Email leads to Trojan download
Recently, UNAM-CERT received a notification about an email that informs the user that he/she has been recently sued. Two PDF files are attached to the email, supposedly explaining the reasons of the demand. Below the email body:
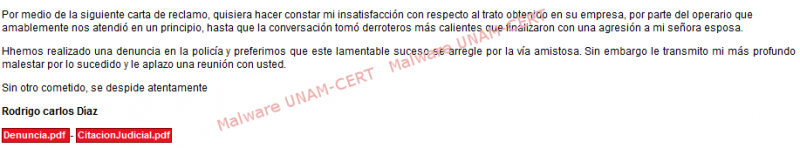
By clicking on the file links, a redirection was made to two different sites hosted in different servers, leading to the download of the same file in ZIP file format on both of them.
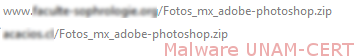
After downloading both files, it was verified that they were indeed compressed files. This is because attackers often change file formats of executable files, in order for the user to run it.
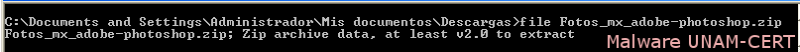
When unzipping the file, an executable file was obtained with the name “Fotos_mx_adobe_photoshop.exe”. Again, the file was verified in order to corroborate its file format, by using “file” command.
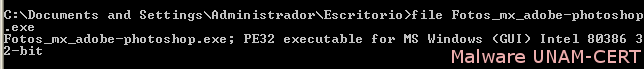
The malware sample was analyzed in a controlled environment. After the sample was executed, it only shows network traffic behavior. And the only process that starts up in the system it’s itself.

Network traffic shows that 3 requests were made to external servers, as it is shown below:
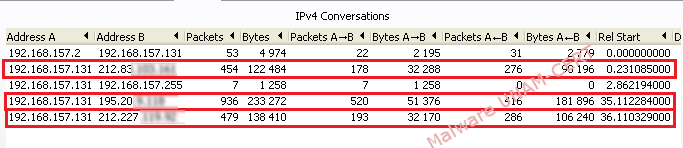
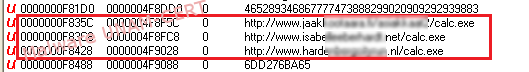
After analyzing network traffic, it was observed that GET requests were made in order to download a second executable file called "calc.exe". Also, network traffic shows a request to download the same file. In this way, it was found that one of the sites was still online. Probably the site was compromised in order to store malware, since the page was totally legitimate. The second domain was registered but it didn’t show any available resource and therefore “calc.exe” file couldn’t be downloaded.
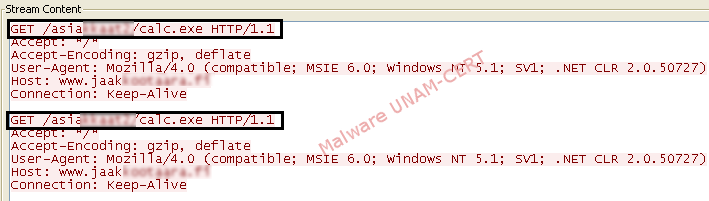
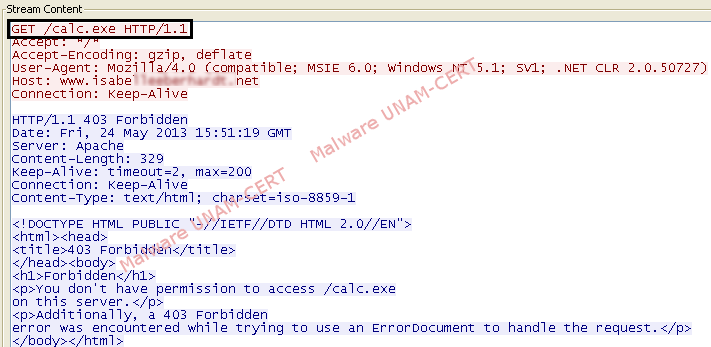
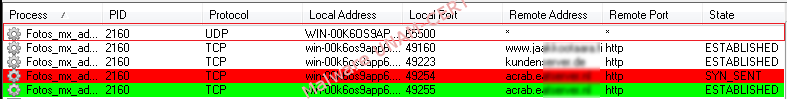
Although the sample was unable to download further malicious code successfully; it’s important to note that a backdoor was created which uses UDP protocol on port 65500. Recently has increased the use of backdoors through UDP protocol, this is because there is no need to create a session between the infected computer and the attacker in order to send instructions to be done.
The sample was packed using UPX tool, action whose purpose is to hinder code analysis.
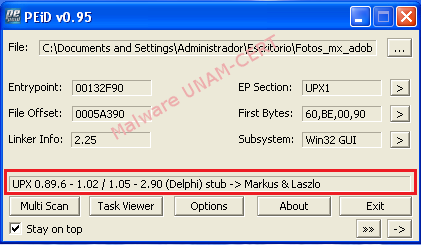
The process to unpacking the malware sample is shown below:
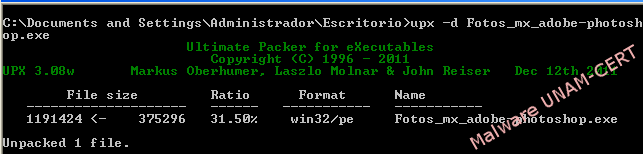
Using PEiD tool, it is confirmed that the sample of malware has been unpacked.
