Cameron Diaz's sister, spreads fake AV through pictures
At the end of 2010, the security company McAfee published a list (see article) about the most dangerous celebrity names to search on the web. In first place was Cameron Diaz because the provided results by popular engines search, of pictures, screensavers and some common notes related to the actress, conduct to malicious code spreading, mainly, a fake antivirus that alerts users of supposed threats in their computer.

Yesterday, with almost five months from the year beginning, and later to McAfee list publication, we found these same threats, but now, searching images of Cameron Diaz's oldest sister, Chimene Diaz.
This kind of attack uses a technique known as SEO poisoning or Black Hat SEO. In the Security Threats Report of 2011, published by the security company Sophos, is explained that cybercriminals are able to manipulate searching results provided by searching engines of companies such as Google, Microsoft or Yahoo.
The genuine SEO (Search Engine Optimization) techniques, are used generally as marketing tools, to generate traffic on the websites because these appear in the first positions on searches, incrementing the probability of users visit them and as a consequence, to generate more profits. But when these techniques are used by cybercriminals, the searching results are “poisoned” in such manner that when a user click on some link, it is redirected to sites storing malicious codes or another kind of code able to exploit some browser vulnerability, which, could affect a user, stealing personal or financial information, adding its computer to a botnet.

For that reason, when clicking on any of the resulting images, was specially established a redirection to a created site to fool users, simulating carry out a system scanning.
In first instance, it appears a window warning about alleged detected threats and the necessity of an urgent scanning.
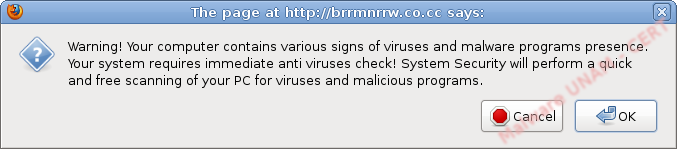
No matter what button is clicked, the fake scanning starts. The interesting thing, is that the site simulates being part of user's SO Windows Explorer, on this case seems to be in Windows Vista or Windows 7 and shows a scanning progress bar.
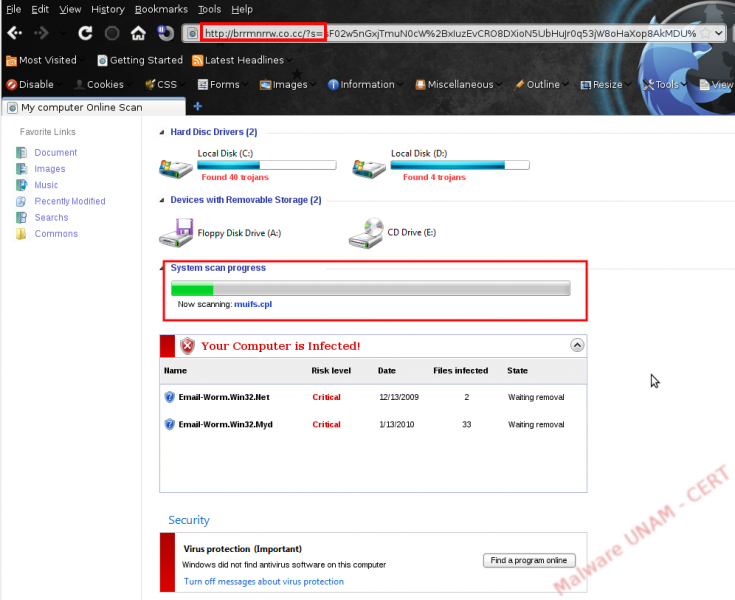
When finishes, it appears a windows seeming to be a notification of Windows Defender Tool, which alerts to the user that was detected spyware and it could be removed from the computer.
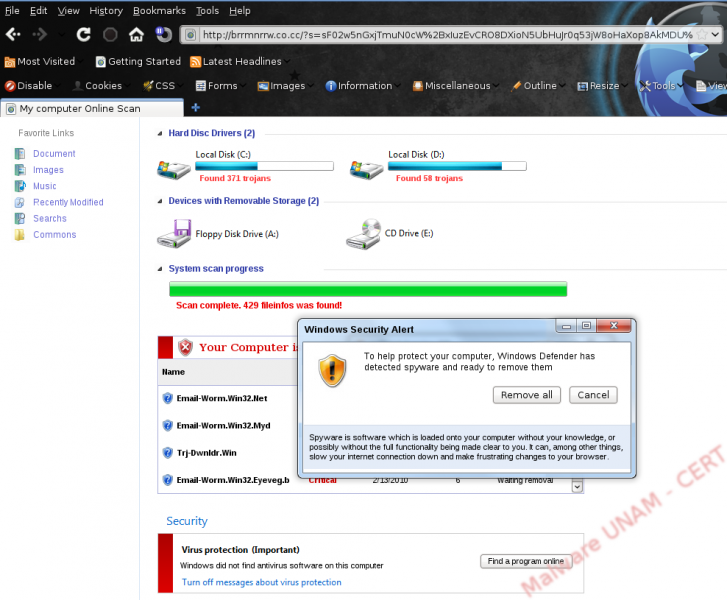
Again, no matter in what position on the alert is clicked, it appears a window to download the executable SecurityScanner.exe, which so far, is just detected by four antivirus.
