Executable file Downloads_D modifies registry keys
We received an email with an executable called Downloads_D.zip, which contains a file called Downloads_D.exe.
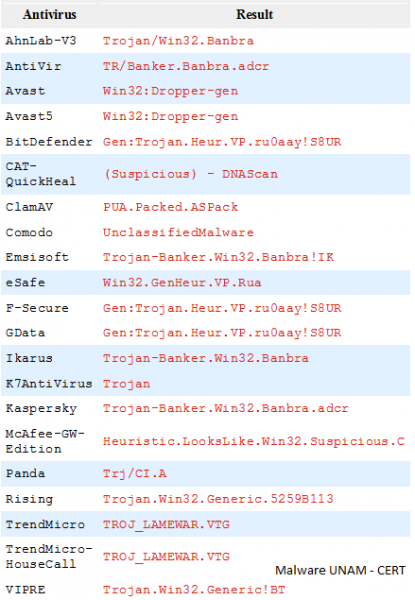
Analyzing it with antivirus engines showed that is a Trojan and allegedly steals information of a bank.
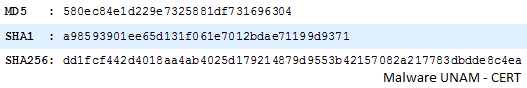
The executable file has the following MD5 and SHA1 hashes:
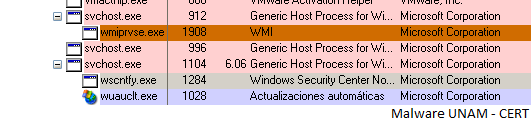
After analyzing it with commercial virtual labs, it did not make any modification. However, analysing it with CERT Lab (Sandnet), it made modifications in the file registry, as well as the creation of a trojanized process of svchost.exe.
Svchost started a script called wmiprvse.exe, as shown in the following image:
This process opens the TCP port 1105 and let it listening. It also modifies some characteristics about security in Windows regard to the handling of ciphering algorithms because it modifies the registry key
HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Ciphers
Some of the most important registry entries are the following:
HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Ciphers\DES 56/56 HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Ciphers\NULL HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Ciphers\RC2 128/128 HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Ciphers\RC2 40/128 HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Ciphers\RC2 56/128 HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 128/128 HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 40/128 HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 56/128 HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168/168 HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Hashes\MD5 HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Hashes\SHA HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\KeyExchangeAlgorithms\Diffie-Hellman HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\KeyExchangeAlgorithms\PKCS HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Protocols\Multi-Protocol Unified Hello HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Protocols\Multi-Protocol Unified Hello\Client HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Protocols\Multi-Protocol Unified Hello\Server HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Protocols\PCT 1.0\Client HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Protocols\PCT 1.0\Server HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client HKLM\SYSTEM\ControlSet001\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server
According to Microsoft Information, these registry values are modified to deactivate some kind of ciphering in the computer, probably the author's malicious code is trying to deactivate the ciphering algorithms.
The malware did not perform any other modification.