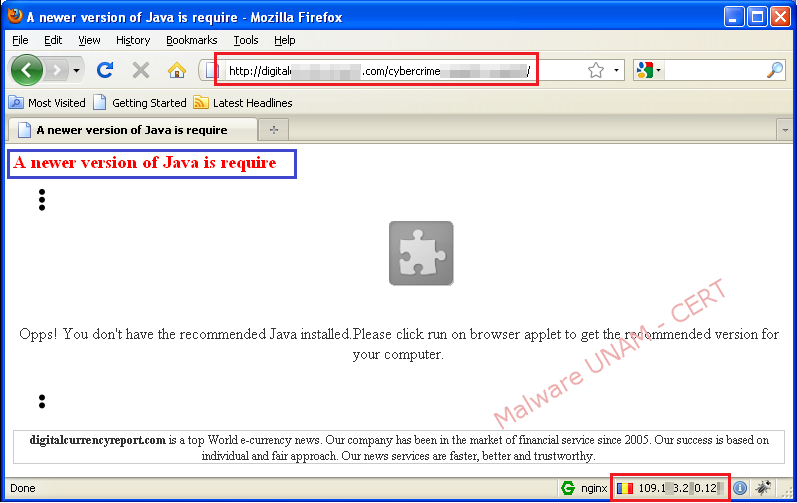
The web site, hosted in Romania, contained a link that when selected, starts up an applet with the name “javaupdate11”.
Applets are programed in Java language; they can be integrated to HTML files as a new element of web sites and also they can be executed on browsers.
Any person which does not take the enough cautions and decide to push the “Run” button will compromise their computer.

Applets need to have the Java plugin installed on the web browsers, and they begin the process when Java Virtual Machine (JVM) is running.
Therefore, the browser process “firefox.exe” start up the legitimate process of “Java”.

When connection is established, the file “javaupdate11” executes itself, downloading and executing a new file named “up1.exe”.
The same site that hosts the applet is the one that performs the download.

Next, there is another download, a file named “up2.exe”.

After a few seconds, the program in execution “up1.exe” opens 8000 port on LISTENING mode, leaving with them, in the infected host, a backdoor.

A Prove of Concept was made just to verify how the malware author could obtain a Command Line Interface (CLI) of their victims.

Finally, in terms of process activity, the file “igfxtray.exe” is downloaded and executed; this process establishes a connection with a remote server on port 3360.
The connection, by the time of this analysis, did not generate malicious net traffic.

In terms of registry activity, the sample creates a key with the name “SunJavaUpdateSched” to keep the execution of the binary “svchost.exe” on every startup.
It’s noteworthy that the file “svchost.exe” didn’t make any malicious activity.

In the image below there is shown the record of the files created by the infection, the report was generated with the RegShot tool.




During the infection process, some changes were made on the configuration file of Firefox web browser. One of them is the JavaScript file “pref.js”. In this file are stored the preferences of the user session. Other file is “sessionstore.js” that contains open tabs and open windows.


A list of the created folders is presented below:


Once the network activity and the created processes by the sample have been analyzed, we proceed to download the malicious web site.
Only two file were downloaded, “index.html” and “javaupdate.class”.

On the HTML code shown by the malicious website, we can appreciate the messages that the author of the applet has employed to trick their victims.

Also, we can identify the <applet> label used to load the “javaupdate11.class” code.

By decompiling the class file, we can see the source code of the original Java file “javaupdate11.java”.
The malware author forms the URL, to start the download once he has infected the user. The complete direction for the download is stored in variable “str7”, which is transferred a posteriori to the “download()” function.

A few hours later, the website that hosted the Java applet, changed their HTML code to show the next message:

Finally, we consult the “VirusTotal” service, and the next report was generated:




UNAM-CERT strongly recommends to every user to take extreme precautions when visiting websites that contains indications to installing the latest version of specific software. Most of the times, the tricks are focused on web browsers complements, for example: Adobe Flash Player, Java Runtime Environment, Adobe Shockwave Player, and other trends. It’s necessary to apply common sense in these situations, so this way we can prevent malware infections.
Sometimes this kind of software, like Java plugins and their respective updates are needed to watch animations on web browsers, but similar situations than these, we must download the software form official websites.