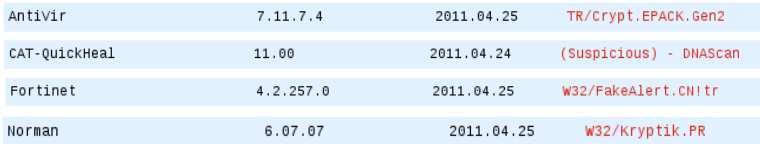
Its hashes are shown as follows:
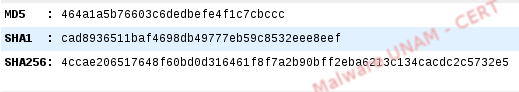
If the user executes the SecurityScanner.exe file, the firewall will be disabled, as well as the automatic updates and the antivirus protection since the Computer Security Center and it is automatically executed the XP Home Security 2011 application and the computer scanning starts.
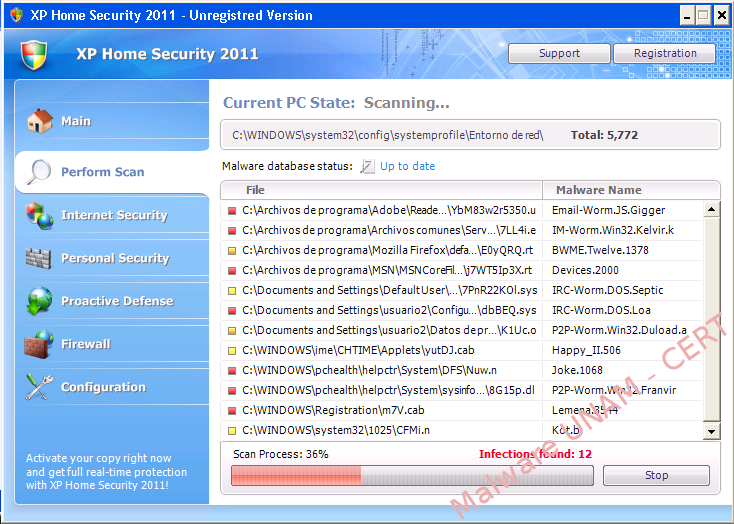
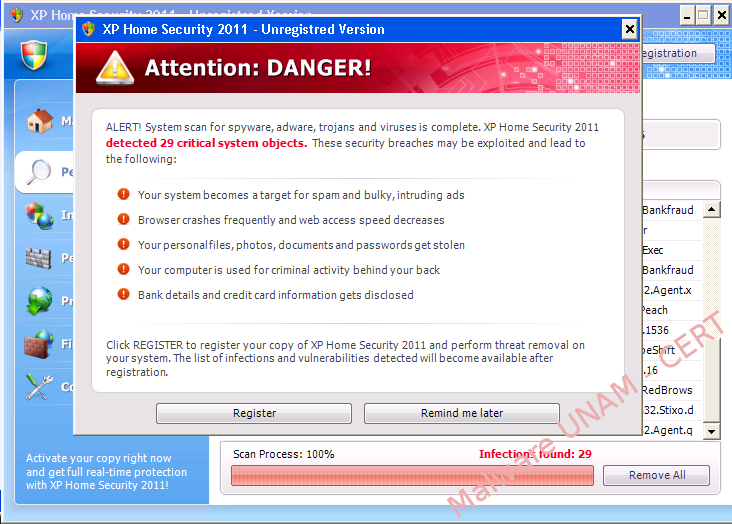
When the alleged scanning finishes, it shows a window, which mentions that were recognized 29 threats and in order to remove them, it is required to register the product.
Then, it opens a browser from the alleged antivirus application and shows a page with the different license prices for the product.
