Email that redirects to a phishing site of the Afirme Bank
SSI/UNAM-CERT received a report about a website that attempted to fake the portal of the Afirme financial group.
On the content of the email there was a link to the alleged website, as shown below:
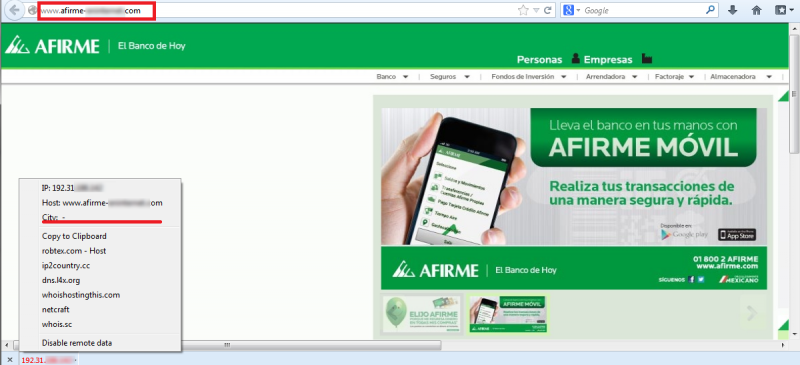
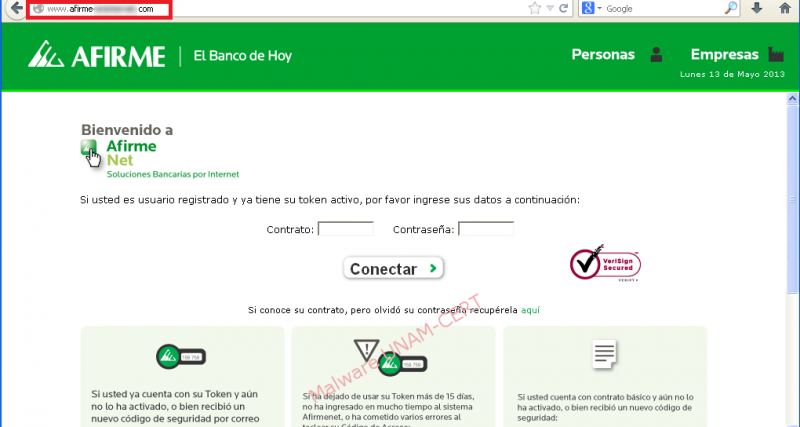
After the link is clicked, the user is redirected to the fake site of the Bank. As it can be observed, the URL contains the word “afirme”, to avoid suspicions and make the user think that the site is legitimate.
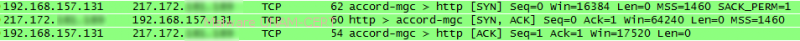
Interestingly, Firefox’s plugin could not determine the country of the server hosting the website. However, after analyzing the network traffic, we could observe the IP address of the website that makes the requests.
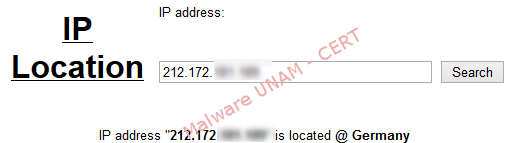
By using the iplocation.pythonclub.org, we obtained the possible location of hosting server.
After clicking on the main site, a new web page loaded and requested information to confirm that the user is registered on the website.
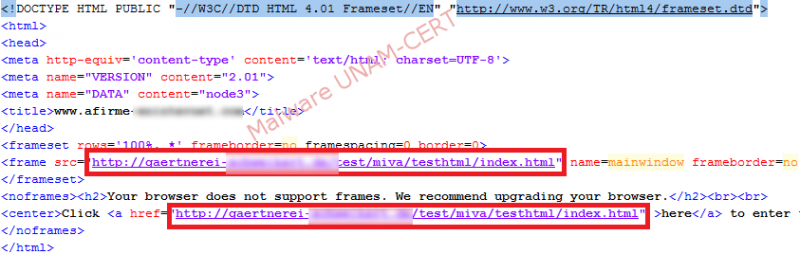
The source code of the site does not present any kind of obfuscation; therefore, the domain used to establish communication can be easily observed.
After introducing the test credentials, the network traffic was monitored to verify the domain to which the data was sent.
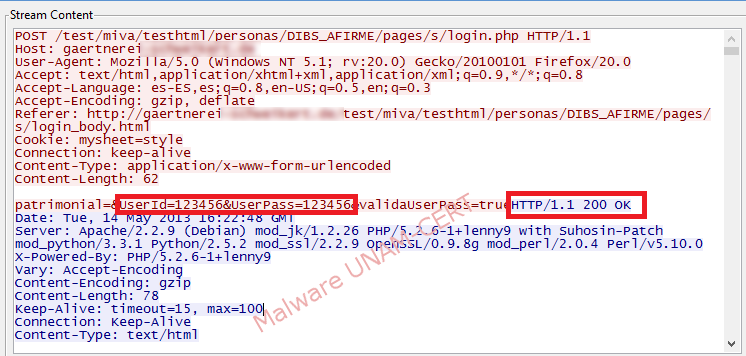
On the image above, the credentials introduced, its validation by the phishing website and a response code of 200, can be observed. From this response we could identify that the site was hosted in an Apache server that used different modules, such as: perl, python, php, etc.
