Backdoor on GNU/Linux
The Computer Emergency Response Team UNAM-CERT, received a report about a possible malicious executable file for GNU/Linux operating systems.
While it’s well known that exists a plenty of malware for Windows operating systems, users should not rule out the development of malware for GNU/Linux and Mac OS operating systems, which, even thought in lower degree, are not exempt to this type of threats.
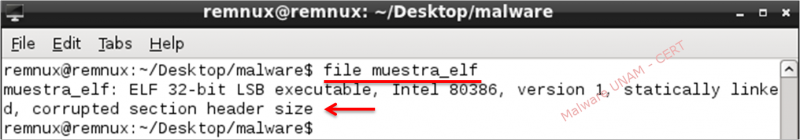
When using “file” command to identify what kind of file the sample is, the command throws up that the sample was an ELF file type. The“Executable and Linking Format” file type, is a format for executable files used on UNIX systems (Linux, BSD, Solaris, etc.).
As a result of executing “file” command, also shows information of being a 32 bits executable file and it is specified that the way of memory storage is “little-endian” type. Also, the file was compiled for Intel 80386 platforms. Finally it shows that it’s “statically-linked” and that a problem exists with “section header” size.
In the string analysis, it’s easy to find “UPX” word, which means that the sample is probably packed with a tool with the same name.

UPX is one of many packers that malicious software developers use frequently to protect their executable files. If the author used a generic version of UPX to protect their samples, it is possible unpack using the same tool trough the command “upx -d”.
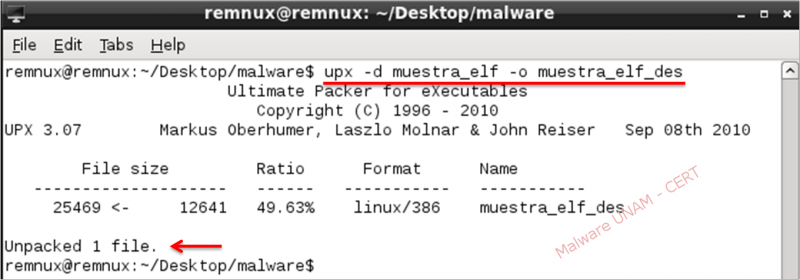
While using again “file” command to verify the file type of the new sample, there are some important changes: the new sample is dynamically linked, the “section header” problem has gone, and it shows that the sections and symbols of depuration were not eliminated with “strip” tool.
With the presence of the sections and the symbols of depuration of the executable file, some important information could be extracted in a more detailed string analysis. Often the authors of malicious software, use “strip” command to make harder the job of the malware analyst.
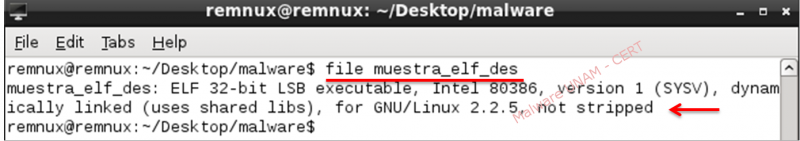
On the string analysis made to the unpackaged sample, information about an Apache web server 1.3.22 that uses 8008 port is shown.
In the list generated by "ldd" utility about libraries needed to run the program, is “libpthread.so.0” that is particularly suspicious about the possible thread management in malware activity.
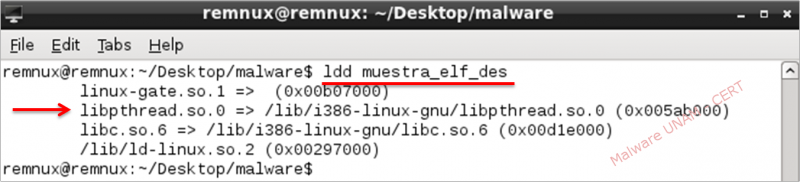
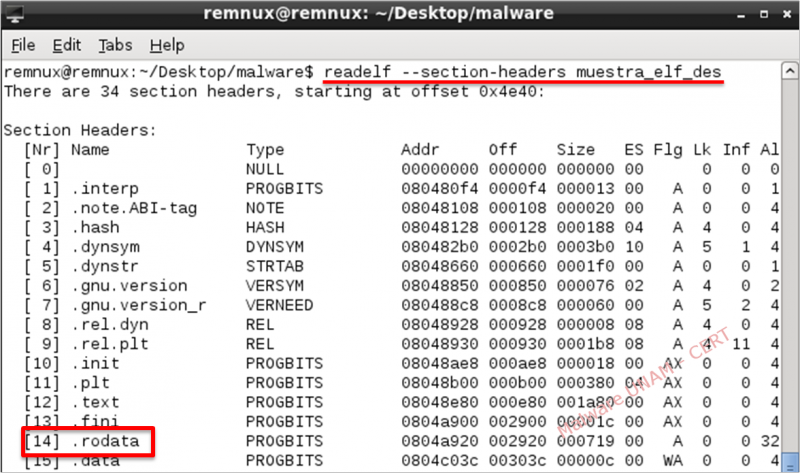
The type ELF file contains sections that can be listed using the "readelf" later to be inspected.
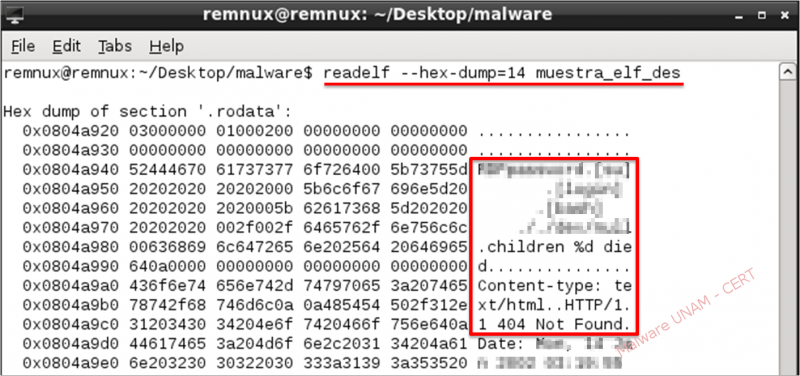
When performing the dump of section 14 which is "read-only data", it can be corroborated the strings displayed by the command "strings".
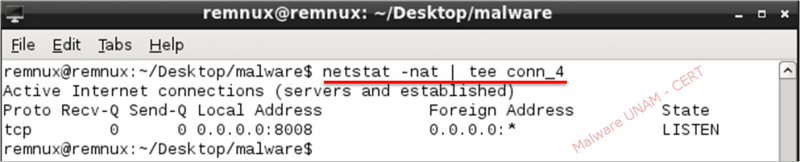
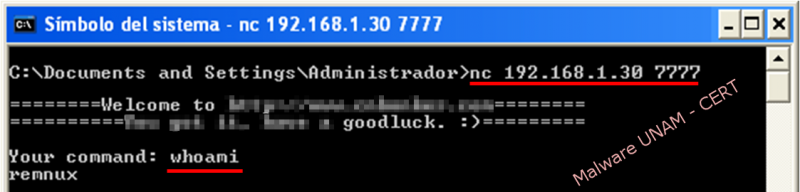
After performing the static analysis, UNAM-CERT malware analysts proceeded to carry out the execution in a controlled environment. As network activity, the malware opens local port 8008 in listening mode.
Both locally and remotely, malware returns a custom terminal with a welcome message for the attacker, where it can be executed commands for further malicious actions.

Due to dynamism in vectors of infection with different operating systems for PCs and mobile, UNAM-CERT strongly recommends to all users to protect their equipment with any antivirus solution and maintain their operating system and applications up to date.