The banking trojan Banload and its techniques to evade security software
Abstract
Out of all the samples received during the last few weeks, the Visual Basic scripts (.vbs or .vbe) are the ones who caught our attention. In this report, we analyze a Visual Basic file that was coded with a legitimate Windows program to hinder its analysis. The analyzed sample is the first infection stage and its purpose is to download and, in some cases, assure persistence of additional modules or updates of the trojan; in addition to uninstalling the security software used in the computer (such as antivirus or banking plugins) and creating firewall rules to block the network traffic related to such executables in case the uninstall fails.
Introduction
As mentioned on the reports about the phishing received at UNAM-CERT, during the last few months we have seen a campaign of emails informing the user about an alleged investigation of the Federal Police (Procedimento Investigatório in Portuguese). This include titles with an ID, such as the one shown below, that reference fragments of the “Federal Constitution” (Constituição Federal) to make the user believe it is a legitimate warning.
Intimação Procedimento Investigatório Policia Federal nr <year><month><day>5641541BR (<number>)
The email that contained de download link of the analyzed sample can be seen at the start of this post.
When clicking the alleged attachment (“anexo” in Portuguese), the browser redirects to a Google Drive account from which the malicious file is downloaded.
The downloaded ZIP file contained the script “Bonus20reais_PDF.vbe”. Because of the extension, it is known the file is a Visual Basic script coded with the command screnc for Windows and, therefore, if opened with a text editor only random characters will be seen.
Once decoded, even though it was possible to identify some lines of code, it was necessary to rename variables and functions to make the script readable. A fragment of the decoded script is shown below.
Static Analysis
Below, the relevantaspects of the functioning of the script are explained.
1) Reads the registry key HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProductName to identify the version of the operating system. If it is Windows 7, Windows Vista or Windows 8, the script executes again using wscript, except this time with administrator privileges.
2) Adds the string “RR” to the end of the file C:\Windows\<Nombre_del_Equipo>_Part.rri.
3) If the file C:\Windows\idx doesn’t exist, it creates it, otherwise it stops its execution.

4) After that, the script creates some scheduled tasks with the command schtasks, all of them execute once with the user SYSTEM, at different times and with the same identifier (0CE4BD10-B60E-49E4-93A5-7415FFD761CC, now referred to as “ID”) as part of its name. These tasks execute the cmd commands explained on the following table:
|
Task |
Execution |
Actions |
|
{ID} |
9 minutes after the start of the system |
Downloads a file from hxxp://xxxdownload1.com/up.jpg with the command bitsadmin. The downloaded file is stored in C:\Windows\<random_number>.tmp and later executed with rundll32.exe. The URL gets stored in the environment variable “UPLKVARIABLE”. The name assigned to the downloaded file is stored in the environmental variable “upvariable”. |
|
{ID}1 |
4 minutes after executing the script |
Downloads a file called mod1.jpgfrom a remote server with bitsadmin. This file is stored in C:\Windows with the name %COMPUTERNAME%.tmp. Adds a value with the name of the computer to the registry key HKLM\Software\Microsoft\Windows\CurrentVersion\Run and adds the command “rundll32 %SYSTEMROOT%\%COMPUTERNAME%.tmp,#1” as the data. |
|
{ID}2 |
3 minutes after executing the script |
Downloads the filepart.jpg from a remote server with IP address 167.xxx.131.179 y stores it in C:\Windows\<nombre_del_equipo>_Part.exe. Adds the string "autocheck autochk *\0 \0%SYSTEMROOT%\%COMPUTERNAME%_Part.exe\0"to the registry key "HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\BootExecute”. The value “autocheck autochk” forces a system scan during startup. In this case, what the malware does is to take advantage of the fact that other values can be added to the subkey “BootExecute” to make the malicious file SYSTEMROOT%\%COMPUTERNAME%_Part.exe execute since the system starts. Adds the subkey HKLM\SYSTEM\CurrentControlSet\Control\Partizan. (1) (2) (1) The first part contains the information to control the system startup. (2) Partizan is an anti-rootkit part of the Russian edition of the program UnHackMe. During startup, it scans the system to uninstall the files specified on the file with extensión “rri”. |
|
{ID}3 |
14 minutes after executing the script |
The task deletes itself and reboots the system after 60 seconds. |
|
{ID}4 |
2 minutes after executing the script |
The task deletes itself and opens the URL hxxps://contxxx.whelaxxx.net/infects/mk.php?url=[Plugin][%COMPUTERNAME%]-cn- on the default browser. This process repeats with the URL hxxps://contxxx.whelaxxx.net/infects/mk.php?url=[N/A][%COMPUTERNAME%]-cn-. |
In addition, it checks the value of the registry key HKLM\SYSTEM\ControlSet001\Services\GbpSv to know if “G-Buster Browser Defense-Service”, which is a security program used by the clients of the Brazilian banks Caixa Econômica Federal and Banco do Brasil, amongst others.