The string analysis allowed UNAM-CERT members to observe the strings that refer to the websites where the malicious file “calc.exe” was hosted.
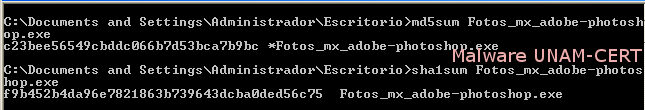
Md5 and Sha1 firms of the infected files are shown below:
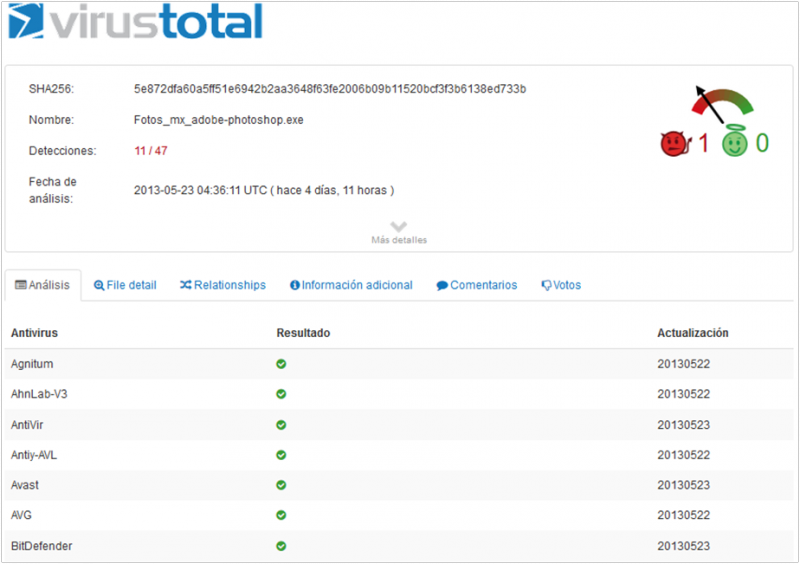
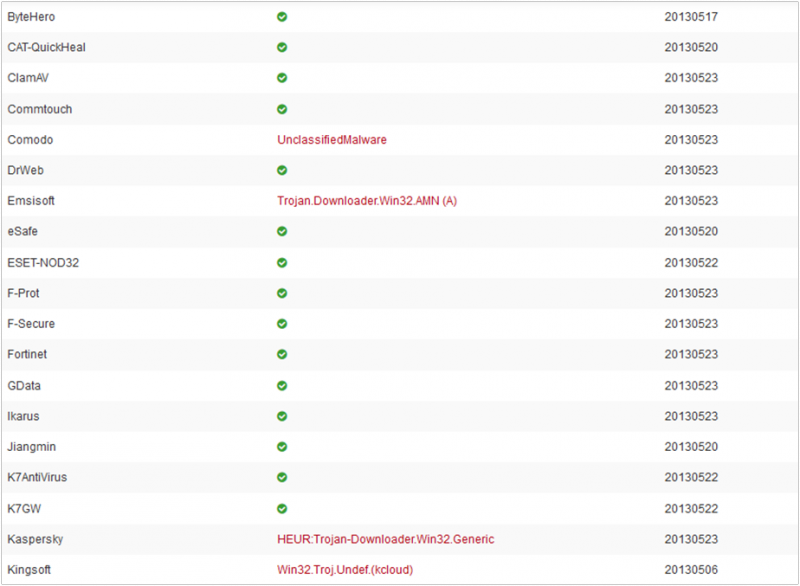
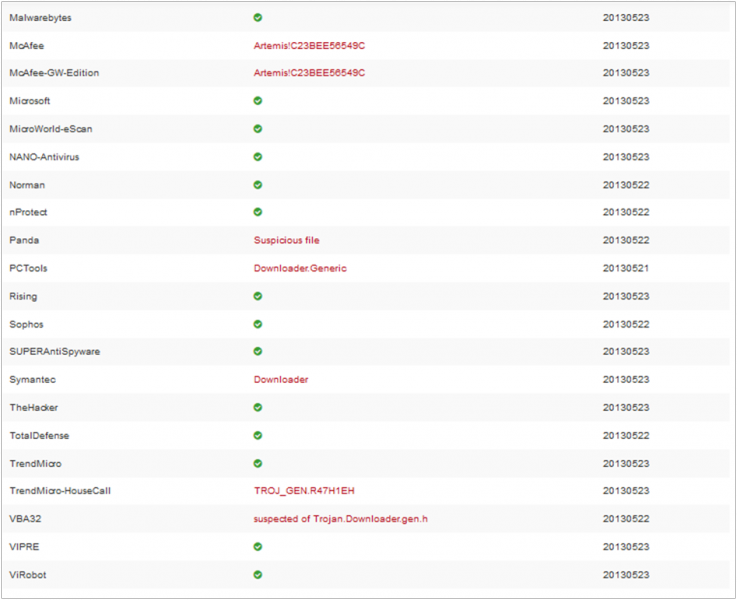
Below is shown the report of VirusTotal service:
UNAM-CERT recommends all users to be cautious with suspicious links and attachments, because this is one of the most common methods to distribute malware.