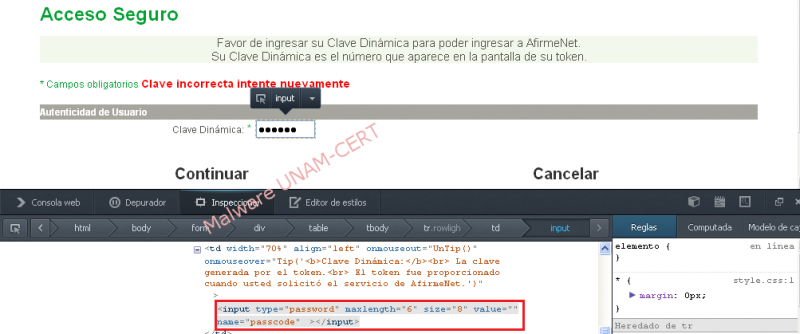
When the credentials were validated, the website displayed a new form that asked the user to type a dynamic key. The portal attempts to validate the key and if it fails, it incites the user to try again.
By using the browser’s development tools, we could observe that the length of the key was of 6 digits.
When the key got validated, a new page loaded. This time it asked for personal data, such as the user’s name and telephone numbers.
On the image below, the network traffic captured during the shipment of the key is shown.
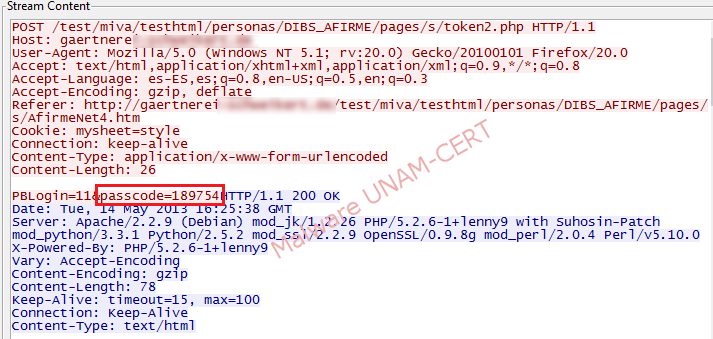
During the analysis, it was also found that the site presented a one day lag respecting the day of our analysis; probably because it was hosted on a country with a different time zone

After the data was introduced and validated, it was sent to the server that hosted the malicious site. On the next image, the data we introduced can be seen in red.

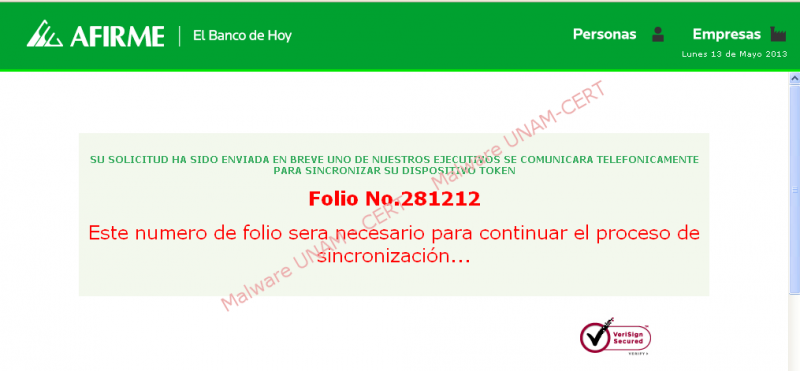
Finally, the website displayed a message saying that personal from the financial group will get in touch with the user.
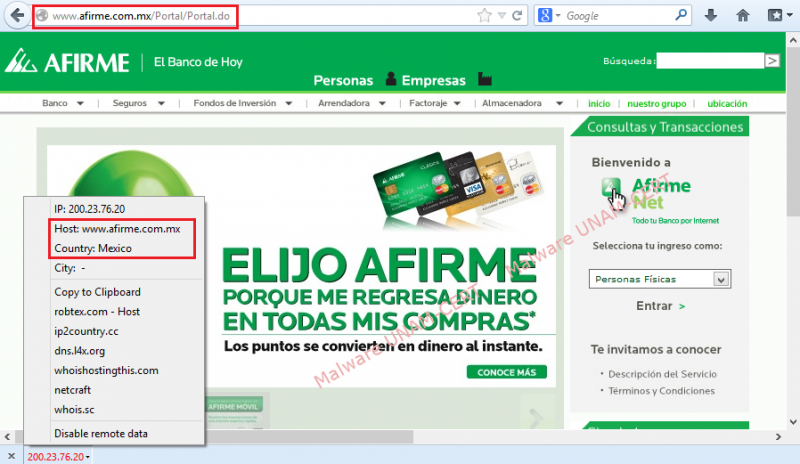
A screenshot of the legitimate Afirme website is shown below, with the URL and the country that hosts the website shown in red.
It is recommended to avoid clicking on the links received by email, especially when it comes to banking institutions; due to the fact that it is quite common to encounter a fake site and to download some kind of malicious software that could compromise the computer