----- GBPLUGIN y Warsaw -----
5) Firewall rules are created to block incoming and outgoing network traffic of all executables and DLLs found in %PROGRAMFILES%\GbPlugin\ and %PROGRAMFILES%\Diebold\Warsaw\. Warsaw is also a security plugin developed by GAS Tecnologia to make trustworthy the electronic transactions of some Brazilian banks (…).
----- ANTIVIRUS -----
Several antivirus products support the integration with WMI (Windows Management Instrumentation), which is an infrastructure to manage data and operations of the Windows operating systems and that Windows Security Center uses to detect the AV and firewall solutions installed on a computer. Windows Security Center monitors the “health” of the system, for example: updates and the configuration of the firewall, antivirus or antispyware.
If the AV product registered its data with Windows Security Center, there will be information related to the application (name, unique identifier, path, state of the protection in real time and state of the malware definitions) in one of the two WMI namespaces of the Security Center: \root\SecurityCenter (pre-Vista versions) or \root\SecurityCenter2 (post-Vista versions). In this case, the script only executes in Windows Vista, 7 or 8 and, therefore, consults \root\SecurityCenter2. Inside of it, is the class AntiVirusProduct.
6) The script checks the content of the class AntiVirusProduct through the query “Select * from AntiVirusProduct”. For each AV product the script: searches for executables in the subfolders, obtains path and name and stores that string in %SYSTEMROOT%\%COMPUTERNAME%_Part.rri. It then adds rules to the Windows firewall to block inbound and outbound network traffic related to the AV.
Dynamic Analysis
Once the plugins Warsaw and G-Buster were installed on the lab, the file Bonus20reais_PDF.vbe was executed to analyze its behavior.
· Process Tree
- wscript.exe
- --cmd.exe
- ------conhost.exe
- ------schtasks.exe
- --cmd.exe
- ------conhost.exe
- ------req.exe
- --cmd.exe
- ------netsh.exe
- --cmd.exe
- ------setx.exe
· File System
After Bonus20reais_PDF.vbe downloads the three files (its update and two additional modules), these are executed, after the system reboots, in the following way:
- Part.jpg: Executes during startup to uninstall the antivirus. Programmed in Borland Delphi. Not packed.
- Mod1.jpg: Executes as soon as a user logs in the infected computer. Programmed in Borland Delphi. Not packed.
- Up.jpg: Executes immediately after its download rundll32.exe. Programmed in Microsoft Visual C++. Not packed.
· Observed Behavior
The jobs created by the script were observed on the task scheduler. When the image was taken, tasks 1 and 2, which download files part.jpg and mod.jpg respectively, were active.
The existence and content of the environment variables %uplkvariable% y %upvariable% was also checked. The first contained the URL to download the file up.jpg. And the second had a random numeric value used to name the file up.jpg once it’s downloaded. The file up.jpg seems to be an update of this banking trojan.