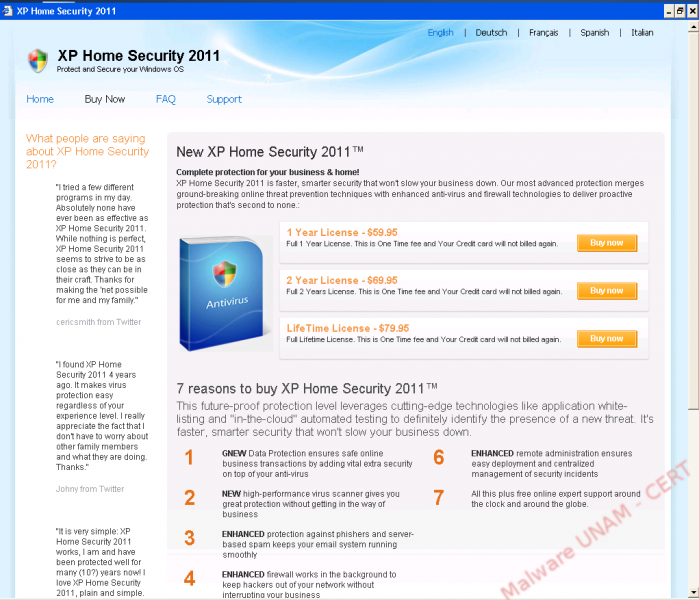
As part of the analysis, we select a one-year license and it shows us a form to be answered with financial and personal information to carry out the buying. We did it with fictitious information and when trying to perform the transaction, it throws us an error.
On the system, were created several files, such as:
C:/DocumentsandSettings/<usuario>/Configuraciónlocal/Datosdeprograma/ste.exe
This file belongs to the same executable, but is renamed and it can be distinct with each execution.
- C:/DocumentsandSettings/<usuario>/Cookies/<usuario>@fequxukovo[1].txt
This file is created when the user access the web site to buy the product, as well as the form.
Moreover, the ste.exe file is responsible for starting a process with the same name and this process starts the fake application XP Home Security 2011.
It also modifies, the Windows registry, so that each time is opened the Firefox or Internet Explorer browser, is executed the malicious application.
Modified registry keys and values:
- [HKLM\Software\Clients\StartMenuInternet\FIREFOX.EXE\shell\open\command]
Created registry values:
@="\"C:\Documents and Settings\usuario2\Configuración local\Datos de programa\ste.exe\" -a \"C:\Archivos de programa\Mozilla Firefox\firefox.exe\""
Deleted registry values:
@="C:\Archivos de programa\Mozilla Firefox\firefox.exe"
- [HKLM\Software\Clients\StartMenuInternet\FIREFOX.EXE\shell\safemode\command]
Created registry values:
@="\"C:\Documents and Settings\usuario2\Configuración local\Datos de programa\ste.exe\" -a \"C:\Archivos de programa\Mozilla Firefox\firefox.exe\" -safe-mode"
Deleted registry values:
@="\"C:\Archivos de programa\Mozilla Firefox\firefox.exe\" -safe-mode"
- [software\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command]
Created registry values:
@="\"C:\Documents and Settings\usuario2\Configuración local\Datos de programa\ste.exe\" -a \"C:\Archivos de programa\Internet Explorer\iexplore.exe\""
Deleted registry values:
@="\"C:\Archivos de programa\Internet Explorer\iexplore.exe\""
- [HKLM\Software\Microsoft\DirectDraw\MostRecentApplication]
Created registry values
"Name"="iexplore.exe"
"ID"=dword:41107b81
Deleted registry values:
"Name"="AcroRd32.exe"
"ID"=dword:4b309800
- [software\Microsoft\Security Center]
Created registry values
"FirewallOverride"=dword:00000001
Deleted registry values:
"FirewallOverride"=dword:00000000
When analyzing the generated traffic, we could determine the site where can be bought the application.
- hxxp://fequxukovo.com/buy.htm
- hxxp://fequxukovo.com/checkout.html?on

And capture data when is processed by the form:
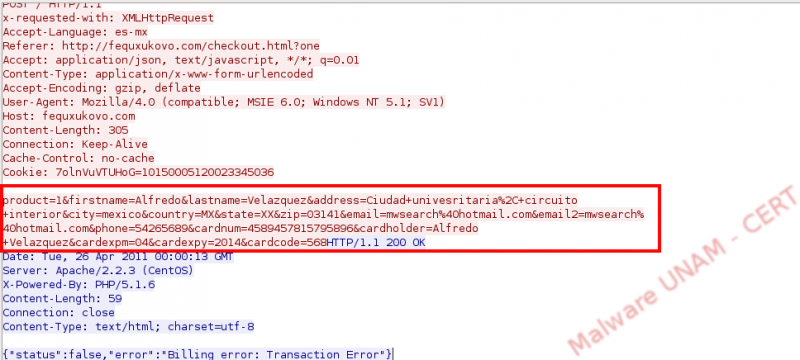
This kind of attack can cause a great impact, specially to less experimented users because they take advantage from generated fear on them, to accomplish its objectives. It is important to consider that Windows Explorer, in other words, the interface that allows us to see our folders, files, disk units and usage percentage, will never be available in a web browser neither it shows us a progress bar nor a message warning about possible detected threats in the computer.