On the folder C:\Windows the files idx and <computer_name>_Part.rri, created by the malware, could be observed; as well as two files BIT*.tmp generated temporarily by bitsadmin during the download of part.jpg and mod.jpg. The file mod1.jpg is the payload, a variant of the ChePro family that steals sensitive data when the user accesses one the banking websites that the trojan monitors. On the other hand, the file part.jpg is actually the tool Partizan, mentioned before, that obtains the names of the programs it must delete from the file with extension “rri”. In this case, such file contained the path of the executables related to Windows Defender, which was the only anti-malware software installed on the computer.
In fact, some strings related to Partizan can be observed on the network traffic during the download of the file.
After checking the rules of the firewall for inbound and outbound traffic, we observed that there were no rules created for the security plugins, only for the Windows Defender executables.
After some minutes, the computer was rebooted. During the system startup, Partizan was executed, as it was specified on the task scheduler.
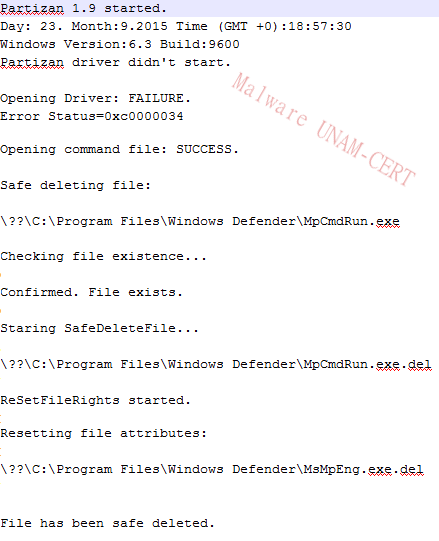
As observed on the following image, Partizan leaves a text file that contains a log of its execution.
Where it is specified whether a file is deleted or not. By looking at the creation dates, it can be inferred that the files are not really deleted, but its extension gets changed, adding “.del” at the end of the name.
· Up.jpg / <número>.tmp
The file up.jpg, which seems to be an update of the analyzed Trojan, includes another URL to download mod1.jpg and other command to add the executables and DLLs of GbPlugin and Warsaw to the Windows firewall, possibly to correct the commands that failed on the original script.
· Mod1.jpg / <Nombre_Equipo>.tmp
Some commands in plain text, strings related to Brazilian banks coded in base64 and ciphered strings were found in the file mod1.jpg. Amongst the plain text strings there’s one that seems to have the necessary data to make the infected computer connect to the database of a remote server, as well as what seems to be the commands of a bot in portuguese: “Provider=SQLOLEDB.1;Password= ;Persist Security Info=True;User ID=conectwebm1;Initial Catalog=conectwebm1;Data Source=”.
Plain Text
- cmd.exe /c taskkill /IM explorer.exe /F &&%systemroot%\explorer.exe
- Provider=SQLOLEDB.1;Password=
- ;Persist Security Info=True;User ID=conectwebm1;Initial Catalog=conectwebm1;Data Source=
- Internet Explorer
- #32770
- Mensagem da p
- gina da web
- @idcliente
- @casa
- @pcname
- @versao
- spcadnovainfo
- @objeto
- @comando
- @resposta
- @param
- spprincipal
- spresposta
Base64
- YWliHd9H8 = ancosantan
- MzBob3Jhcw== = 30horas
- bmNvYnJhZGVzYw== =ncobradesc
- ZXJuZXRiYW5raW5n =ernetbanking
- dGJhbmtpbmdjYWl4 = tbankingcaix
- W2JiLmNvbS5i = [bb.com.b
- YmFuY29icmFz = bancobras
- Z2JmdGJidC5kbGw= =gbftbbt.dll Utilizado por Banco do Brasil
- Z2JwaW5qLmRsbA== =gbpinj.dll
- ZGJzcTAwMTUud2hzZXJ2aWRvci5jb20= =dbsq0015.whservidor.com
Hashes
mod1.jpg: 691e85c70eb994d5ce556cfd88d463d6
part.jpg: d5915a4c454e50d76b343019d9978373
up.jpg: 692eedb2b519b86f9d5a1e4a85b7b606
Bonus20reais.vbe: 6396334d7c2dd955f70c20f73f434ee1